This paper proposes a bio-inspired clustering algorithm based on the bacteria foraging optimization (BFO) approach to enhance the energy efficiency and network lifetime of wireless sensor networks (WSNs). It discusses various routing protocols, issues related to deployment, energy consumption, and optimal clustering strategies to improve signal strength and reduce data loss. The results from simulations indicate that the BFO algorithm performs better than traditional clustering methods like LEACH and K-means in terms of energy dissipation and overall network performance.
![9 ICRTEDC -2014
IJEEE, Vol. 1, Spl. Issue 2 (May, 2014) e-ISSN: 1694-2310 | p-ISSN: 1694-2426
EFFECTIVE AND SECURE DATA GV/ICRTEDC/02
COMMUNICATION IN WSNs
CONSIDERING TRANSFER MODULE
OF NODES
1
Dr. Dinesh Arora, 2
Dr.Hardeep Singh
1
Gurukul Vidyapeeth Institute of Engg. & Technology, Banur, Punjab, India
2
Indo Global College of Engg. & Technology, Mohali, Punjab, India
1
drdinesh169@gmail.com, 2
hardeep_saini17@yahoo.co.in
ABSTRACT: Wireless network which allows users to
access information and service regardless of their
geographic position. These networks are highly distributed
networks of small wireless nodes, monitors the
environment or system by measuring physical parameters
such as temperature, pressure. A network consists of
numbers of nodes with one as a source and one as a
destination. Data loss, high energy consumption, reduction
in signal strength and interferences in data were various
factors which incorrupt the transmission in Wireless
sensor networks. A Bio-inspired clustering algorithm
based on BFO has been proposed and investigation on
energy efficient clustering algorithms related to WSNs has
been done in this paper. The contribution of this paper
related to use of Bacteria foraging algorithm firstly for
WSNs for enhancing network lifetime of sensor nodes.
Keywords: Wireless Sensor Network, Sensor Nodes,
Routing in WSNs, BFO;
1. INTRODUCTION
Wireless network which allows users to access
information and service regardless of their geographic
position provides advantage in terms of cost factor,
flexibility, size and power consumption as it can operate in
wide range of environment without the limitation of
physical media when compared with wired technology. In
wireless technology, message can be forwarded over
multiple hops. Wireless networks operate in two basic
modes. These are:
Infrastructure mode (BSS)
Ad-Hoc mode (IBSS)
1.1 Infrastructure mode
In BSS mode, network is connected with central device
called as access point (AP). All other communicating
devices called as clients are connected to each other
through central access point. Clients and access point must
use the same label of an Ethernet jack on the wall called
SSID. Clients and AP uses same SSID to identify the
network. A mobile host interacts with a bridge in the
network (called base station) within its communication
radius. Channel is setup in the access point (AP) and
discovered by clients.
Typical example of infrastructure based wireless networks
includes cellular networks, WI-FI, WI-MAX, satellite
communication, radar etc.
1.2 Ad-Hoc Mode (IBSS)
In Ad-Hoc mode, which also called as Independent Base
Service Set (IBSS), no central access point (AP) is
required. Here all nodes use the same SSID and channel.
Here all nodes can exchange information without the use
of pre-existing fixed network infrastructure. Devices are
free to move in the network without bound to any
agreement to stay connected. It is self-organizing and
adaptive network where each mobile host itself acts as a
router. Ad-Hoc network allows spontaneous formation and
deformation of mobile networks.
2. LITERATURE SURVEY
This section enlightens the earlier work done related to
wireless sensor networks. Literature survey illustrating the
various routing protocols for lifetime enhancement,
throughput paths, best roués and in field of wireless sensor
network security.
B.P.S Sahoo, Satyajit Rath, Deepak Puthal [1]
presented the adaptive approach to find an optimal routing
path from source to sink when the sensor node are
deployed randomly deployed in a restricted service area
with single link. Their analysis shows that the approach
they followed reduces the message communication to find
an optimal routing path. Hence the network consumes less
energy and increase the lifetime of network.
Asar Ali, Zeeshan Akbar [2] evaluate the performance of
two different routing protocols like ad hoc on demand
distance vector (AODV) and dynamic source routing
(DSR) for monitoring of critical conditions with the help
of important matrices like throughput and end to end delay
in different scenarios. Based on result derived from
simulation a conclusion is drawn on the comparison
between these two different routing protocols with
parameter like end-to-end delay and throughput.
Theodore Zahariadis et al [3] present a trust aware,
location based routing protocol which protects the WSN
against routing attacks, and also support large scale
WSN’s deployments. Their proposed solution has been
shown to efficiently detect and avoid malicious nodes and
has been implemented in state-of-the-art sensor nodes for
a real-life test-bed. Their work focused on the assessment
of the implementation cost and on the lessons learned
through the design, implementation and validation
process. The domain of WSNs applications is increasing](https://image.slidesharecdn.com/gvicrtedc02-140714020002-phpapp02/75/EFFECTIVE-AND-SECURE-DATA-COMMUNICATION-IN-WSNs-CONSIDERING-TRANSFER-MODULE-OF-NODES-1-2048.jpg)
![ICRTEDC-2014 10
widely over the last few years. As severely constrained
node resources, limited network resources and the
requirement to operate in an ad hoc manner characterize
this new type of networking, implementing security
functionality to protect against adversary nodes becomes a
challenging task.
Guoxing Zhan et al [4] proposes a fact that multi hope
routing in wireless sensor network offers little protection
against deception through replaying routing information. It
cannot be solved solely by encryption or authentication
techniques. To secure multi-hop routing in WSNs against
intruders exploiting the replay of routing information, we
propose TARF, a trust-aware routing framework for
WSNs.
3. ROUTING IN WSNs
The Wireless networks are highly distributed networks of
small wireless nodes, monitors the environment or system
by measuring physical parameters such as temperature,
pressure. A network consists of numbers of nodes with
one as a source and one as a destination. In a wide area the
number of nodes is not specified.
Here the concentration point is neither routing nor
transmission but deployment which means to distribute
systematically or strategically. In Wireless sensor
networks this arrangement method is called as sensor take
battle station.
These wireless sensor network’s faces numbers of
following problems at the time of communication.
Issue regarding deployment
Issue regarding distance
Issue regarding energy consumption
Issue regarding coverage area
3.1 Bacteria Foraging Optimization in WSNs
Bacterial Foraging Optimization (BFO) is a population-
based numerical optimization algorithm. In recent years,
bacterial foraging behaviour has provided rich source of
solution in many engineering applications and
computational model. It has been applied for solving
practical engineering problems like optimal control,
harmonic estimation, channel equalization etc. In this
paper, BFO has been used for cluster head selection to
provide improved energy efficiency in routing. The
process of cluster head selection involves application of a
clustering algorithm. This has been classically done with
LEACH, K-Means and direct method [6].
4. RESEARCH OBJECTIVE
The aim and objective of our research incorporated in our
paper covers the following steps.
1) Optimum route distance between nodes and
sensors
2) Optimum or least power consumption between
location points and sensors.
3) Maximum Bandwidth utilization.
4) Increase in Sensor Coverage.
5) Optimization of Mean location points of wireless
sensors.
5. PROPOSED STEPS TO ACHIEVE THE
OBJECTIVE
With minimum number of sensor nodes having
maximum coverage in the network and the nodes
are within the communication range.
By making optimized wireless clusters using the
Euclidean distance from all the location nodes to
the Sensor Nodes.
By making the Clusters of the sensor nodes with
a corresponding central transceiver point which
will be further chosen from a group of sensors.
By Optimizing the Sensors position within each
individual cluster, using BFO.
6. PROBLEM FORMULATION
In wireless sensor network data is transmitted through
node to node where distance is the most effecting factor to
the efficiency of the networks. Sensors are to be linked to
many near falling nodes by determining their distances. If
the distance is large than it will result to more energy
consumption and even results to week the signal strength.
If any sensor is linked to large number of nodes to reduce
the coverage area cost, then it will produce delay and leads
to more energy requirement. On other side if the to lower
the deployment cost sensors should be located far from
each other so that they may cover maximum area as well
as maximum numbers of nodes. But this may increase
wireless sensor node power consumption due to the energy
needed to reach large distances. Data loss, high energy
consumption, reduction in signal strength and
interferences in data were various factors which incorrupt
the transmission in Wireless sensor networks.
7. PROMBLEM SOLUTION
For reduction of the challenged faced by the wireless
sensor networks, we need to establish the sensors at a
place where it results to better communication. For this
various factors as distance, coverage area, signal strength,
energy level all has to be determined. There are to two
methods can be used.
Hit & trial method
Iterative optimization
8. SYSTEM DESIGN EVALUATION AND
SIMULATION RESULTS
This section includes results of the proposed algorithm in
terms of various parameters by analyzing the result
visually in network animator and graphically evaluating
the performance of the proposed system in terms of
standard parameters, which discussed later in this chapter.
This section also incorporate the validity of proposed work
by comparing the performance with existing system.
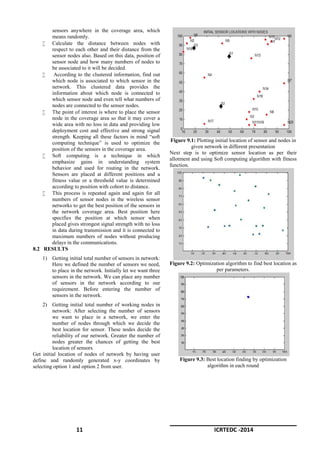
8.1 SIMULATION
Firstly calculate the total number of the users in
the area under the wireless network and also
determine the total numbers of sensors are to be
used in the network for the communication
between the different nodes.
Identify the initial position of all the nodes in the
network with determining the rough positions of](https://image.slidesharecdn.com/gvicrtedc02-140714020002-phpapp02/85/EFFECTIVE-AND-SECURE-DATA-COMMUNICATION-IN-WSNs-CONSIDERING-TRANSFER-MODULE-OF-NODES-2-320.jpg)