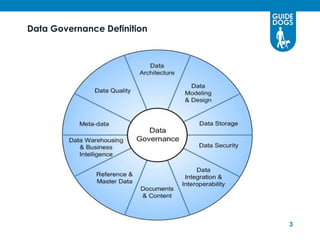
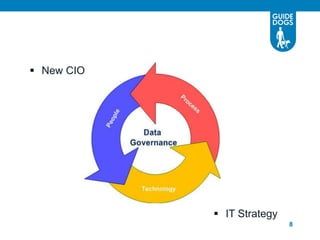
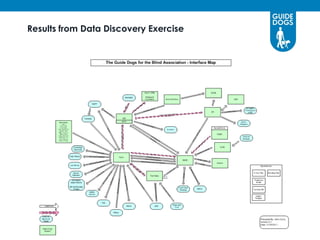
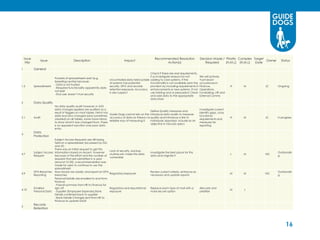
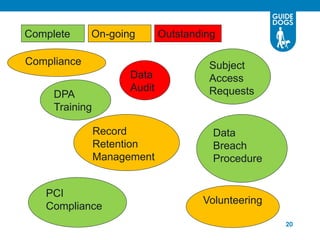
This document discusses data governance at Guide Dogs. It introduces data governance and defines it. It explains why data governance is important due to Guide Dogs' growing programs, systems, and locations. It describes how Guide Dogs is ensuring data is handled compliantly across the organization through a Data Governance Board. The board addresses issues, defines data elements, and agrees on data quality and security requirements. The document outlines where Guide Dogs is in implementing data governance and next steps around a "Data Day," privacy campaigns, and streamlining the board structure.