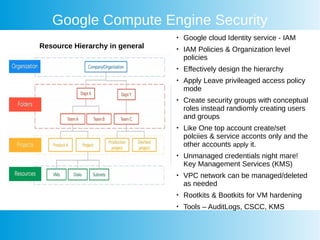
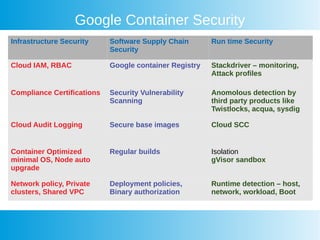
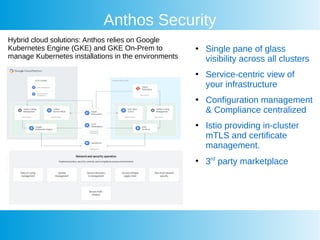
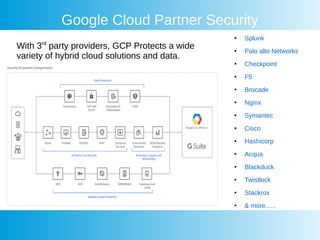
This document provides an overview of Google Cloud's container security features and best practices. It covers key aspects such as IAM policies, workload protection, vulnerability scanning, and components of Google Kubernetes Engine security, including control plane management and node security. Additionally, it highlights integration with third-party security solutions and emphasizes the importance of compliance and security across hybrid cloud environments.