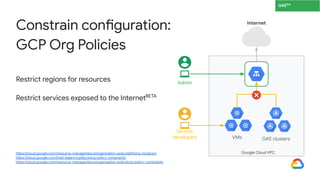
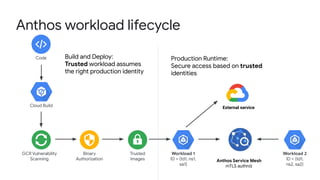
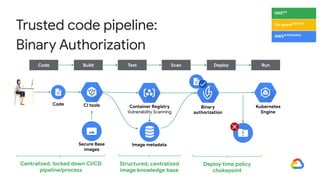
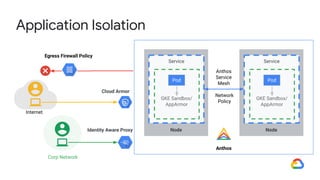
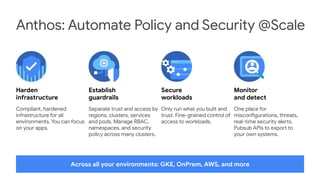
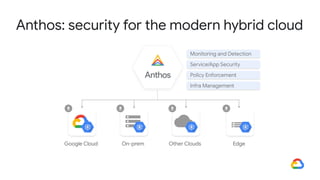
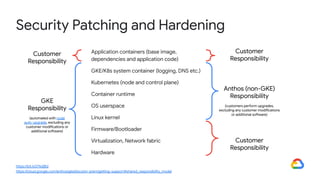
The document discusses the security enhancements provided by Google Cloud Anthos across hybrid and multi-cloud environments, highlighting a four-step workflow for securing applications. It outlines features such as infrastructure hardening, establishing guardrails, and monitoring capabilities available on various platforms including GKE, on-prem, and AWS. Key security practices emphasized include zero trust principles, workload isolation, and compliance with various industry standards, enabling organizations to manage security effectively at scale.











![https://cloud.google.com/anthos-config-management/docs/concepts/policy-controller
metadata:
name: psp-pods-allowed-user-ranges
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Pod"]
parameters:
runAsUser:
rule: MustRunAs
ranges
- min: 100
max: 200
Anthos Policy
Controller
We supply a policy library
E.g. No containers may run as root
Based on Open Policy Agent’s
Gatekeeper
GKEGA
On-premGA
AWSGA](https://image.slidesharecdn.com/anthossecuritymodernizeyoursecuritypostureforcloud-nativeapplications-200905172517/85/Anthos-Security-modernize-your-security-posture-for-cloud-native-applications-15-320.jpg)