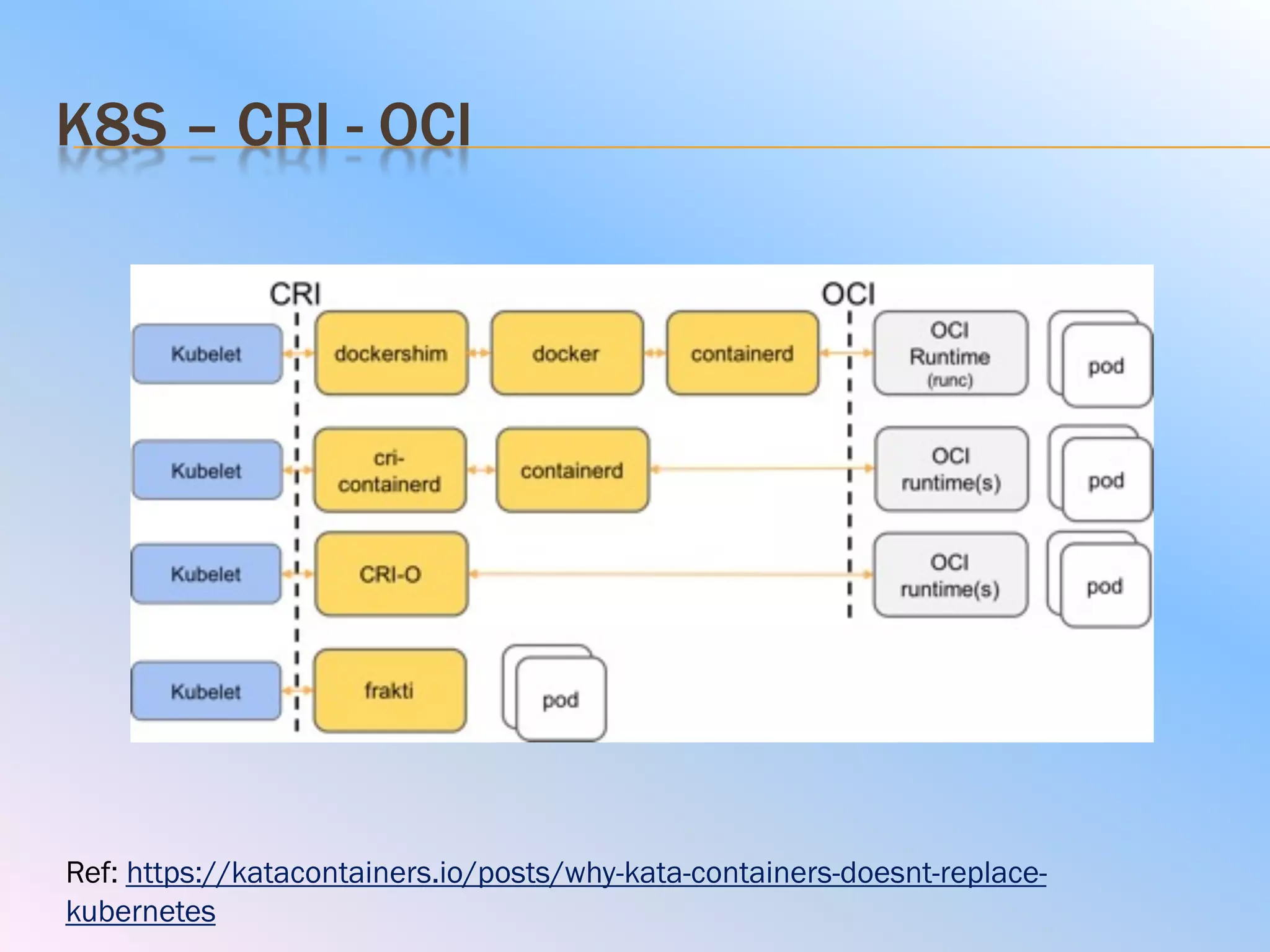
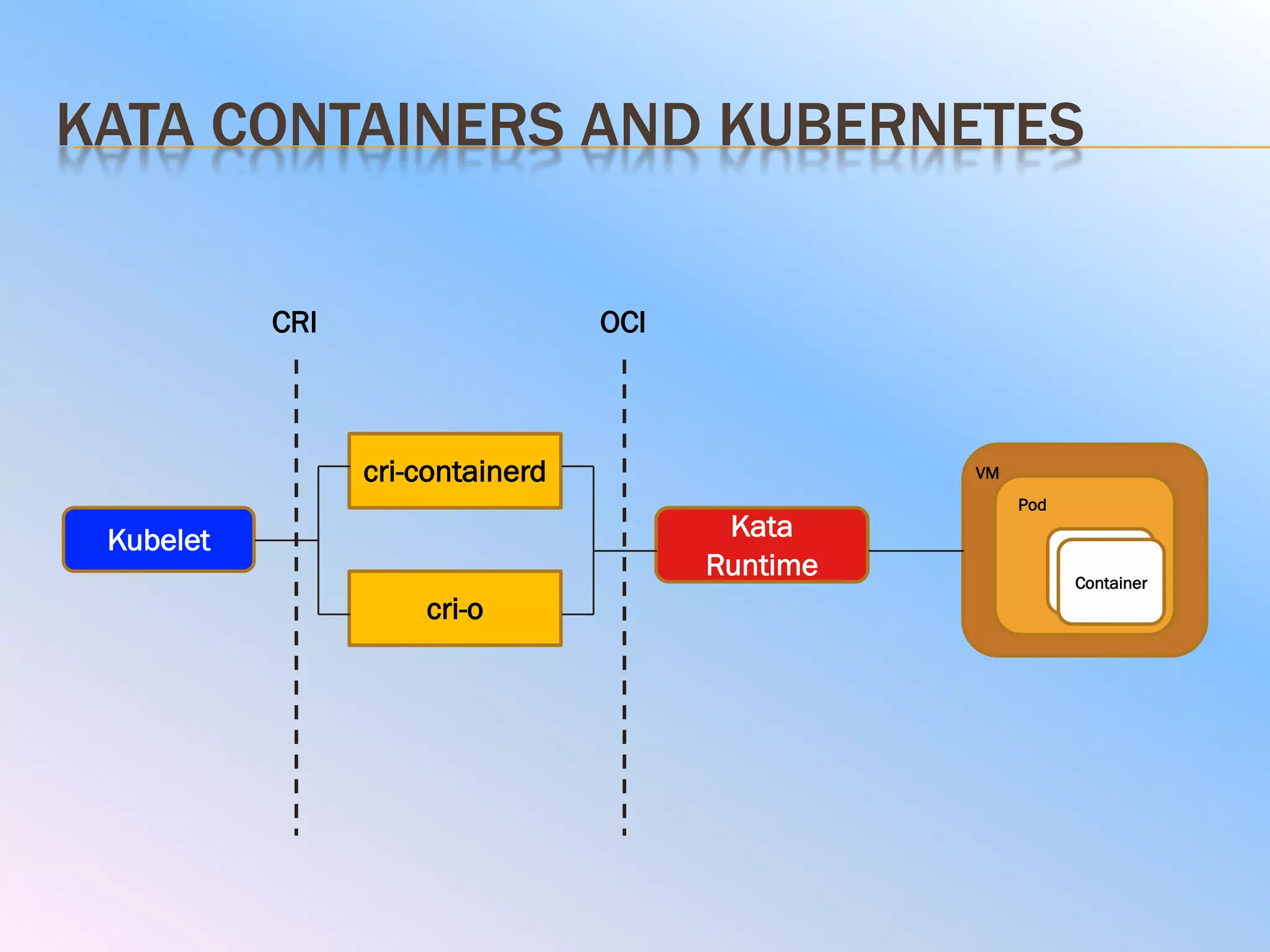
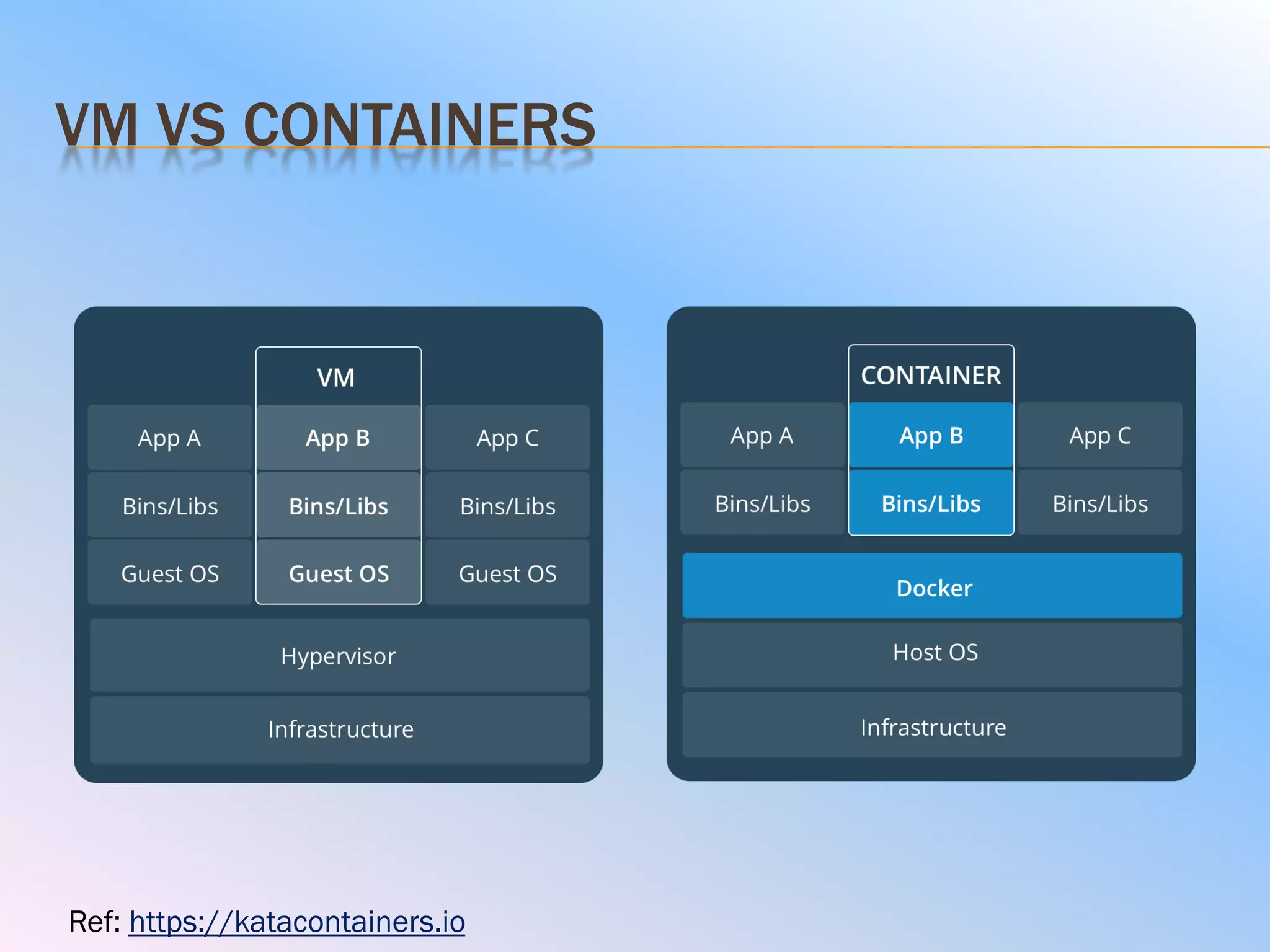
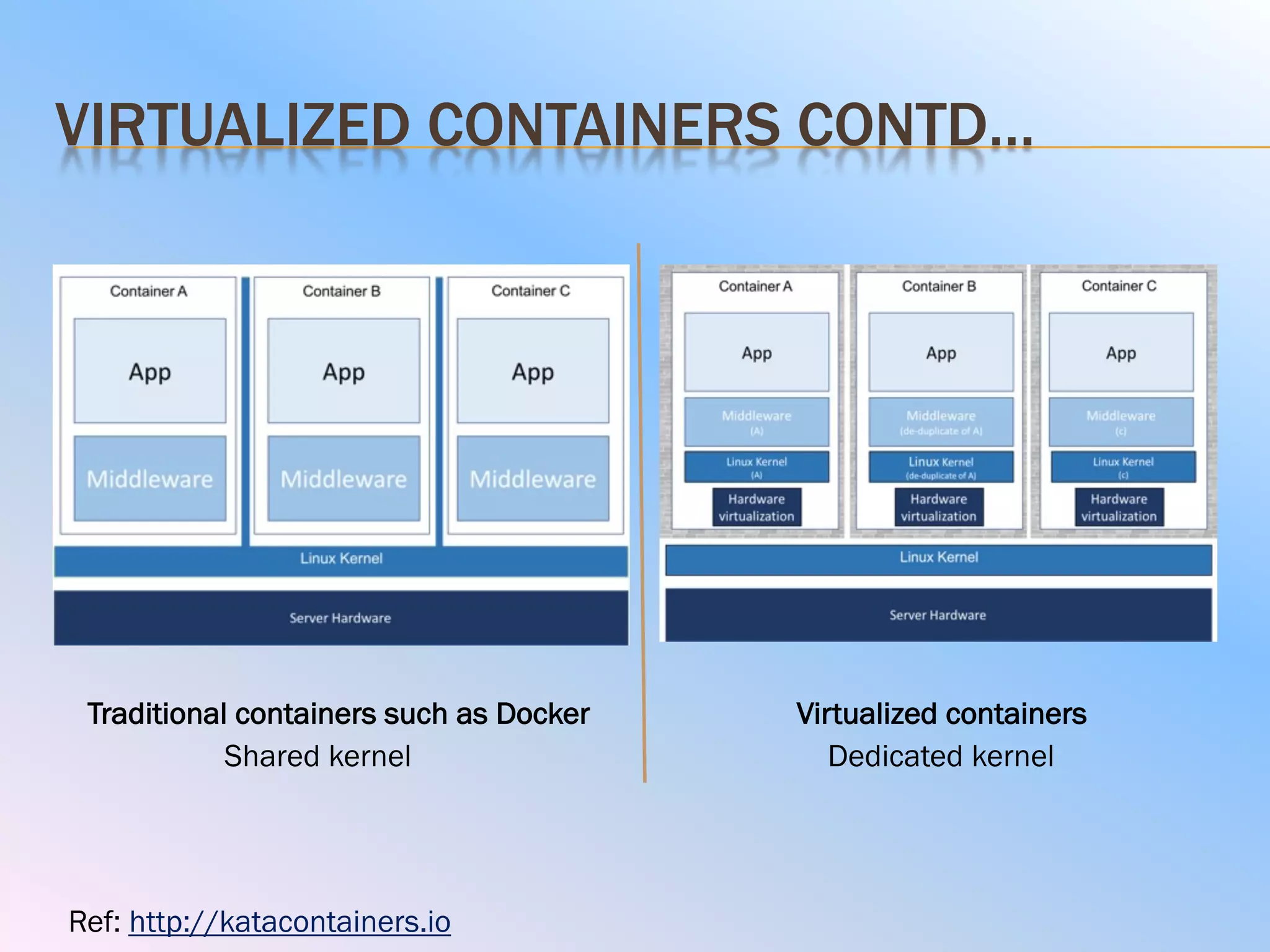
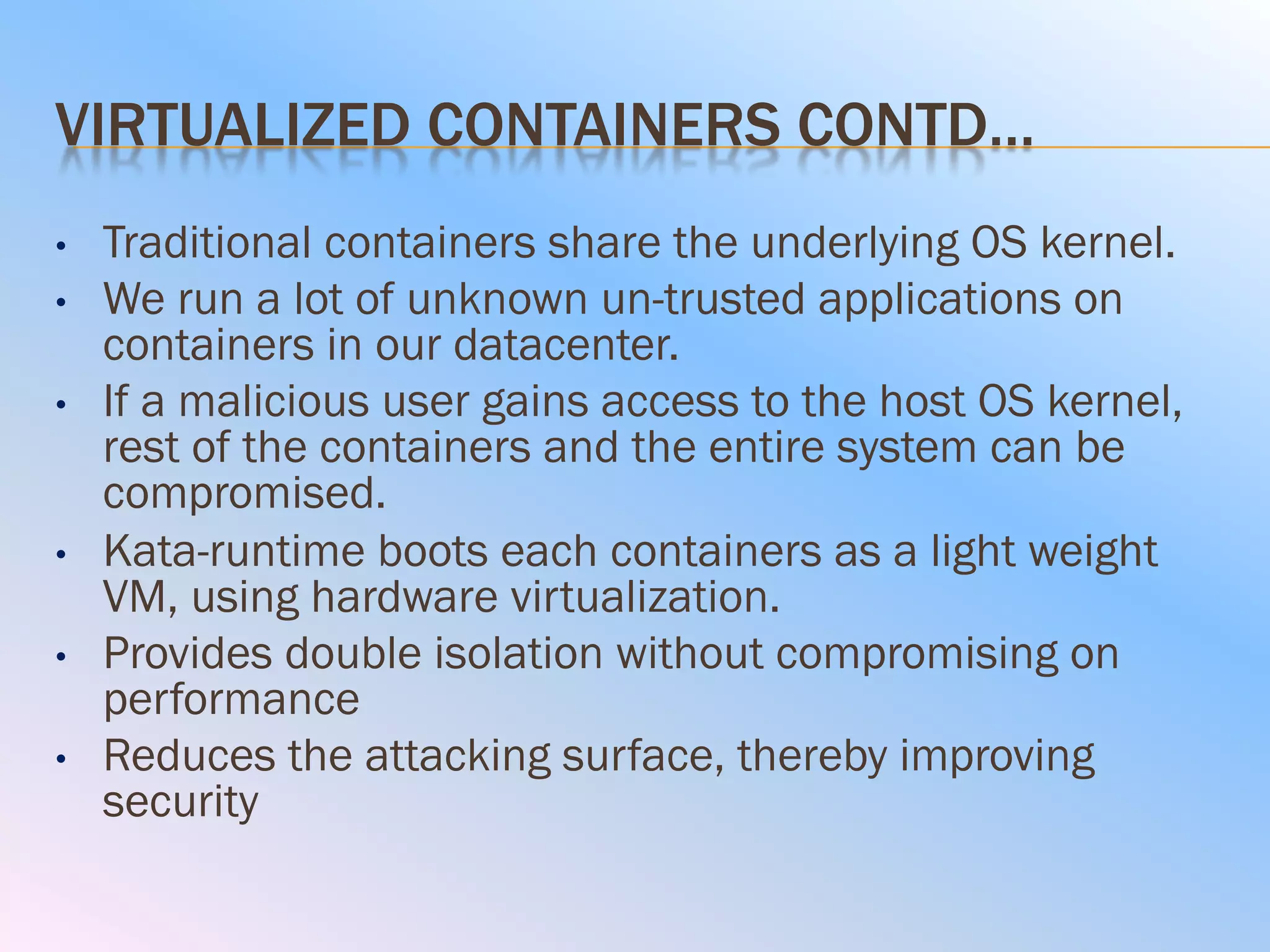
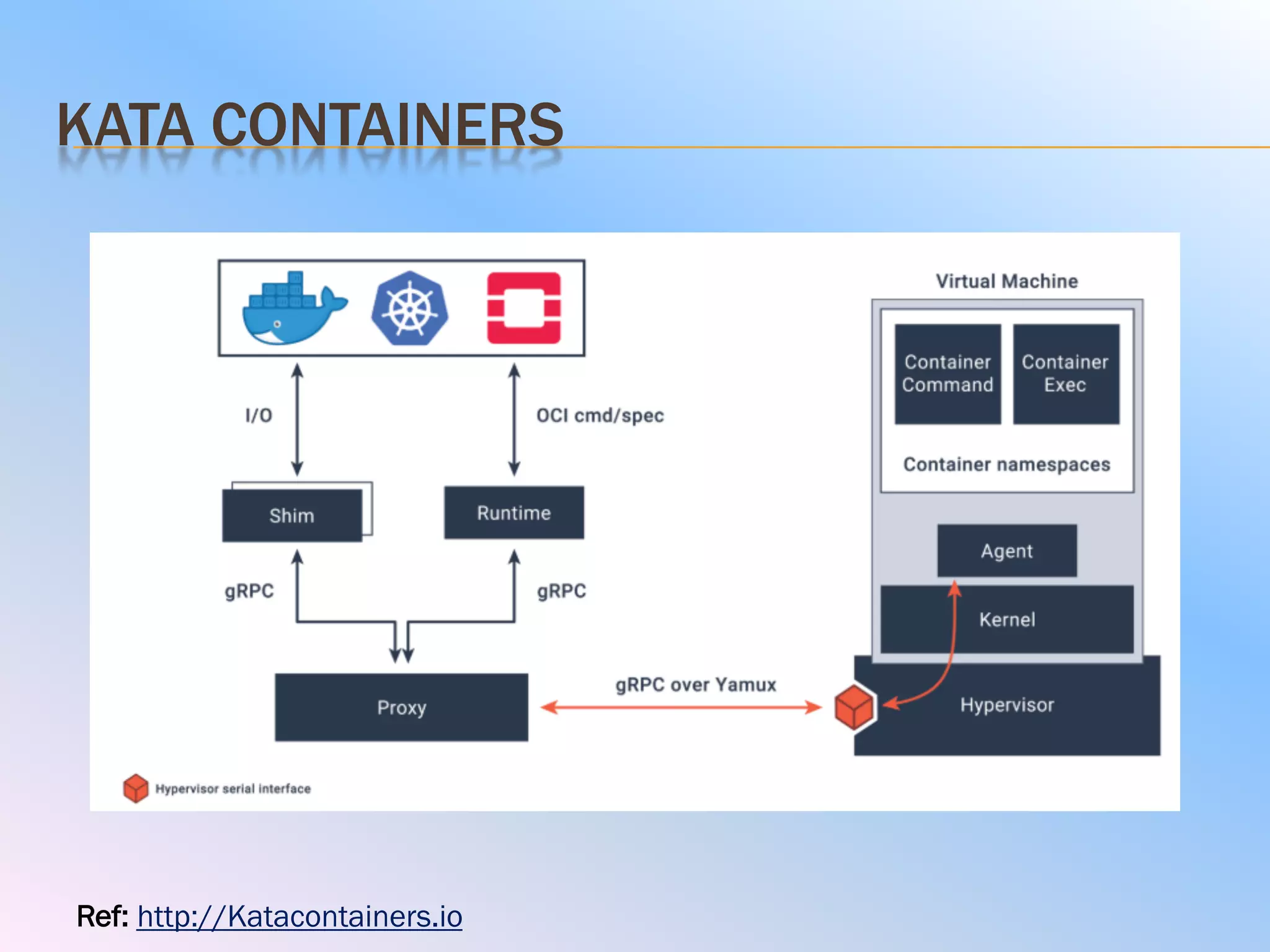
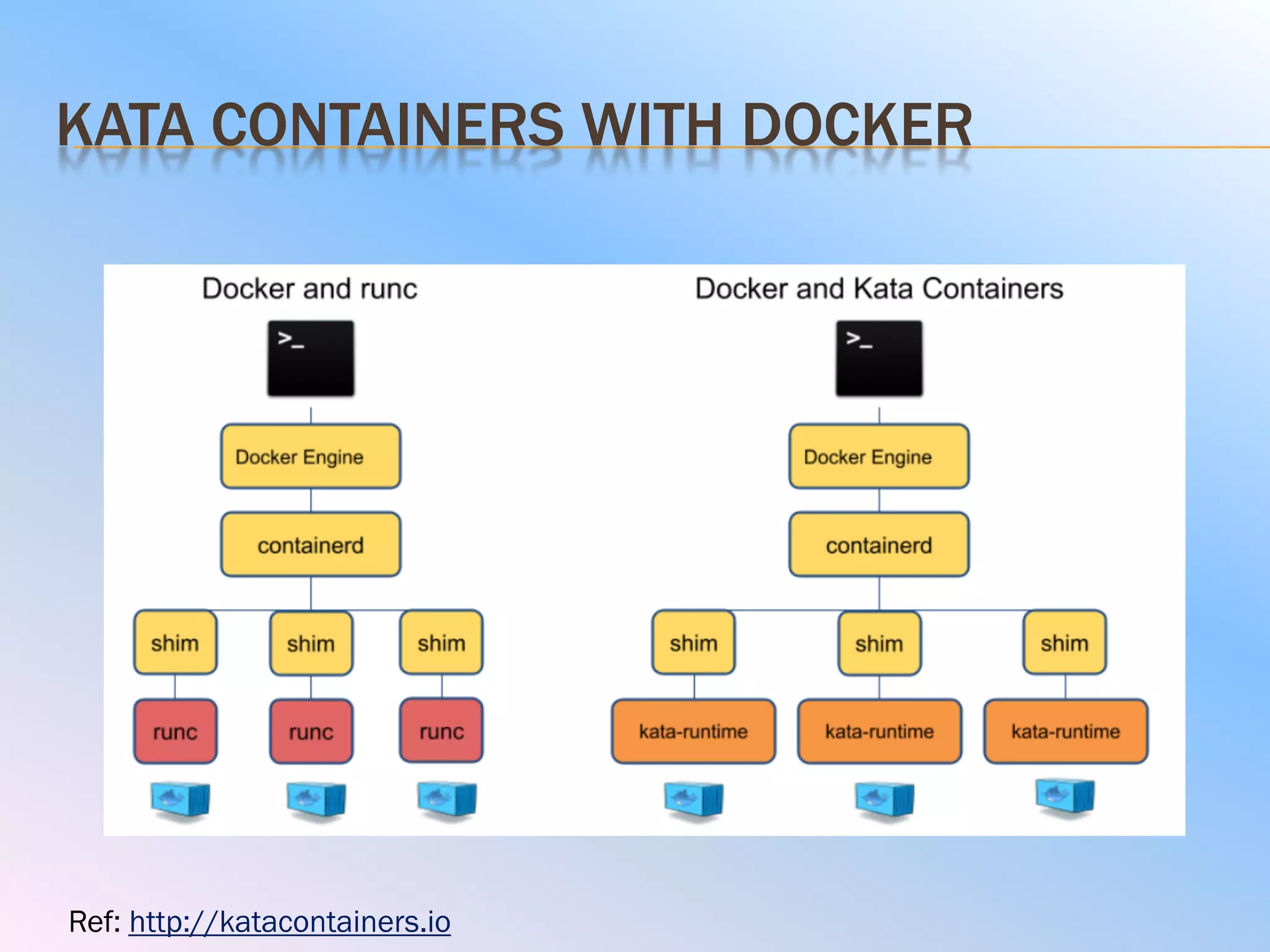
The document discusses the differences between virtual machines (VMs) and containers, highlighting that containers are more lightweight and faster due to shared OS kernels, while VMs are heavier and slower. It introduces kata containers, which enhance security by running each container as a lightweight VM, offering better isolation and reducing vulnerabilities. Additionally, it emphasizes that kata containers complement existing technologies like Docker and Kubernetes rather than replacing them.




![CONFIGURATION STEPS
• Enable virtualization (Intel VT / AMD-V) on the docker host
• Create a config file inside docker.service.d
• Restart docker
• Spin up kata containers using docker run command and docker images
[root@tt2aio docker-host]# cd /etc/systemd/system/docker.service.d
[root@tt2aio docker-host]# cat <<EOF | sudo tee kata-containers.conf
[Service]
ExecStart=
ExecStart=/usr/bin/dockerd -D --add-runtime kata-
runtime=/usr/bin/kata-runtime --default-runtime=kata-runtime
EOF
[root@tt2aio docker-host]# systemctl daemon-reload
[root@tt2aio docker-host]# systemctl restart docker](https://image.slidesharecdn.com/virtualizedcontainers-howgoodisit-ananth-siemens-cc18-180806081647/75/Virtualized-Containers-How-Good-is-it-Ananth-Siemens-CC18-12-2048.jpg)