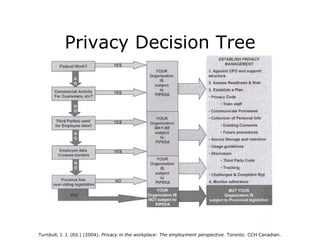
The document discusses workplace privacy issues in Canada including relevant legislation and case studies of public libraries. It covers the Freedom of Information and Protection of Privacy Act (FIPPA) and Municipal Freedom of Information and Protection of Privacy Act (MFIPPA) which establish rules for government organizations regarding personal information. Case studies examine privacy policies at the County of Brant Public Library and Toronto Public Library. Current issues addressed include electronic privacy, employer monitoring, and disclosing personal information to employers.