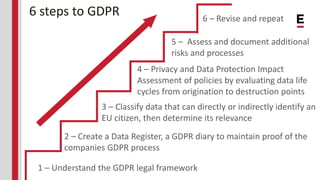
The General Data Protection Regulation (GDPR) aims to protect the personal data and privacy of EU citizens, imposing strict compliance requirements on companies by May 2018. It grants rights to individuals, including access to their data and the right to be forgotten, and mandates specific data handling practices for personal information. Non-compliance can result in significant penalties, highlighting the importance for businesses to ensure they meet GDPR standards.