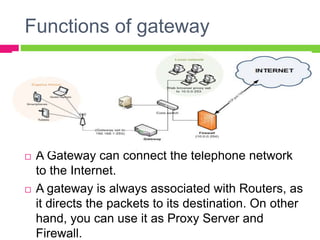
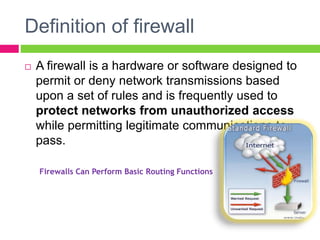
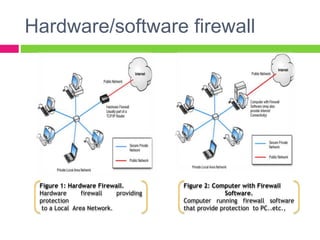
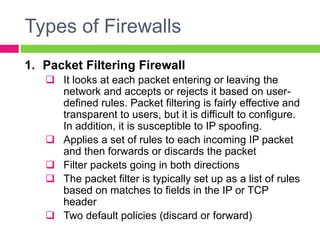
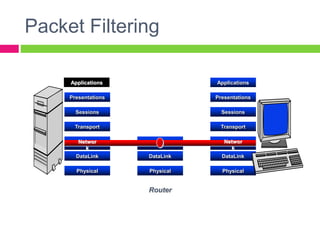
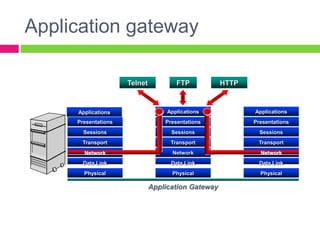
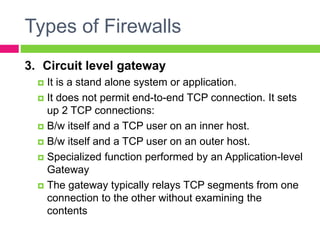
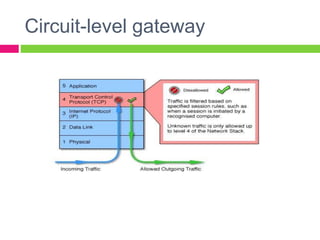
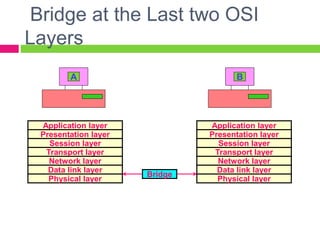
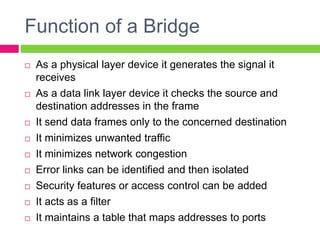
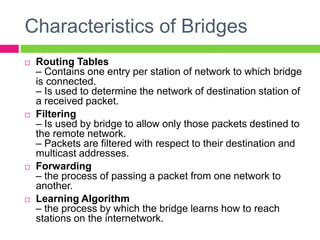
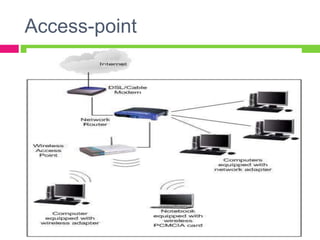
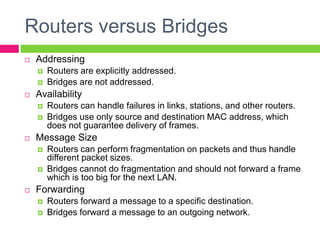
A gateway connects two networks that use different protocols. It routes traffic between different networks, such as between a home or enterprise network and the internet. A firewall protects networks from unauthorized access by allowing or blocking network transmissions based on a set of rules. It can inspect traffic at the application and packet levels. A bridge connects two portions of a network at the data link layer. It filters traffic to send frames only to the concerned destination network to minimize congestion.