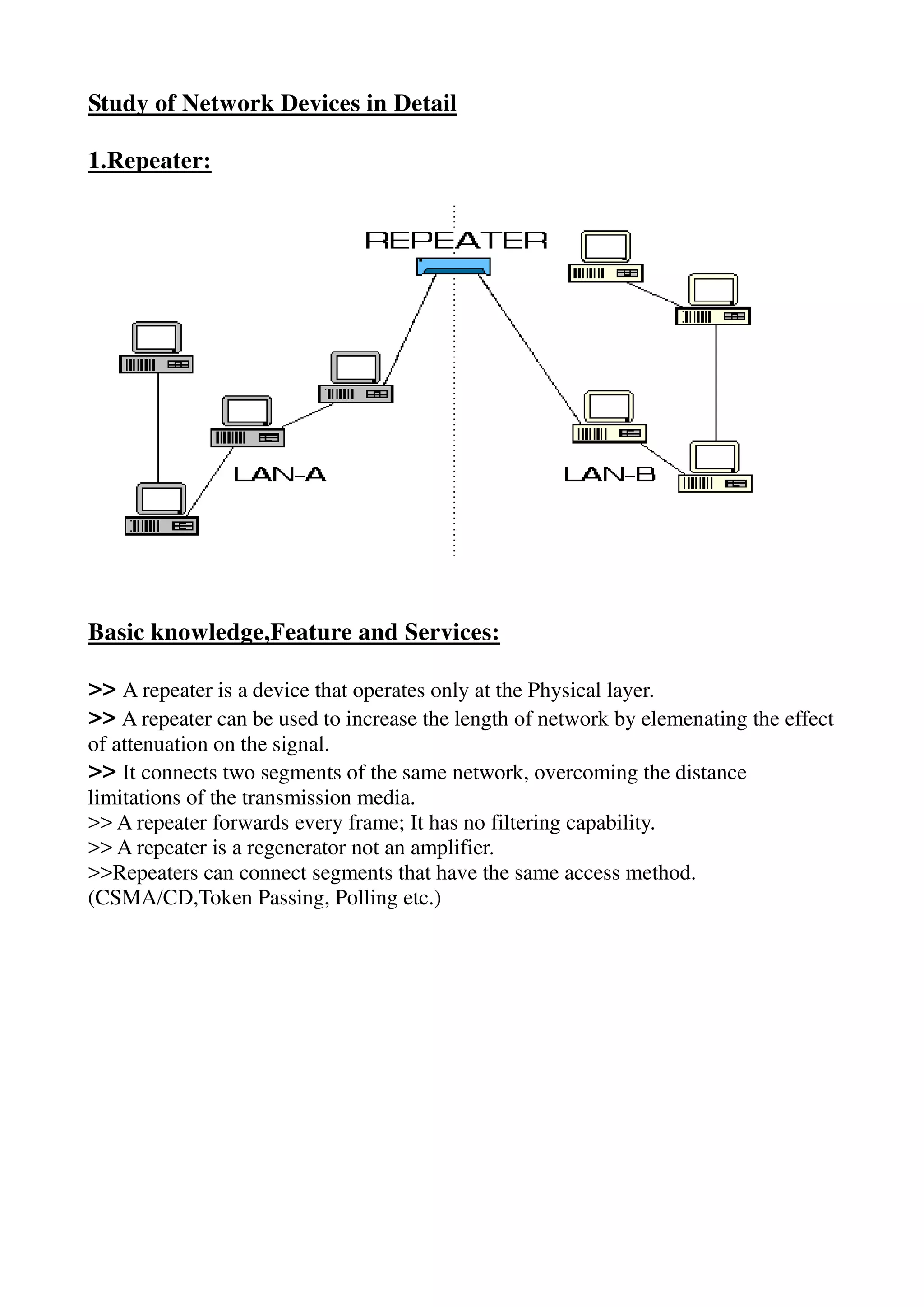
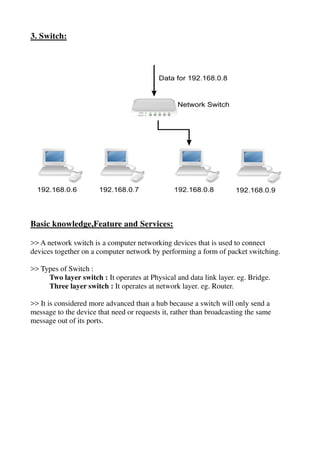
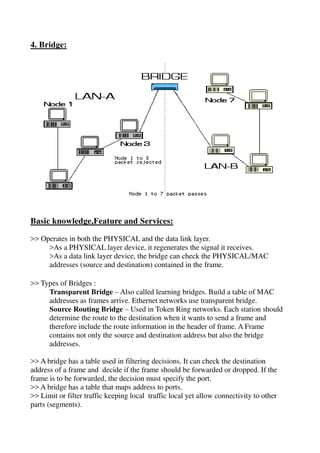
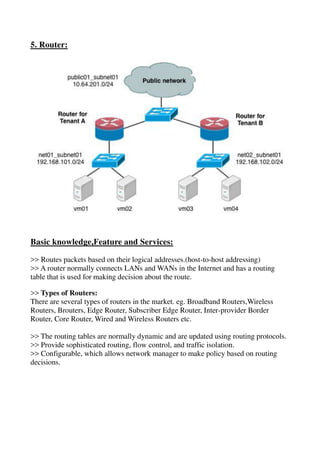
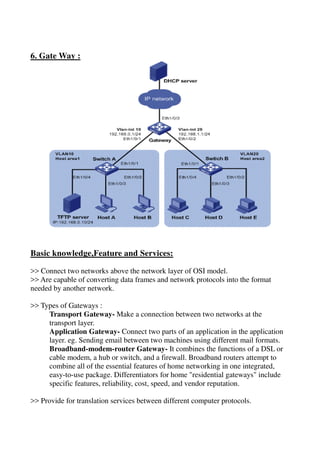
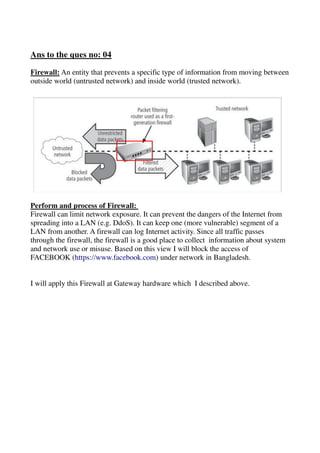
The document provides a detailed study of various network devices, including repeaters, hubs, switches, bridges, routers, and gateways, along with their functions and characteristics. It explains how these devices operate at different layers of the OSI model and their roles in enhancing network performance and connectivity. Additionally, it discusses the role of firewalls in managing network security and controlling traffic flow.