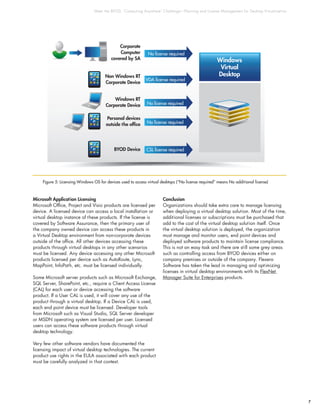
This document discusses the challenges of managing software licenses in virtual desktop environments. It explains that capturing accurate inventory and usage data is difficult for virtual desktops, especially session-based ones. It also outlines Microsoft's licensing rules for Windows and applications in virtual desktop scenarios. Organizations must carefully analyze each software vendor's product use rights to ensure license compliance when using virtual desktop technologies.

![Meet the BYOD, ‘Computing Anywhere’ Challenge—Planning and License Management for Desktop Virtualization
3
As of today, desktop virtualization represents only a few
percent of all desktops. However, it is still seen as one of
the leading technologies that should take a more significant
portion of the market in the coming years. One of the
drivers fueling these forecasts is the rapid adoption of
mobile devices and Bring Your Own Device (BYOD) policies
by organizations. For these devices, the virtual desktop
offers end users the flexibility to access their business
environment from anywhere, at any time, from almost any
device, running any operating system.
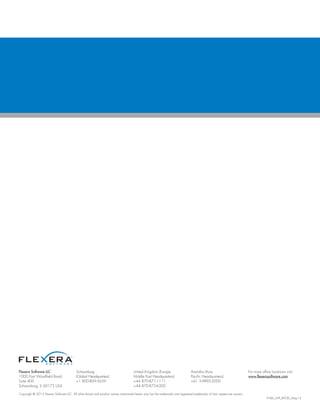
The drivers for desktop virtualization, as shown in Figure
2, also include providing the ability for IT to centralize and
simplify desktop management and accelerate provisioning
of new desktops. In addition, this technology meets
most organizations’ security, compliance and regulatory
requirements as data and applications are kept securely in
the datacenter.
Figure 2: Drivers for Desktop Virtualization [Source: TechWeb]
Drivers for Desktop Virtualization
(Organizations rating benefits of desktop virtualization “quite or very important”)
Percentages based on a 4 or 5 rating on a scale of 1 to 5, where 5 is “very important.”
Base: 300 respondents who have implemented, are piloting or planning to roll out desktop virtualization in the next year.
Data: TechWeb survey of 490 IT decision makers.
To centralize and simplify
desktop management
74.8%
74.2%
73.0%
67.5%
65.7%
62.7%
To improve security by maintaining
and backing up data centrally
To simplify and accelerate
provisioning new desktops
To lower infrastructure costs in power
usage and/or hardware acquisition
To provide end users with a convenient way to
access their desktop environments remotely
To extend refresh cycles
for desktop PCs
To reduce downtime caused by
server/client hardware failure
86.2%](https://image.slidesharecdn.com/fnmwpbyodmay13-140411115547-phpapp02/85/Meet-the-BYOD-Computing-Anywhere-Challenge-Planning-and-License-Management-for-Desktop-Virtualization-3-320.jpg)
![Meet the BYOD, ‘Computing Anywhere’ Challenge—Planning and License Management for Desktop Virtualization
4
Types of Virtual Desktops
Virtual desktops come in two flavors: persistent and session
based (or non-persistent). A persistent virtual machine is
a virtual machine that is kept on a disk in the datacenter.
Each time the user logs in, the previous session on that
virtual machine is resumed. A user can create shortcuts,
customize or install additional applications on his or her
virtual desktop and all of these changes will be available
in future sessions. Persistent virtual machines are usually
only assigned to power users or administrators as they
consume a large amount of resources—such as storage, in
the datacenter.
The most common virtual desktops are session based. A
session based virtual machine is assigned from a pool
of virtual machines to the end user at log in time and
wiped out each time the user logs out. Some vendors offer
technical solutions to keep user changes across sessions and
can even add applications to the virtual desktop template
based on the user profile. In these instances, when the user
logs in, the user personalization is added to the virtual
desktop template.
Collecting Virtual Desktop Inventory
In the traditional desktop world, inventory is performed by
an agent running within the operating system. Inventory
consists of capturing software package data, for instance
in Windows environments—from Programs and Features,
file data, including contents of specific files, Windows
registry or ISO 19770-2 tags. From there, data scrubbing
and analysis is performed by an application recognition
tool to generate the list of commercial products requiring
a license. Additionally, a review of the login history on
the device provides clues about its primary user. Typical
inventory tools run on a schedule or are executed at log on
time. Scheduling is the most commonly used strategy as it
is less intrusive: it does not slow down the execution of the
operating system when the end user requests access to it.
It takes a few minutes for an inventory tool to capture
data, the most resource intensive task being to perform
a disk scan for executables, dlls, ISO 19770-2 tags or
specific files.
For persistent virtual desktops, inventory tools are able to
capture inventory and usage data the same way as for
traditional desktops. On the other hand, session based
virtual desktops are challenging for many reasons: there is
no practical way to run the inventory on a schedule as the
machine is wiped out every time the user logs out and this
may happen multiple times a day. The lifespan of a virtual
desktop can be extremely short, not leaving enough time
for a scheduled or session triggered inventory to complete
successfully. Inventory tools identify operating system
instances by using various techniques: from analyzing key
hardware or software properties (serial number, MAC
address, IP address…) or by assigning a unique identifier
to each one. A session based virtual desktop gets reused
across multiple users or is re-imaged after use. So, it’s
difficult to get a unique inventory for each session. This can
result in an ever growing, large number of devices that will
need to be reconciled. An alternative approach is to set-up
a mechanism to group sessions together on a per user basis.
In the virtual desktop environment, templates of virtual
machines are created and assigned to users. When a
user accesses a session based virtual desktop, a new
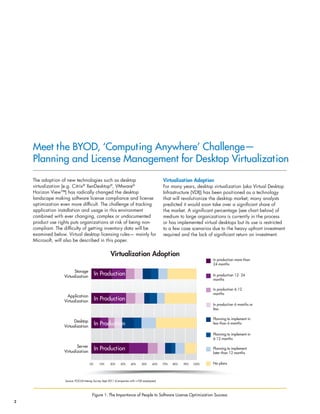
Figure 3: Desktop Virtualization Architecture [Source: FOCUS LLC www.focusonsystems.com ]
VirtualDesktops(VMs)
Server Hosted
Virtual Desktop Infrastructure
User Access Devices
PC
Laptop
Thin Client
Server
Tablet/phone
Hypervisor
Guest OS
APP 1 APP 2 •••
Guest OS
APP 1 APP 2 •••
Guest OS
APP 1 APP 2 •••](https://image.slidesharecdn.com/fnmwpbyodmay13-140411115547-phpapp02/85/Meet-the-BYOD-Computing-Anywhere-Challenge-Planning-and-License-Management-for-Desktop-Virtualization-4-320.jpg)