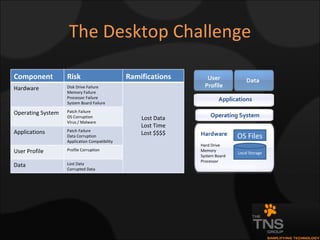
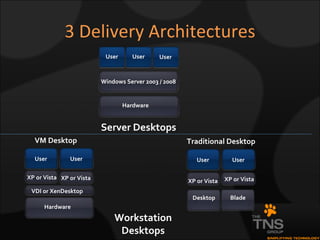
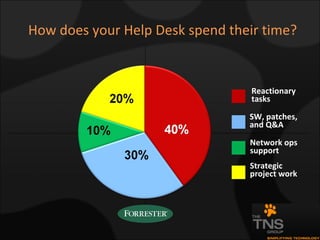
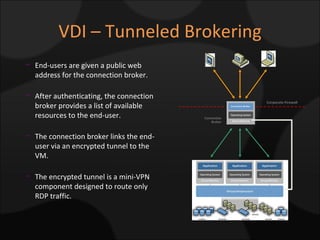
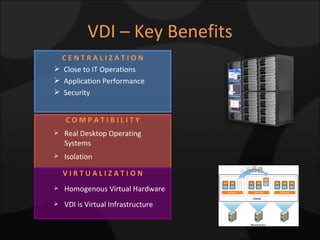
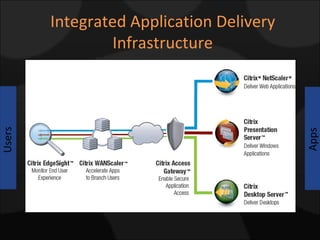
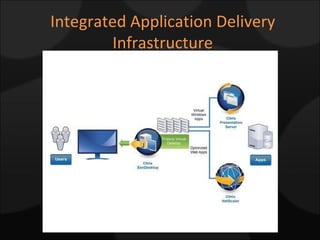
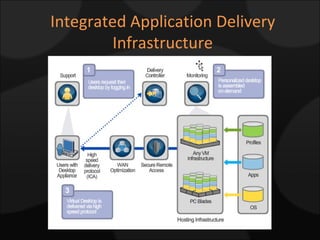
The document compares and contrasts XenDesktop and VMware VDI for virtual desktop solutions. It discusses how virtual desktop technology allows centralized management and standardization of desktop images. It also covers the benefits of virtual desktops such as reducing costs, improving security and flexibility, and enhancing productivity compared to traditional desktop management approaches.