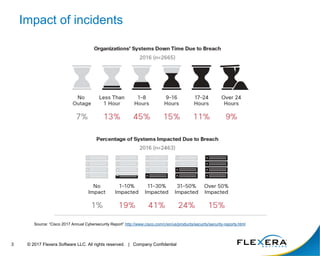
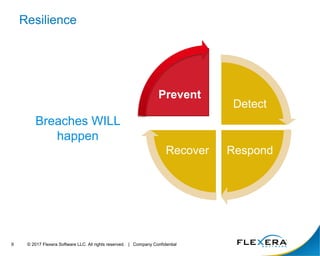
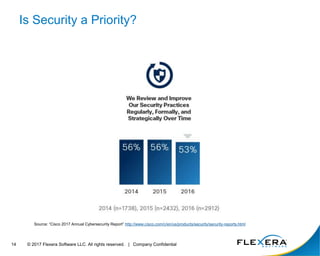
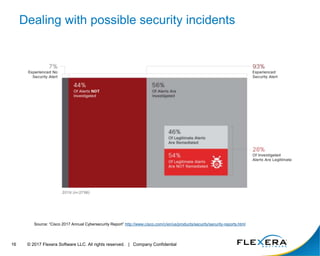
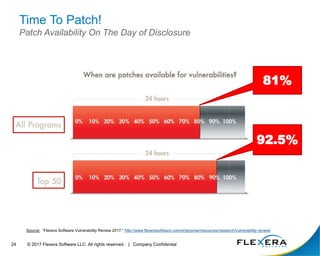
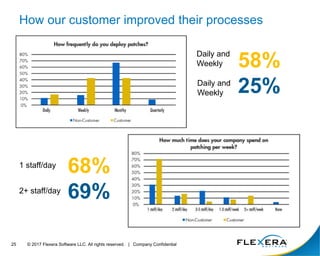
The document discusses the critical importance of cybersecurity in managing software, highlighting the escalating costs and consequences of security incidents and data breaches. It outlines various roles and responsibilities within organizations, including information security, IT security, desktop management, and software asset management, each aimed at reducing vulnerabilities and enhancing security operations. The conclusion emphasizes the need for an integrated approach to operationalize people, processes, and technology to effectively mitigate cyber threats.