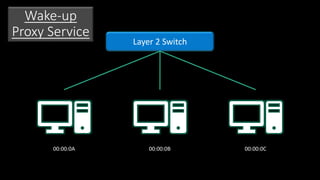
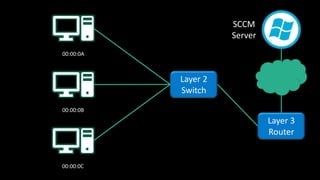
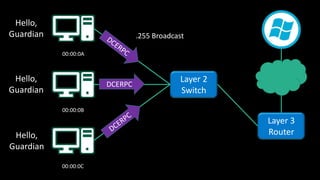
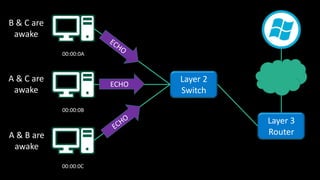
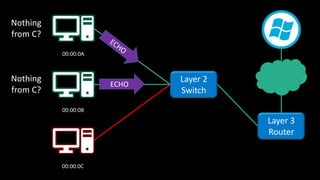
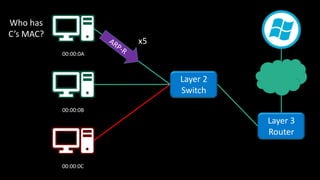
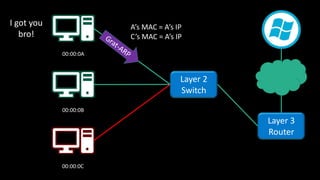
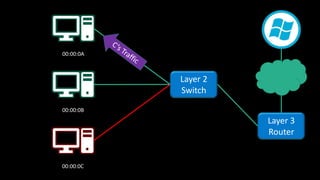
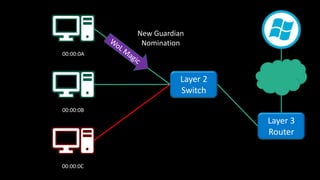
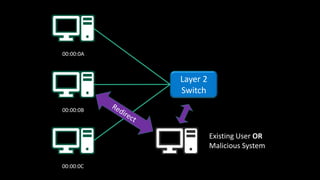
The document discusses Microsoft's wake-up proxy service and its role in managing network devices, particularly in a scenario involving the upgrade from Windows XP to Windows 7. It outlines the challenges of deploying this service on networks with 802.1x access control and highlights various tools that can be utilized for network monitoring and vulnerability assessment without a formal toolkit. Key takeaways emphasize the importance of understanding network ports and protocols, along with the necessity of server and network administration skills.



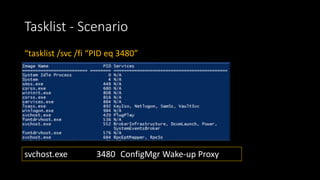
![Netstat - Scenario
“netstat –ano”
UDP [IP]:25536 *:* 3480](https://image.slidesharecdn.com/howmicrosoftwillmitmyournetwork-190412011704/85/How-Microsoft-will-MiTM-your-network-6-320.jpg)
![Log Files
• <![LOG[Not becoming a guardian because we are the only machine in
the subnet running WakeUp Proxy Service]LOG]!><time=“x:x:x.xxx”
component=“SleepAgent” … >
• <![LOG[Sending a port-grabbing frame for x.x.x.x / xxMACxx from
xxMACxx]LOG]!><time=“x:x:x.xxx” component=“SleepAgent” … >](https://image.slidesharecdn.com/howmicrosoftwillmitmyournetwork-190412011704/85/How-Microsoft-will-MiTM-your-network-10-320.jpg)