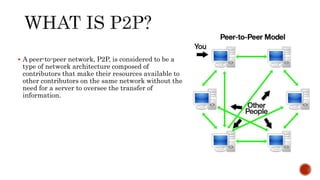
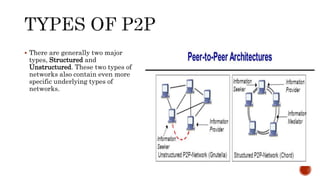
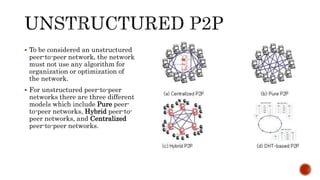
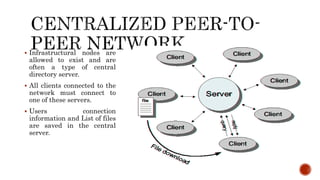
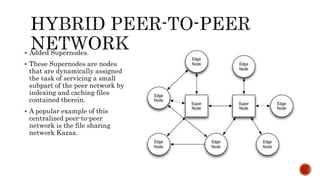
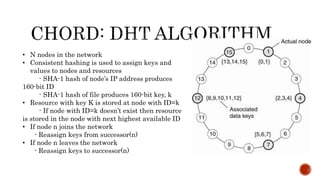
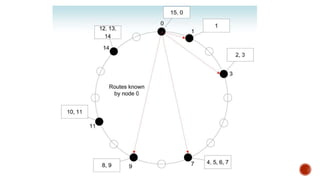
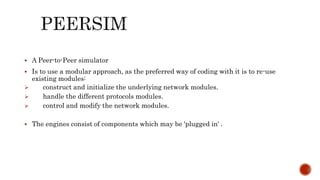
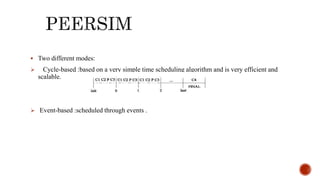
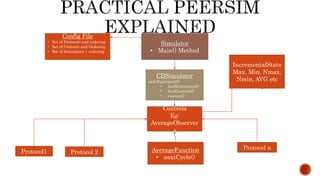
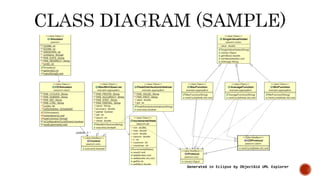
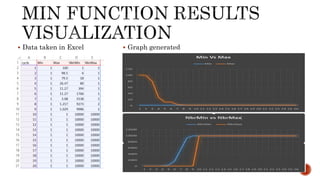
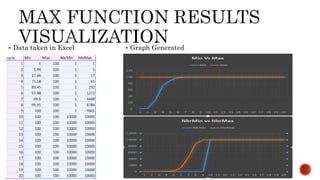
This document discusses web and social computing and peer-to-peer networks. It provides an overview of peer-to-peer network types including unstructured and structured networks. It also describes PeerSim, a peer-to-peer network simulator. The document outlines implementing maximum and minimum functions in PeerSim and analyzing the results. New methods were designed, run, and graphs of the outputs were generated to study how the maximum and minimum values changed over simulations.