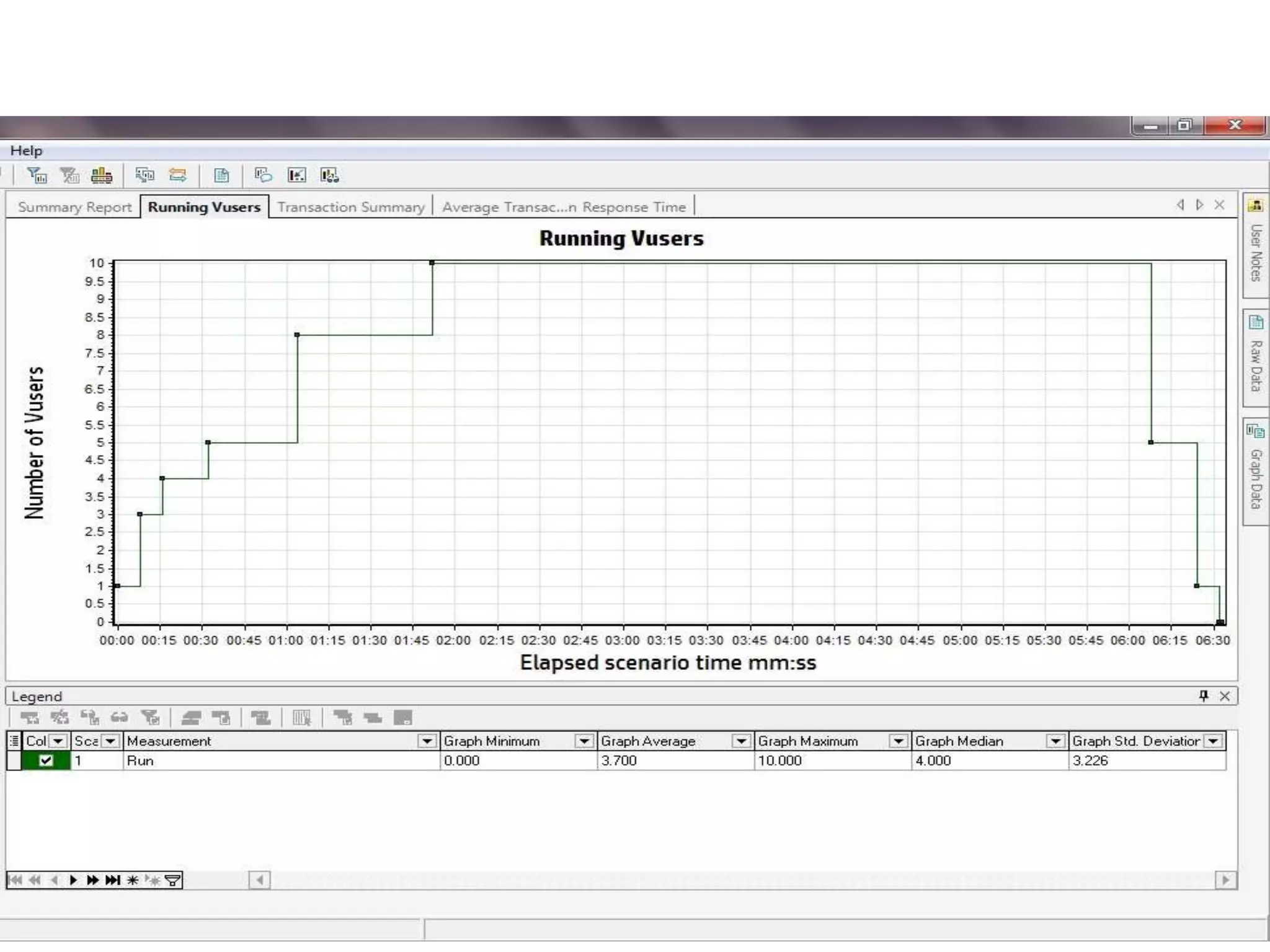
This document summarizes a dissertation on an improved load balancing technique for secure data in cloud computing. The dissertation discusses research issues in load balancing and data security in cloud computing. It proposes a load balancing methodology that uses a load balancer, Kerberos authentication, and Nginx load balancing algorithms like round robin and least connections to securely store and balance load of encrypted data across multiple cloud nodes. The methodology is implemented using tools like HP LoadRunner, Amazon Web Services, and Jelastic cloud platform. Performance is analyzed in terms of transaction time. The proposed technique aims to improve resource utilization, access control, data security, and efficiency in cloud environments.









![Existing Methodologies
Iterative Load Balancer:
• The problem of load balance for deploying ORAM-
based storage in clouds a tree-based ORAM structure,
and a set of storage servers, LB for deploying ORAM
in Cloud problem seeks a data placement such that
the maximum access load among all servers is
minimized.
• To overcome this difficulty, author propose a low-
complexity algorithm called ILB(Iterative Load
Balancer)to iteratively place buckets on servers, such
that only need to deal with a small-scale line are
programming in each iteration. [7]](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-12-2048.jpg)
![Weighted round robin load balancing:
•(WRR) is a common routing policy offered in cloud load balancers.
However, there is a lack of effective mechanisms to decide the
weights assigned to each server to achieve overall optimal revenue of
the system.
•The relations between probabilistic routing (PR) and weighted round
robin (WRR) policies and introduce the result of the algorithms
under different number of users classes.
•The advantage of the heuristic algorithm is that it is independent of
the number of requests Nr for each class and it has been proved to
achieve an optimality ratio of 1+1/(M−1) under heavy load, thus it
gets closer to optimality with increasing number of VMs.[8]](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-13-2048.jpg)
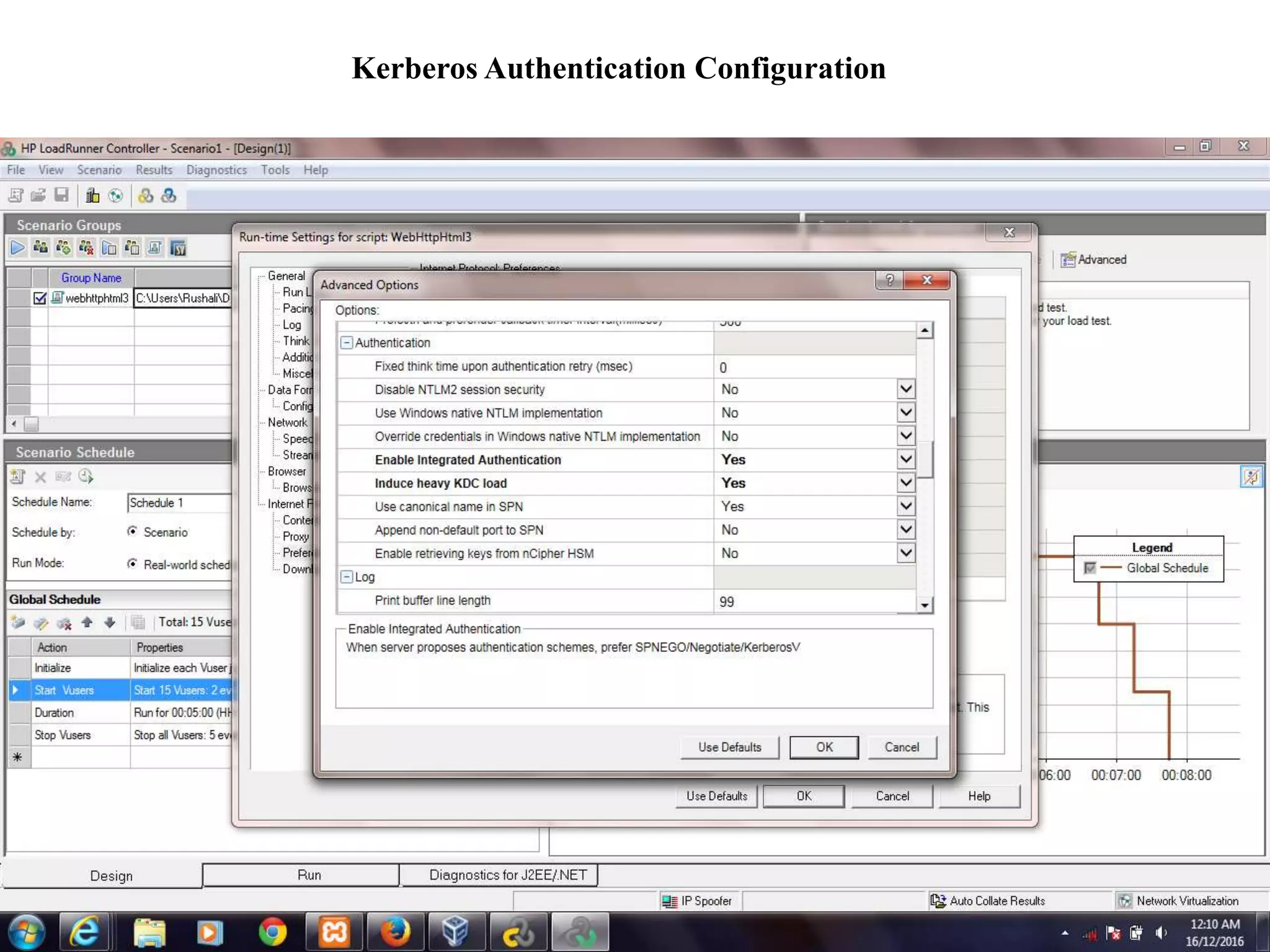
![Kerberos Model:
• To secure sensitive data Kerberos is used
for a user process protection method
based on a virtual machine monitor. The
basic set up of Kerberos protocol is as
shown.
The Kerberos server consists of an
Authentication Server (AS) and a Ticket
Granting Server (TGS). The AS and
TGS are responsible for creating and
issuing tickets to the clients upon
request. The AS and TGS usually run on
the same computer, and are collectively
known as the Key Distribution Center
(KDC). [25] Fig. Kerberos protocol](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-14-2048.jpg)






























![Referances
[1] Martin Randles, David Lamb, A. Taleb-Bendiab,“ A Comparative Study into Distributed Load Balancing
Algorithms for Cloud Computing" 2010 IEEE 24th International Conference on Advanced Information
Networking and Applications Workshops,pp.551-556,978-0-7695-4019-1/10$26.00© 2010 IEEE.
[2] Xu Y, Wu L, Guo L, Chen Z, Yang L, Shi Z."An Intelligent Load Balancing Algorithm Towards Efficient
Cloud Computing", In Workshops at the Twenty-Fifth AAAI on Artificial Intelligence, 2011 Aug 24.
[3] Hung-Chang Hsiao, Member, IEEE Computer Society, Hsueh-Yi Chung, Haiying Shen, Yu-Chang Chao,
“Load Rebalancing for Distributed File Systems in Clouds”, IEEE Transactions On Parallel And Distributed
Systems, Vol. 24, No. 5, May 2013.
[4]Xu,Gaochao; Pang, Junjie; Fu, Xiaodong ,"A Load Balancing Model Based on Cloud Partitioning for The
Public Cloud", IEEE Transaction on Cloud Computing, Tsinghua Science and Technology, Vol.18, No.1,
pp.34-39,Feb.2013.
[5]Dmitry Duplyakin, Paul Marshall Kate , Keahey Henry Tufo, Ali Alzabarah, "Rebalancing In A Multi-Cloud
Environment ", Science Cloud’13, Proceedings of the 4th ACM Workshop On Scientific Cloud Computing,
pp. 21-28, June 17, 2013.
[6] Kun Liu, Gaochao Xu and Jun’e Yuan, "An Improved Hadoop Data Load Balancing Algorithm", JOURNAL
OF NETWORKS, Vol. 8, No. 12, pp. 2816-2822, DECEMBER 2013.
[7] Peng Li; Song Guo "Load Balancing for Privacy-Preserving Access to Big Data in Cloud", IEEE Computer
Communications Workshops (INFOCOM WKSHPS), vol.21, no.4, 524 –528, May 2014. transactions on
information forensics and security, Vol.10, NO. 06, pp. 1315-1317, June 2015.
[8] Weikun Wang, Giuliano Casale, "Evaluating Weighted Round Robin Load Balancing for Cloud Web
Services" , 2014 16th International Symposium on Symbolic and Numeric Algorithms for Scientific
Computing published in IEEE, 978-1-4799-8448-0/15$31.00©2015 IEEE, pp.393-400,22-25 Sept. 2014](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-53-2048.jpg)
![[9] Zhipeng Gao; Dangpeng Liu; Yang Yang; JingchenZheng; YuwenHao, "A Load Balance Algorithm Based
On Nodes Performance In Hadoop Cluster," in Network Operations and Management Symposium
(APNOMS), 2014 16th Asia-Pacific,Vol.,No., pp.1-4, 17-19 Sept.2014
[10] Taeho Jung, Xiang-Yang Li, Senior Member, IEEE, Zhiguo Wan, and Meng Wan, "Control Cloud Data
Access Privilege and Anonymity With Fully Anonymous Attribute-Based Encryption", IEEE
TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY,pp.190- 199 vol.10, no.1,
JANUARY 2015
[11] Xinhua Dong; Ruixuan Li; Heng He; Wanwan Zhou; Zhengyuan Xue; Hao Wu, "Secure Sensitive Data
Sharing On a Big Data Platform", Tsinghua Science and Technology published in IEEE,
vol.20,no.1,pp.72-80,Feb.2015 DOI: 10.1109/ TST. 2015.7040516
[12] W. Teng; G. Yang; Y. Xiang; T. Zhang; D. Wang, "Attribute-based Access Control with Constant-size
Ciphertext in Cloud Computing," in IEEE Transactions on Cloud Computing , vol.PP, no.99, pp.1-1, 02
June 2015,doi: 10.1109/TCC.2015.2440247
[13] J. Li; W. Yao; Y. Zhang; H. Qian; J. Han, "Flexible and Fine-Grained Attribute-Based Data Storage in
Cloud Computing," in IEEE Transactions on Services Computing , vol. PP, no.99, pp.1-1, 22 January
2016, doi:10.1109/TSC.2016.2520932
[14] V. Chang and M. Ramachandran, "Towards Achieving Data Security with the Cloud Computing
Adoption Framework," in IEEE Transactions on Services Computing, vol.9, no.1, pp.138-151, Jan.-Feb.1
2016,doi:10.1109/TSC.2015.2491281
[15] Jia Zhao, Kun Yang, Xiaohui Wei, Yan Ding, Liang Hu, Gaochao Xu, "A Heuristic Clustering-Based
Task Deployment Approach for Load Balancing Using Bayes Theorem in Cloud Environment", IEEE
Transactions on Parallel & Distributed Systems, vol.27, no. 2, pp. 305-316, Feb. 2016,
[16] H.Wang; D. He; S. Tang, "Identity-Based Proxy-Oriented Data Uploading and Remote Data Integrity
Checking in Public Cloud," in IEEE Transactions on Information Forensics and Security ,vol.PP,no.99,pp.1-1,](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-54-2048.jpg)
![[17] Mayanka Katyal*, Atul Mishra*,"A Comparative Study of Load Balancing Algorithms in Cloud
Computing Environment" in International Journal of Distributed and Cloud Computing, pp. 6-14, vol.1,
Issue 2, December 2013
[18] Aarti Singh, Dimple Juneja, Manisha Malhotra , "Autonomous Agent Based Load Balancing Algorithm
in Cloud Computing", International Conference On Advanced Computing Technologies And Applications
(Icacta-2015), 1877-0509 © 2015 Published by Elsevier B.V.
[19] A. Paya; D. Marinescu, "Energy-aware Load Balancing and Application Scaling for the Cloud Ecosystem,
in IEEE Transactions on Cloud Computing, vol. pp, no.99, pp.1-1 Figure: cloud service model ;
Adopted from: Effectively and Securely Using the Cloud Computing Paradigm by peter Mell, Tim
[20]Zhen Xiao, Senior Member, IEEE, Weijia Song, and Qi Chen “Dynamic Resource Allocation using Virtual
Machines for Cloud Computing Environment” IEEE TRANSACTION ON PARALLEL AND DISTRIBUTED
SYSTEMS(TPDS), VOL. N, NO. N, MONTH YEAR 1
[21] S. Gaisbauer, J. Kirschnick, N. Edwards and J. Rolia, "VATS: Virtualized-Aware Automated Test Service,
" 2008 Fifth International Conference on Quantitative Evaluation of Systems, St. Malo, 2008,pp. 93-102.
Jinzhong Niu ; CSc31800: Internet Programming, CS- CCNY, Spring 2004,The note contains The
Definitive Guide, O’Reilly.
[22] B. Li, H. Zhou, D. Zuo, Z. Zhang, P. Zhou and L. Jia, "Performance modeling and benchmarking of bank
intermediary business on high-performance fault-tolerant computers," 2011 IEEE/IFIP 41st International
Conference on Dependable Systems and Networks Workshops (DSN-W), HongKong,2011, pp.234-239.
[23] Automated detection of performance regressions using statistical process
control techniques ”ICPE '12 ProceedingsThanh H.D. Nguyen,Queen's University, Kingston, ON, Canada ”
of the 3rd ACM/SPEC International Conference on Performance Engineering, PP.299-310 Boston,
Massachusetts, USA -April 22 - 25, 2012,ACM New York, NY, USA
[24] NIST (Authors: P. Mell and T. Grance), "The NIST Definition of Cloud Computing (ver. 15),“
National Institute of Standards and Technology, Information Technology Laboratory (October 7 2009).
[25] Published in 2008 by the MIT Kerberos Consortium. Ver. July 23, 2008.](https://image.slidesharecdn.com/30-1-210721090542/75/My-Dissertation-2016-55-2048.jpg)
