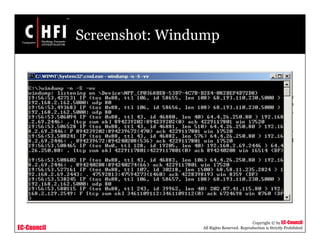
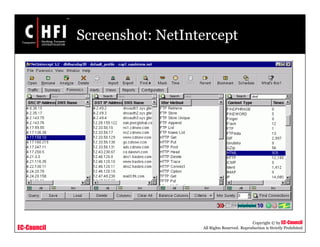
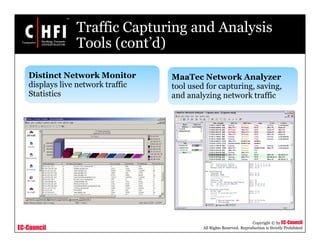
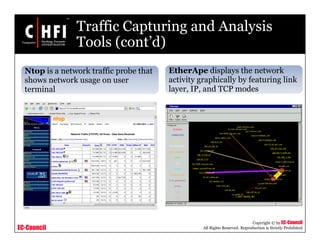
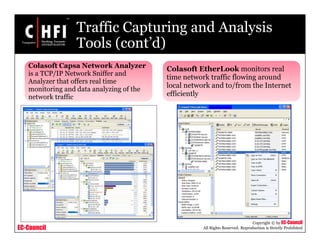
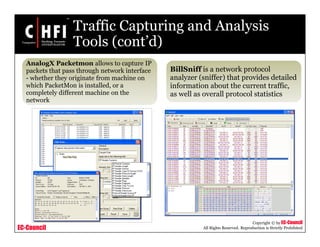
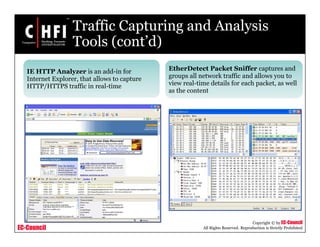
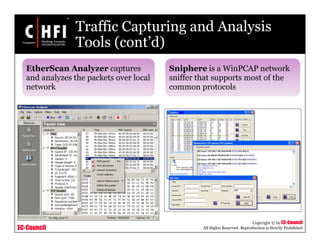
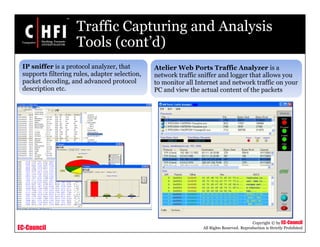
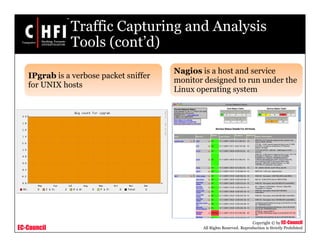
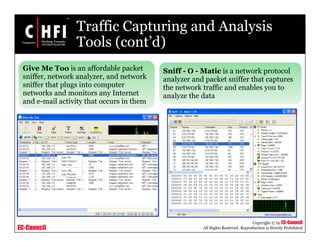
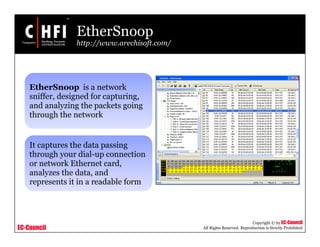
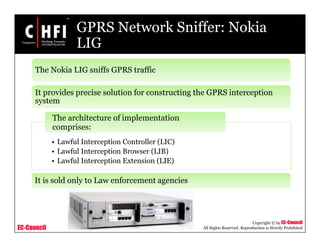
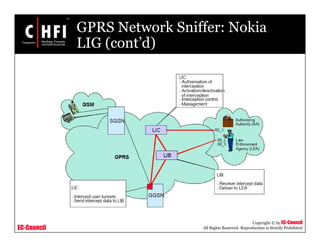
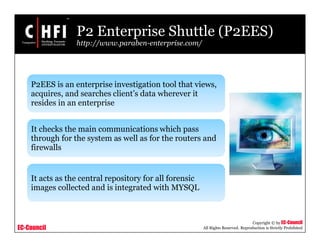
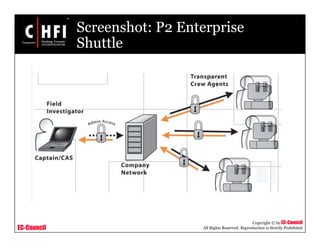
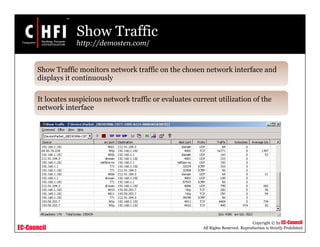
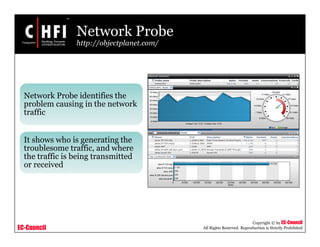
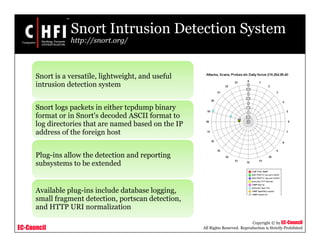
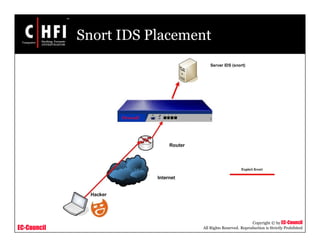
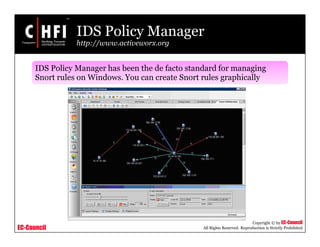
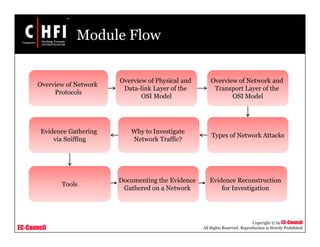
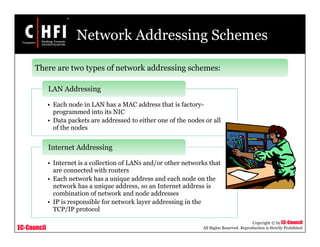
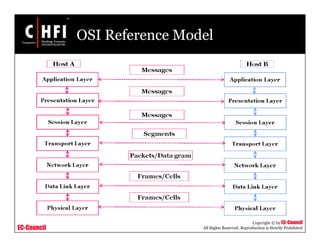
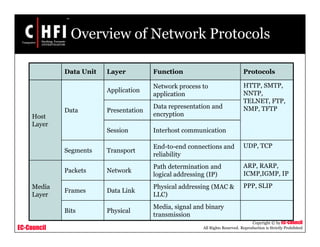
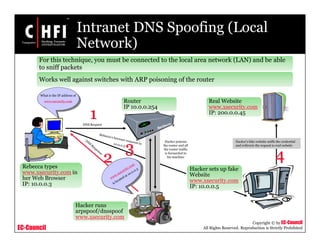
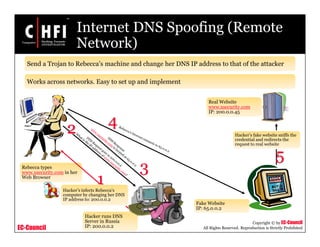
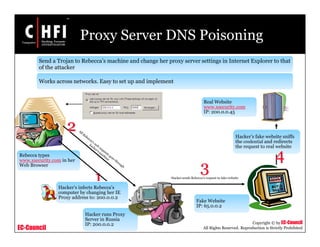
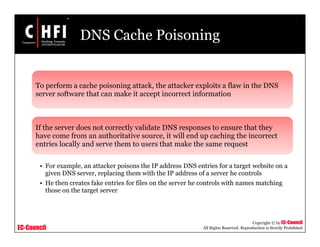
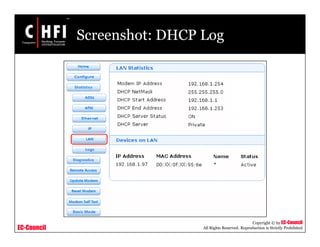
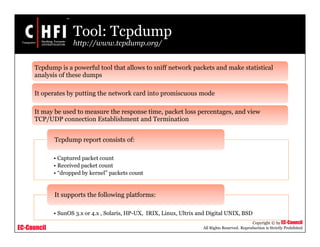
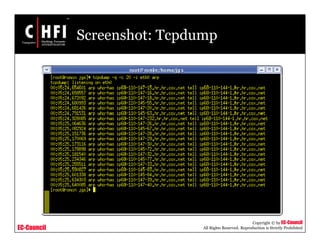
This document discusses tools and techniques for investigating network traffic. It provides overviews of network protocols and layers of the OSI model. It describes types of network attacks investigators may encounter and reasons for examining network traffic, such as locating suspicious activity. Methods of gathering evidence are covered, including sniffing packets and acquiring traffic using DNS poisoning. Specific tools are outlined, such as Wireshark, Tcpdump and Windump, that can capture and analyze network packets.










![EC-Council
Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited
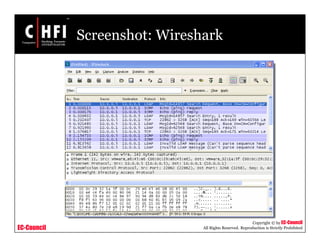
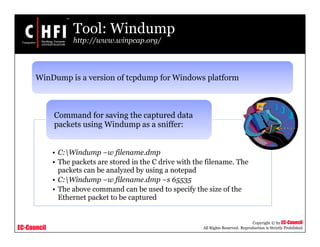
Tool: Windump (cont’d)
http://www.winpcap.org/
• 20:50:00.037087 IP (tos 0x0, ttl 128, id 2572, len 46) 192.168.2.24.1036
> 64.12.24.42.5190: P [tcp sum ok] 157351:157357(6) ack 2475757024 win
8767 (DF)
Sample output of the Windump:
• timestamp 20:50:00.037087
• IP [protocol header] tos 0x0, ttl 128, id 2572, len 46
• source IP:port 192.168.2.24.1036
• destination IP:port 64.12.24.42.5190:
• P [push flag] [tcp sum ok] 157351:157357
• [sequence numbers] (6) [bytes of data]
• acknowledgement and sequence number ack 2475757024
• window size (DF) [don’t fragment set] win 8767
The above entry can be deciphered as:](https://image.slidesharecdn.com/file000140-140617045500-phpapp02/85/File000140-30-320.jpg)