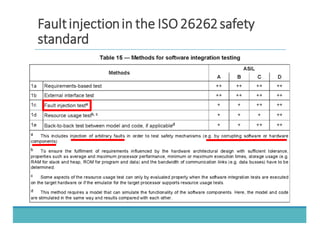
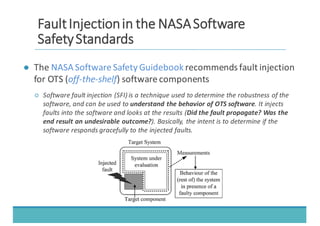
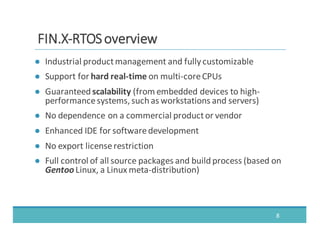
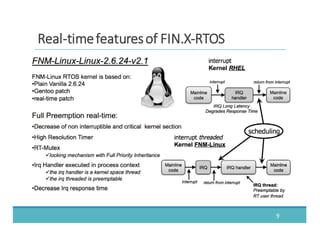
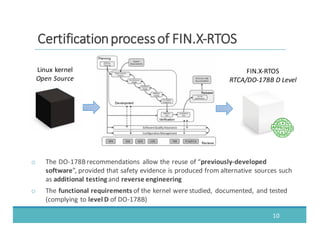
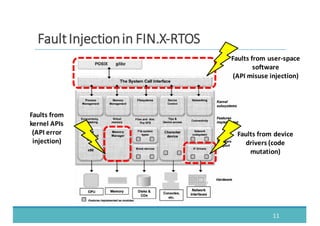
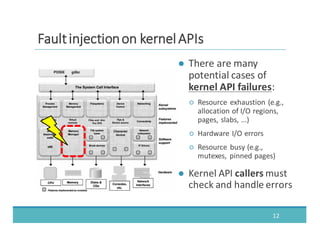
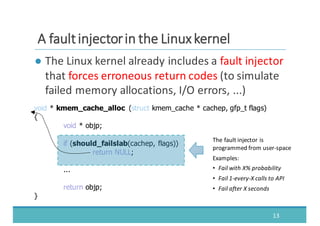
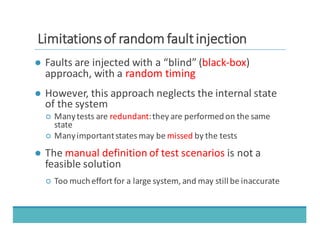
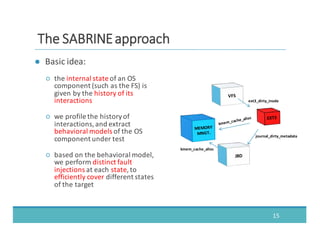
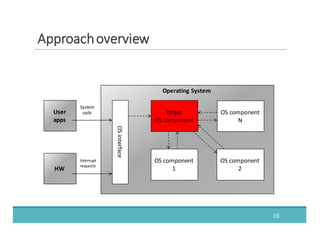
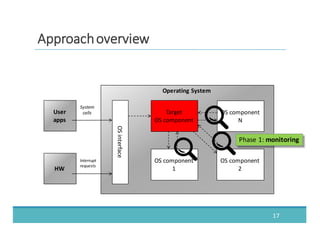
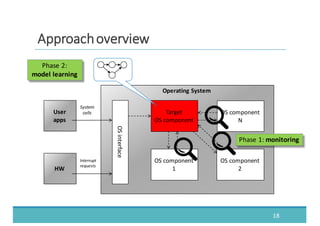
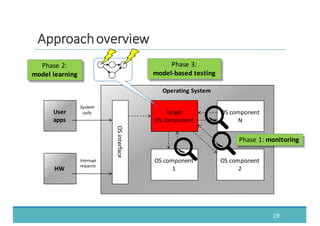
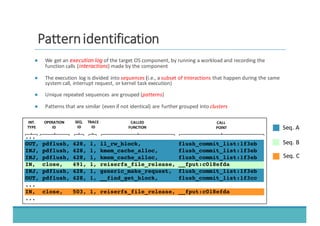
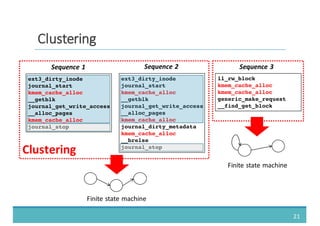
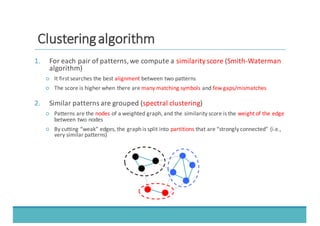
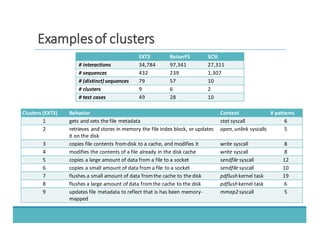
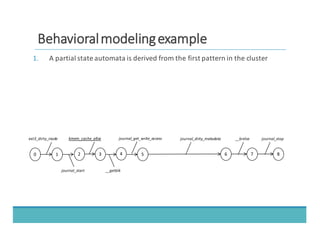
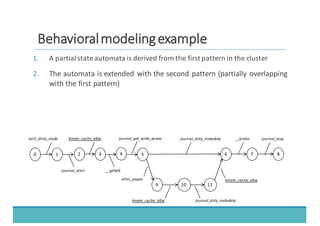
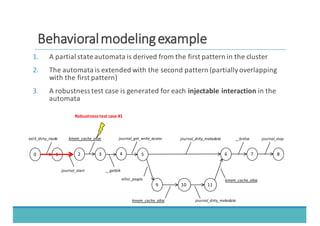
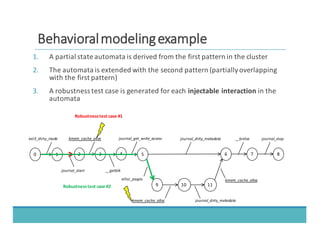
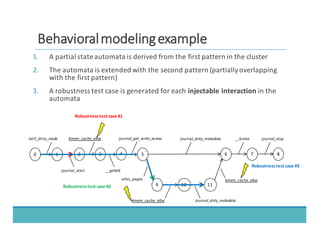
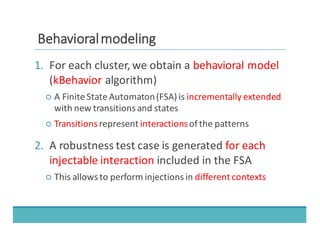
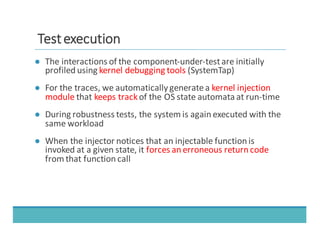
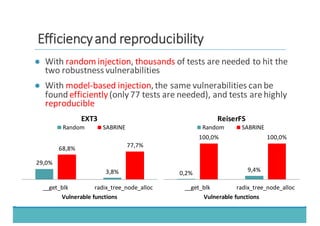
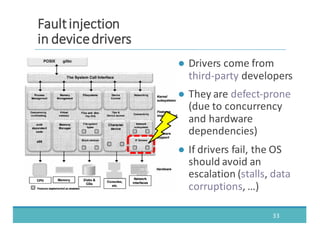
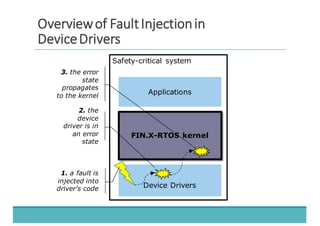
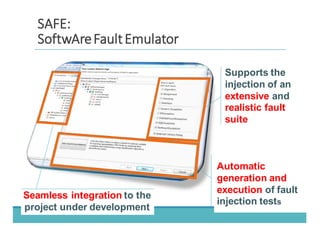
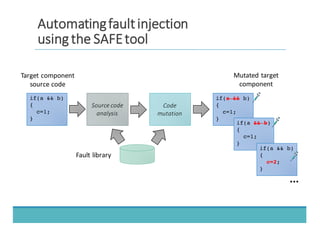
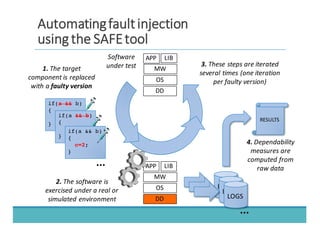
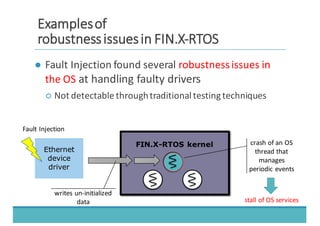
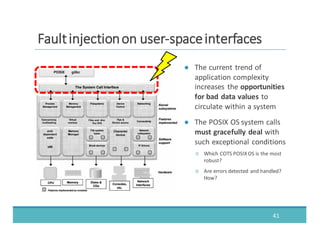
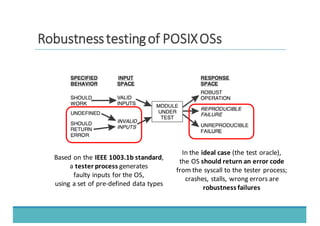
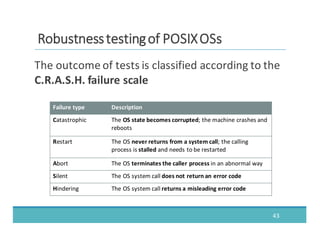
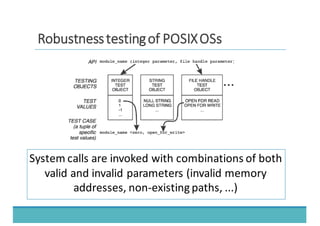
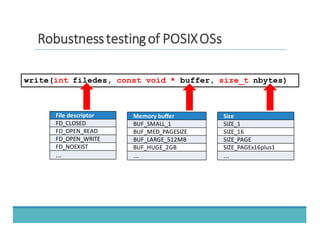
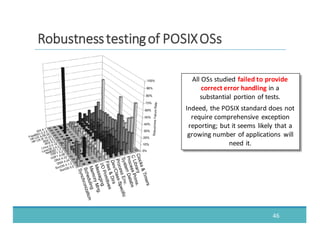
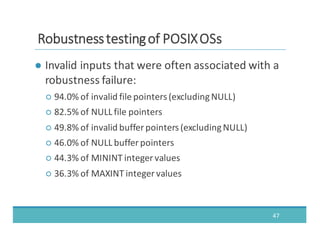
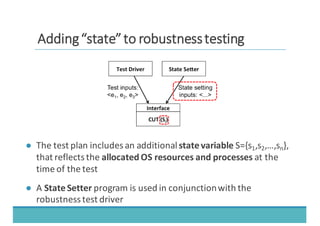
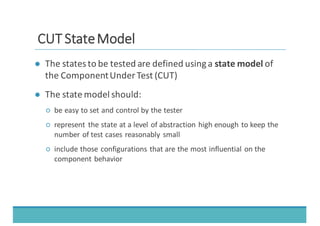
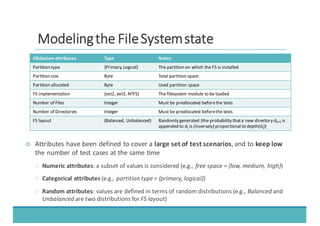
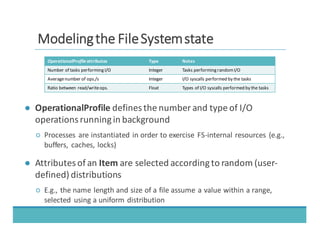
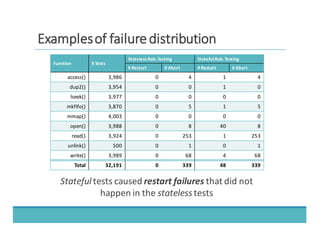
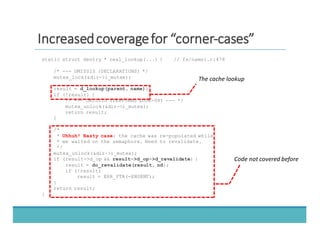
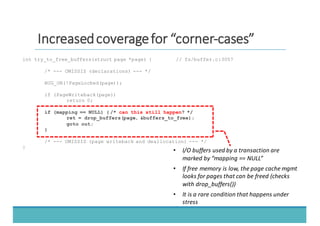
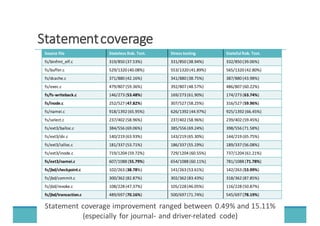
The document discusses fault injection as a critical testing process for software certification, particularly in safety-sensitive systems to enhance fault tolerance and prevent accidents like the Toyota unintended acceleration case. It outlines methodologies for fault injection in operating systems, including testing for robustness, modeling system behaviors, and using techniques to simulate faults efficiently. The use of the fin.x-rtos, a compliant Linux distribution, is highlighted as a practical example of implementing these fault injection techniques in real-time operating systems.



![FFaauulltt
iinnjjeeccttiioonn
iinn
tthhee
DDOO-‐-‐117788BB//CC
ssaaffeettyy
ssttaannddaarrddss
The
standard
recommends
robustness
test
cases
“...
[able
to]
demonstrate
the
ability
of
the
software
to
respond
to
abnormal
inputs
and
conditions.
Activities
include:
○ Real
and
integer
variables
should
be
exercised
using
equivalence
class
selection
of
invalid
values.
○ For
time-‐related
functions,
such
as
filters,
integrators
and
delays,
test
cases
should
be
developed
for
arithmetic
overflow
protection
mechanisms.
○ For
state
transitions,
test
cases
should
be
developed
to
provoke
transitions
that
are
not
allowed by
the
software
requirements.”
○ ...
*
RTCA
DO-‐178B,
Software
considerations
in
airborne
systems
and
equipment
certification,
Sec.
6.4.2.2](https://image.slidesharecdn.com/sfisafetylinkedin-170515162846/85/Fault-Injection-for-Software-Certification-4-320.jpg)