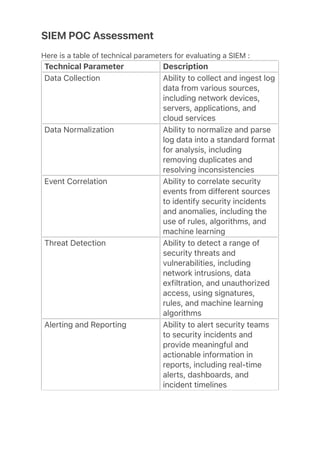
This document provides a table of technical parameters for evaluating a SIEM (security information and event management) system during a proof of concept assessment. The table includes parameters such as data collection, data normalization, event correlation, threat detection, alerting and reporting, incident response, user management, data privacy and security, scalability and performance, and integration with other security tools. Evaluating a SIEM against these comprehensive technical parameters can provide a deeper understanding of its capabilities and help determine if it is suitable for full deployment in an organization's network environment.