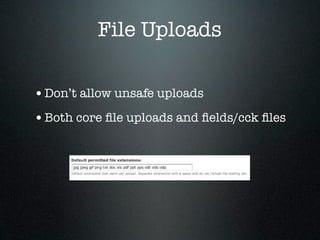
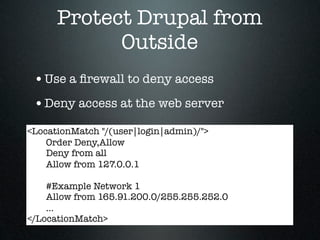
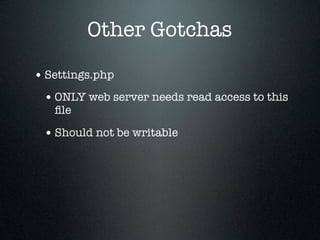
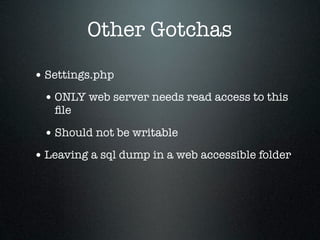
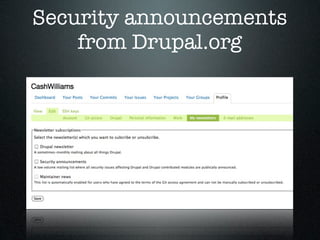
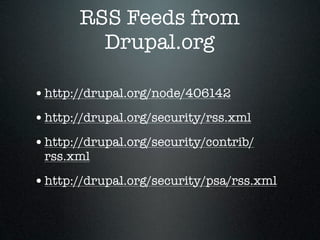
The document provides an overview of Drupal security, highlighting the importance of protecting website data from unauthorized access, modification, and destruction. It outlines various attack vectors, reinforces the need to keep Drupal updated, and suggests best practices for configuring database users, utilizing HTTPS, and implementing security modules. Additionally, it emphasizes precautions for file uploads, firewall usage, and overall site security maintenance.

















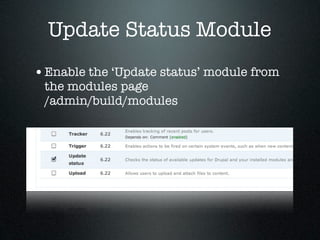
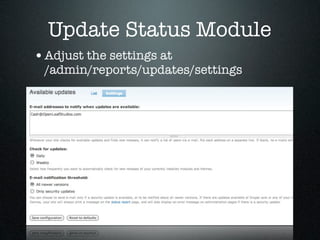








![HTTPS
• Use HTTPS if at all possible
• Session hijacking
• Packet sniffing on open networks
• Secure Pages module
• OR .htaccess rule to redirect all traffic
RewriteCond %{SERVER_PORT} 80
RewriteRule ^(.*)$ https://%{HTTP_HOST}/$1 [R,L]
php_value session.cookie_secure 1](https://image.slidesharecdn.com/dddsecurity-120703083327-phpapp02/85/Drupal-Security-Intro-37-320.jpg)