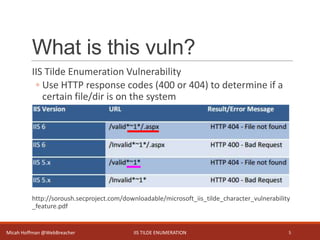
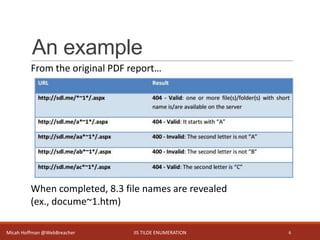
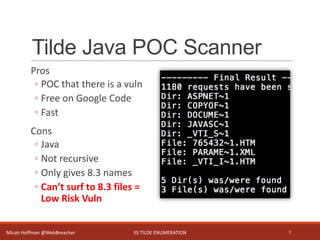
This document discusses IIS tilde enumeration, a vulnerability that allows determining if certain files or directories exist on a system by checking HTTP response codes. It presents a Python tool called tilde_enum.py that exploits this vulnerability to recursively enumerate files and directories using wordlists. The tool represents an improvement over existing Java tools by providing full file and directory names rather than just 8.3 versions, and allowing deeper recursion. However, it is still limited in some ways such as not finding all possible files. Future enhancements are proposed to address limitations.





![tilde_enum.py
https://github.com/WebBreacher/tilde_enum
Micah Hoffman @WebBreacher IIS TILDE ENUMERATION 9
$ ./tilde_enum.py -h
usage: tilde_enum.py [-h] [-b] [-d DIRWORDLIST] [-f] [-u URL] [-v] wordlist
Exploits and expands the file names found from the tilde enumeration vuln
positional arguments:
wordlist the wordlist file
optional arguments:
-h, --help show this help message and exit
-b brute force backup extension, extensions
-d DIRWORDLIST an optional wordlist for directory name content
-f force testing of the server even if the headers do not
report it as an IIS system
-u URL URL to scan
-v verbose output](https://image.slidesharecdn.com/iistildeenum2014-140310215038-phpapp01/85/IIS-Tilde-Enumeration-Vulnerability-9-320.jpg)
![tilde_enum.py Example
Micah Hoffman @WebBreacher IIS TILDE ENUMERATION 10
$ ./tilde_enum.py -u http://iis
/pentest/fuzzdb/discovery/predictableres/raft-small-words-
lowercase.txt
[-] Testing with dummy file request http://iis/lJP7ROxEoS.htm
[-] URLNotThere -> HTTP Code: 404, Response Length: 1635
[-] Testing with user-submitted http://iis
[-] URLUser -> HTTP Code: 200, Response Length: 1433
[+] The server is reporting that it is IIS (Microsoft-
IIS/6.0).
[+] The server is vulnerable to the tilde enumeration
vulnerability (IIS/5|6.x)..
[+] Found a new directory: docume
[+] Found a new directory: javasc
[+] Found file: parame . xml
[+] Found file: 765432 . htm
[+] Found file: _vti_i . htm
[+] Found a new directory: _vti_s
[-] Finished doing the 8.3 enumeration for /.](https://image.slidesharecdn.com/iistildeenum2014-140310215038-phpapp01/85/IIS-Tilde-Enumeration-Vulnerability-10-320.jpg)
![tilde_enum.py Example
con’t
Micah Hoffman @WebBreacher IIS TILDE ENUMERATION 11
---------- FINAL OUTPUT ------------------------------
[*] We found files for you to look at:
[*] http://iis/_vti_inf.html - Size 1754
[*] http://iis/documentation/advertising.html - Size 227
[*] http://iis/documentation/default.aspx - Size 1433
[*] http://iis/javascript/321.xlsx - Size 227
[*] http://iis/parameter.xml - Size 1307
[*] Here are all the 8.3 names we found.
[*] If any of these are 6 chars and look like they should
work, try the file name with the first or second instead of
all of them.
[*] http://iis/documentation/advert~1.htm
[*] http://iis/documentation/defaul~1.asp
[*] http://iis/765432~1.htm
[*] http://iis/_vti_i~1.htm
[*] http://iis/parame~1.xml
[*] http://iis/javascript/321~1.xls](https://image.slidesharecdn.com/iistildeenum2014-140310215038-phpapp01/85/IIS-Tilde-Enumeration-Vulnerability-11-320.jpg)



