The document discusses MySQL Firewall, which enhances database security by defending against SQL injection attacks and requiring minimal performance costs. It outlines the architecture, installation, and operation of the firewall through a case study involving a WordPress installation. The firewall allows for safe SQL command execution by comparing incoming queries against an allowed list, offering both blocking and logging capabilities for suspicious activities.

















![Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |
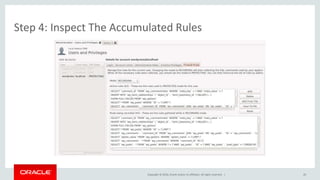
What Does the Application Get ?
• $ client/mysql -u wordpress --protocol=tcp -p -e "select version()“
ERROR 1045 (28000) at line 1: Statement was blocked by Firewall
• [Mon Jun 20 13:23:00.091246 2016] [:error] [pid 31596] [client 127.0.0.1:40226]
WordPress database error Statement was blocked by Firewall for query SELECT *
FROM wp_users WHERE user_email = 'test@test.com' made by edit_user, email_exists,
get_user_by, WP_User::get_data_by, referer: http://localhost/blog/wp-admin/user-
new.php
• [Mon Jun 20 13:23:00.094753 2016] [:error] [pid 31596] [client 127.0.0.1:40226]
WordPress database error Statement was blocked by Firewall for query SELECT *
FROM wp_users WHERE user_email = 'test@test.com' made by edit_user,
wp_insert_user, email_exists, get_user_by, WP_User::get_data_by, referer:
http://localhost/blog/wp-admin/user-new.php
23](https://image.slidesharecdn.com/2016oscmysqlfirewall-160621090122/85/2016-oSC-MySQL-Firewall-23-320.jpg)



