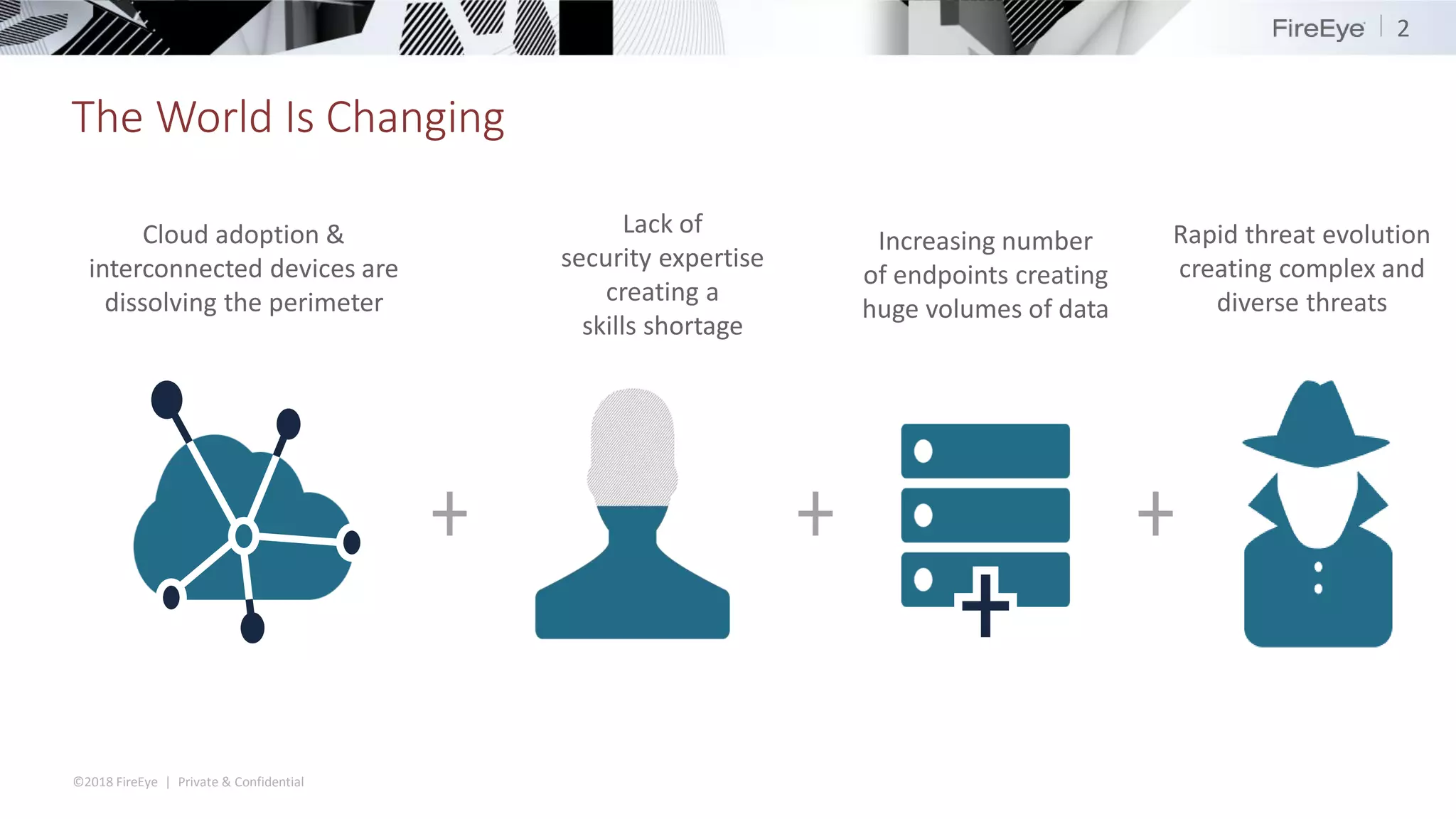
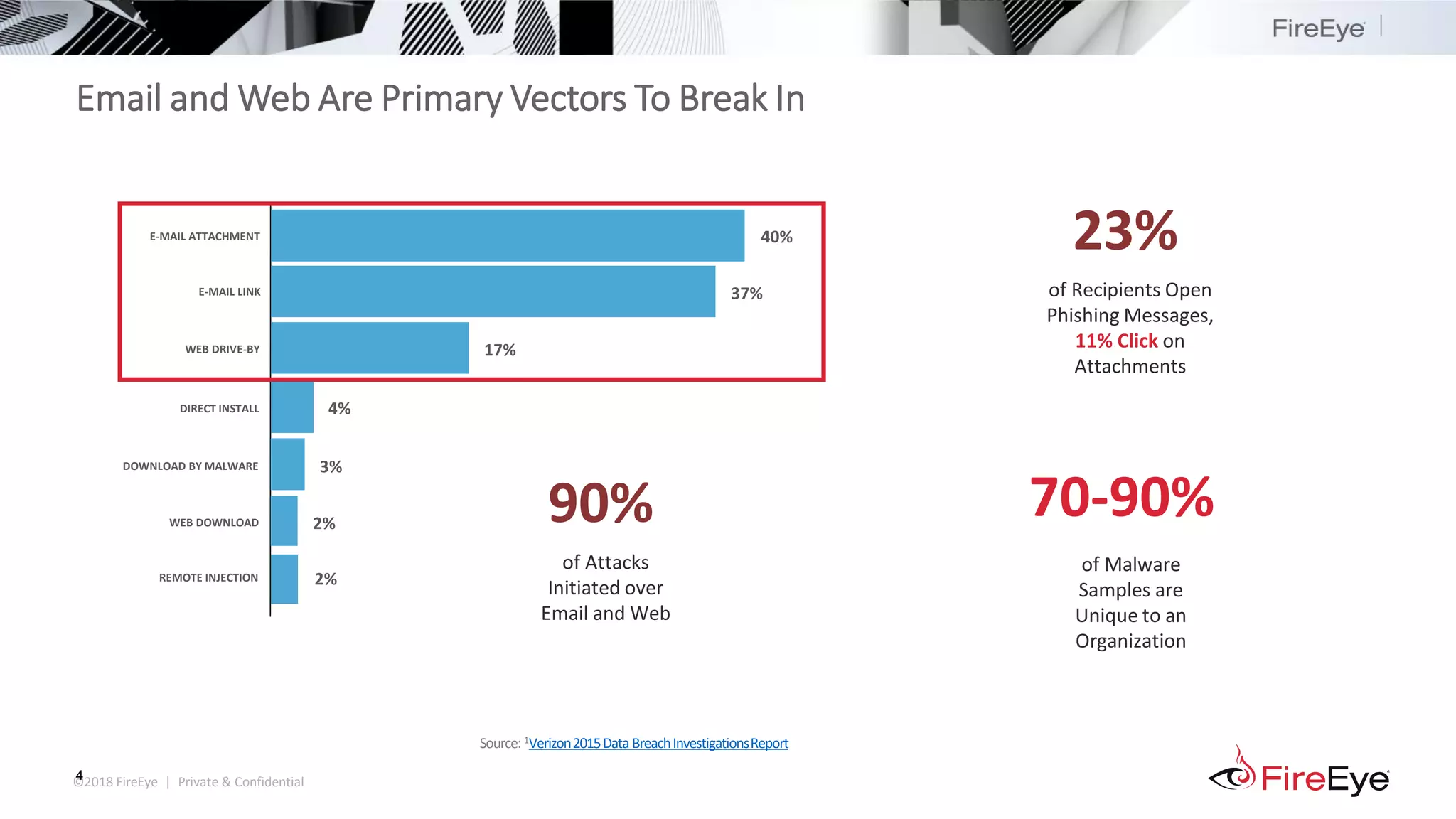
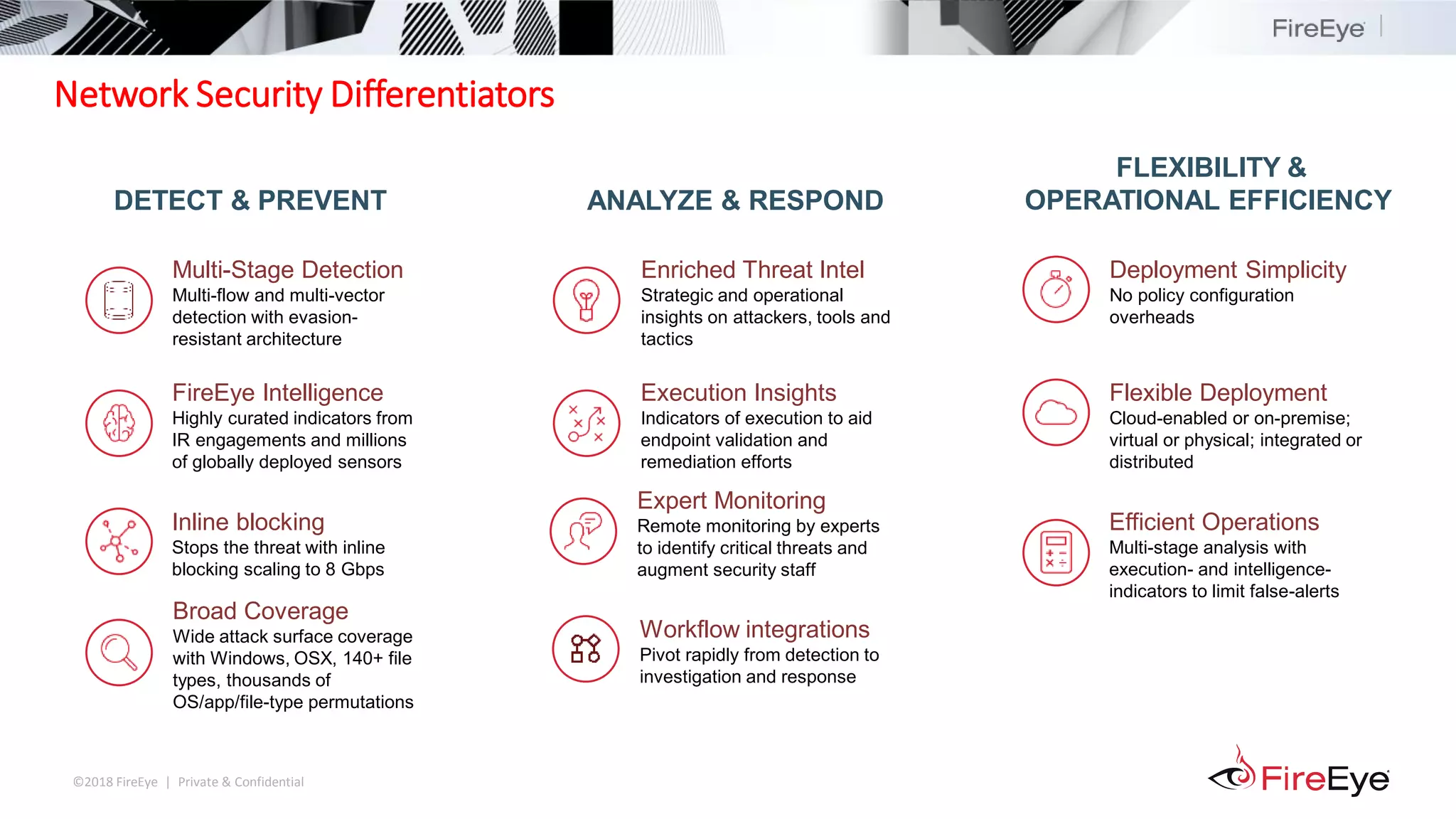
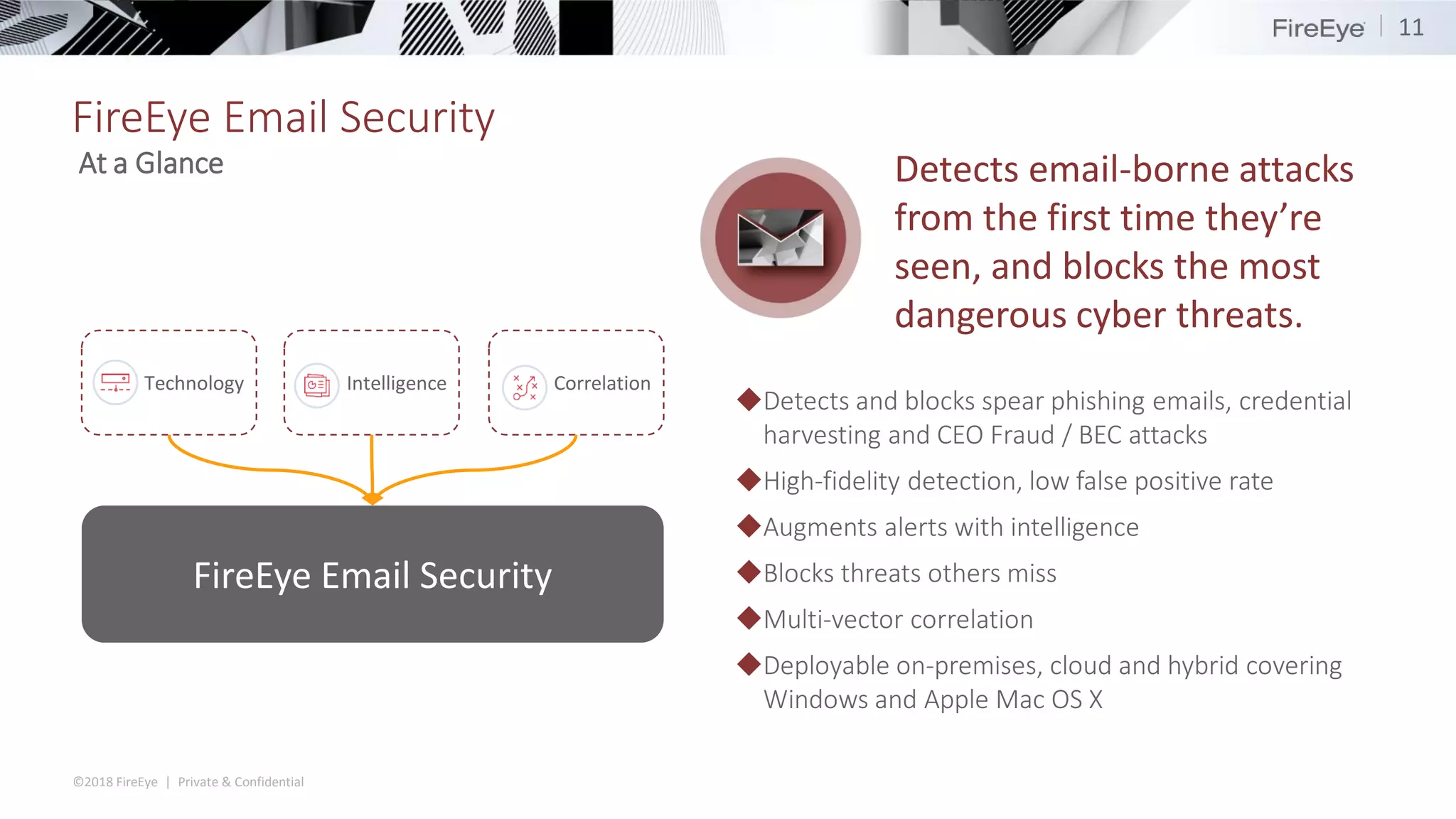
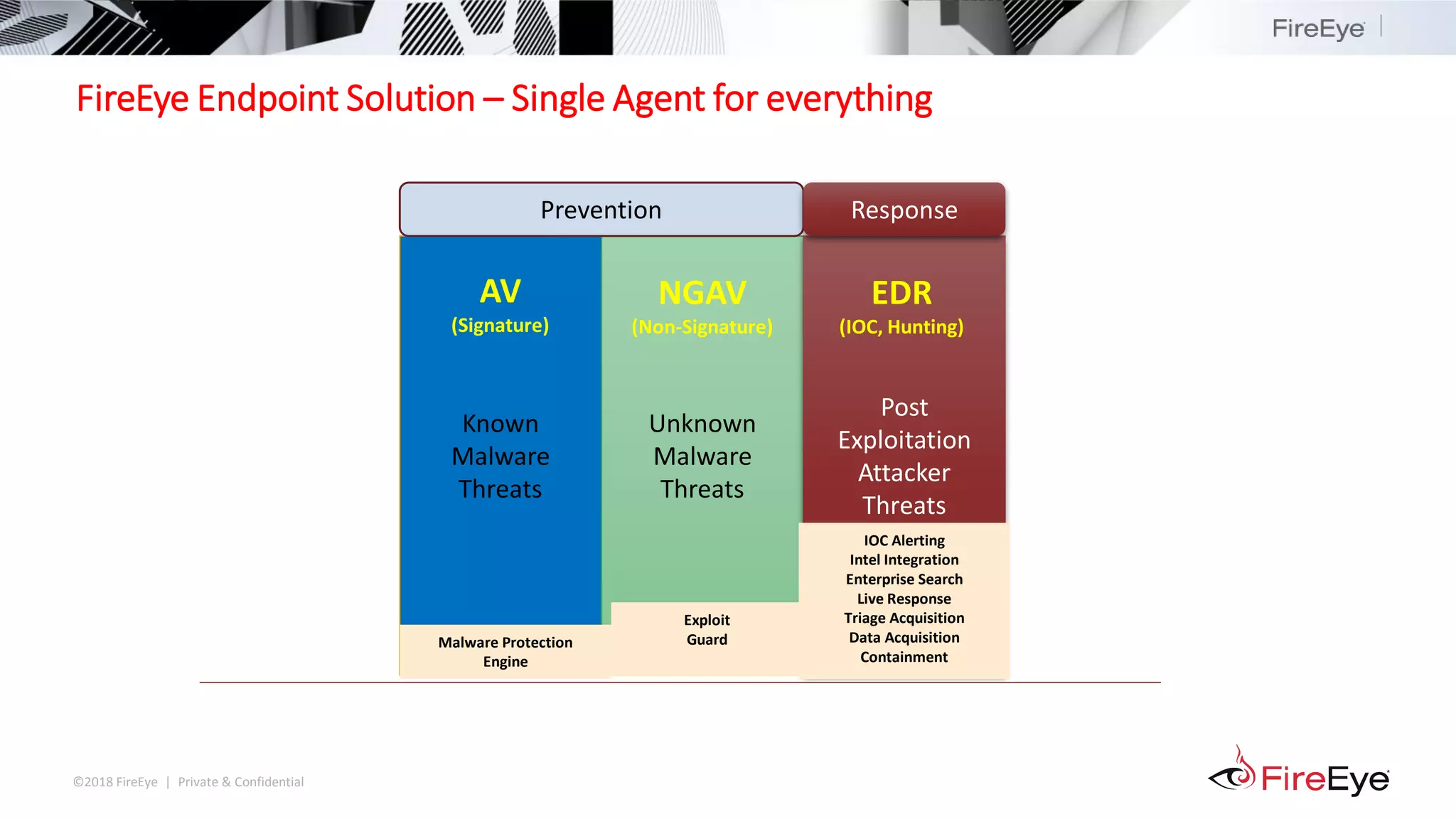
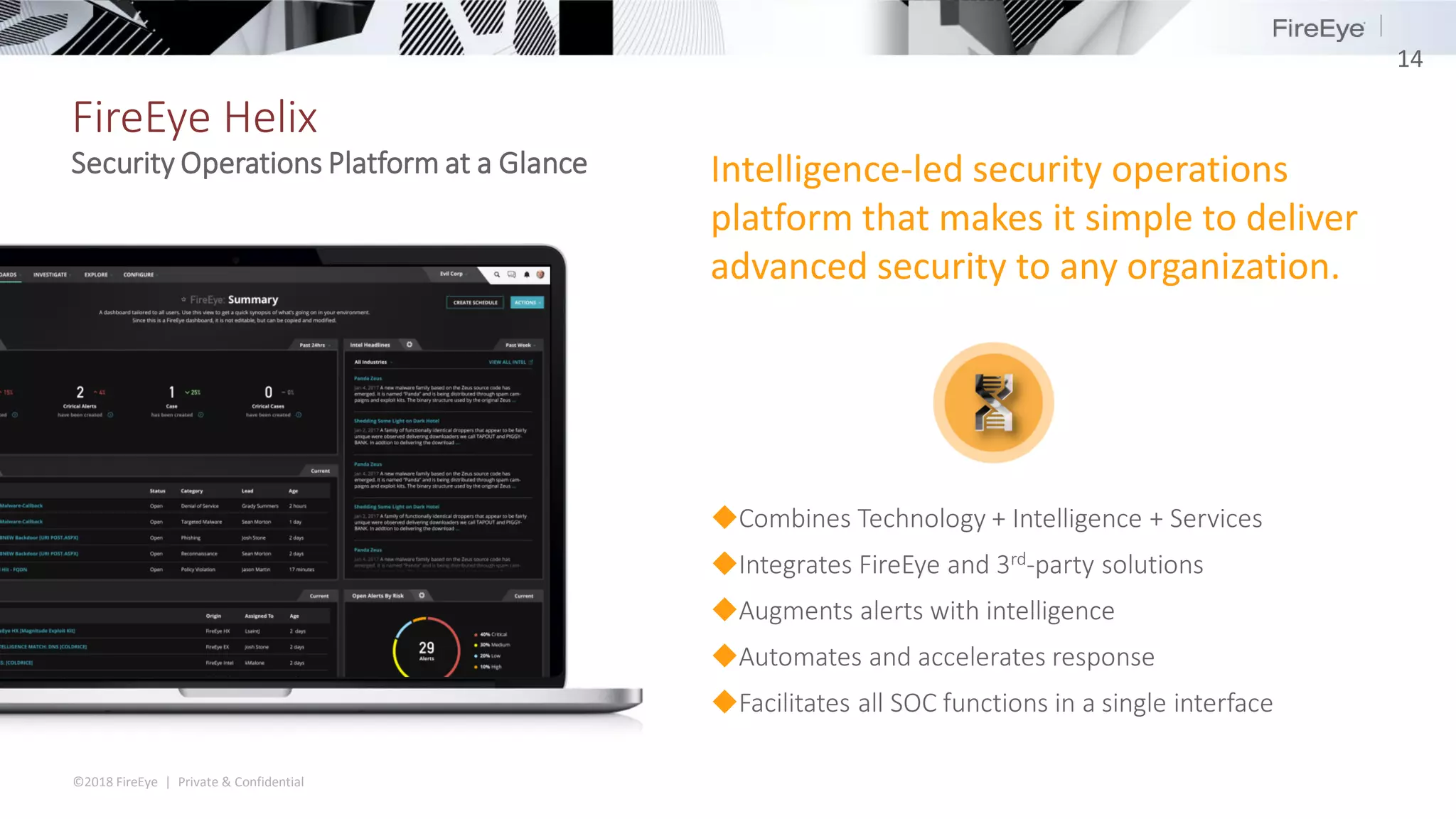
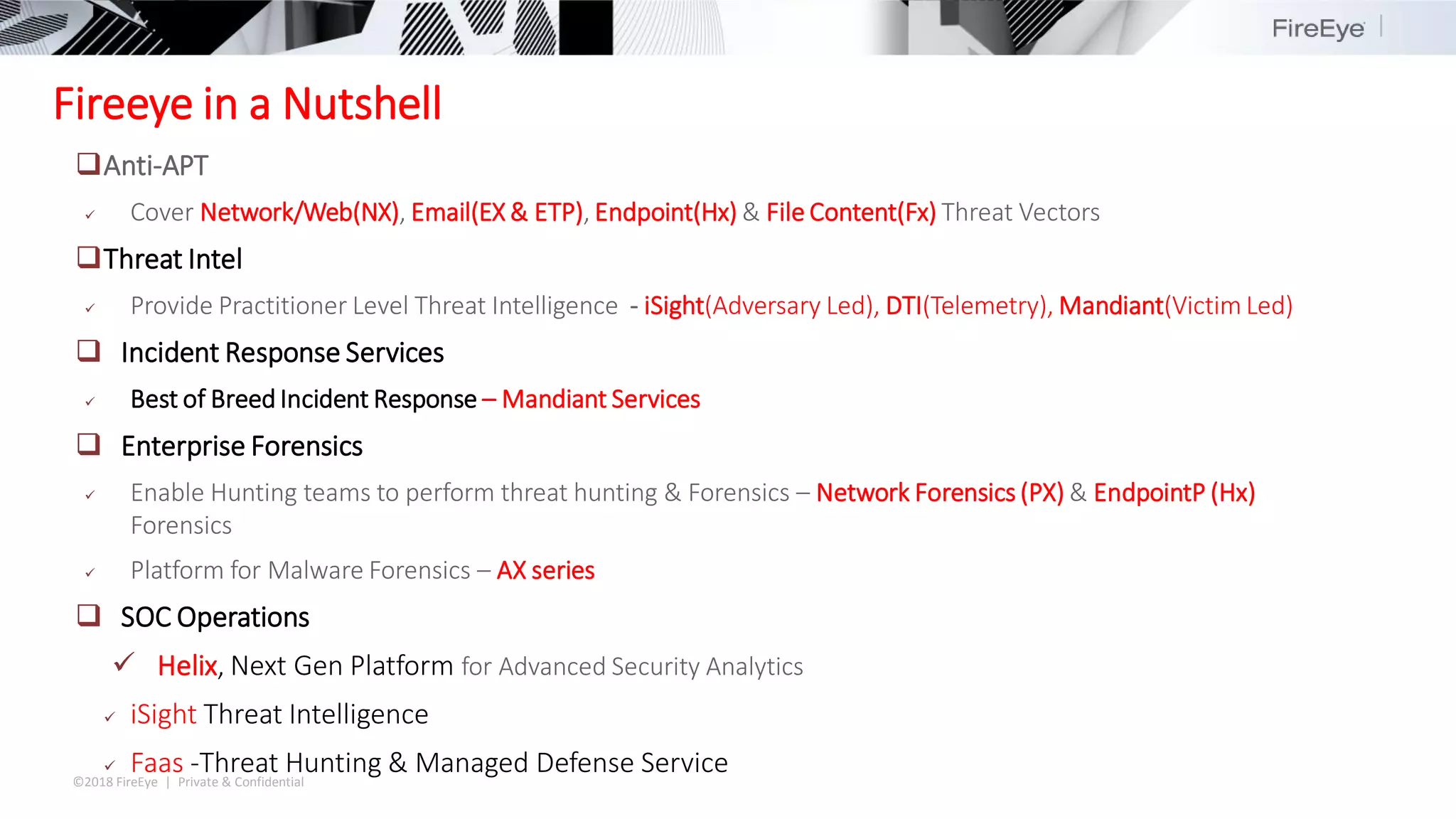
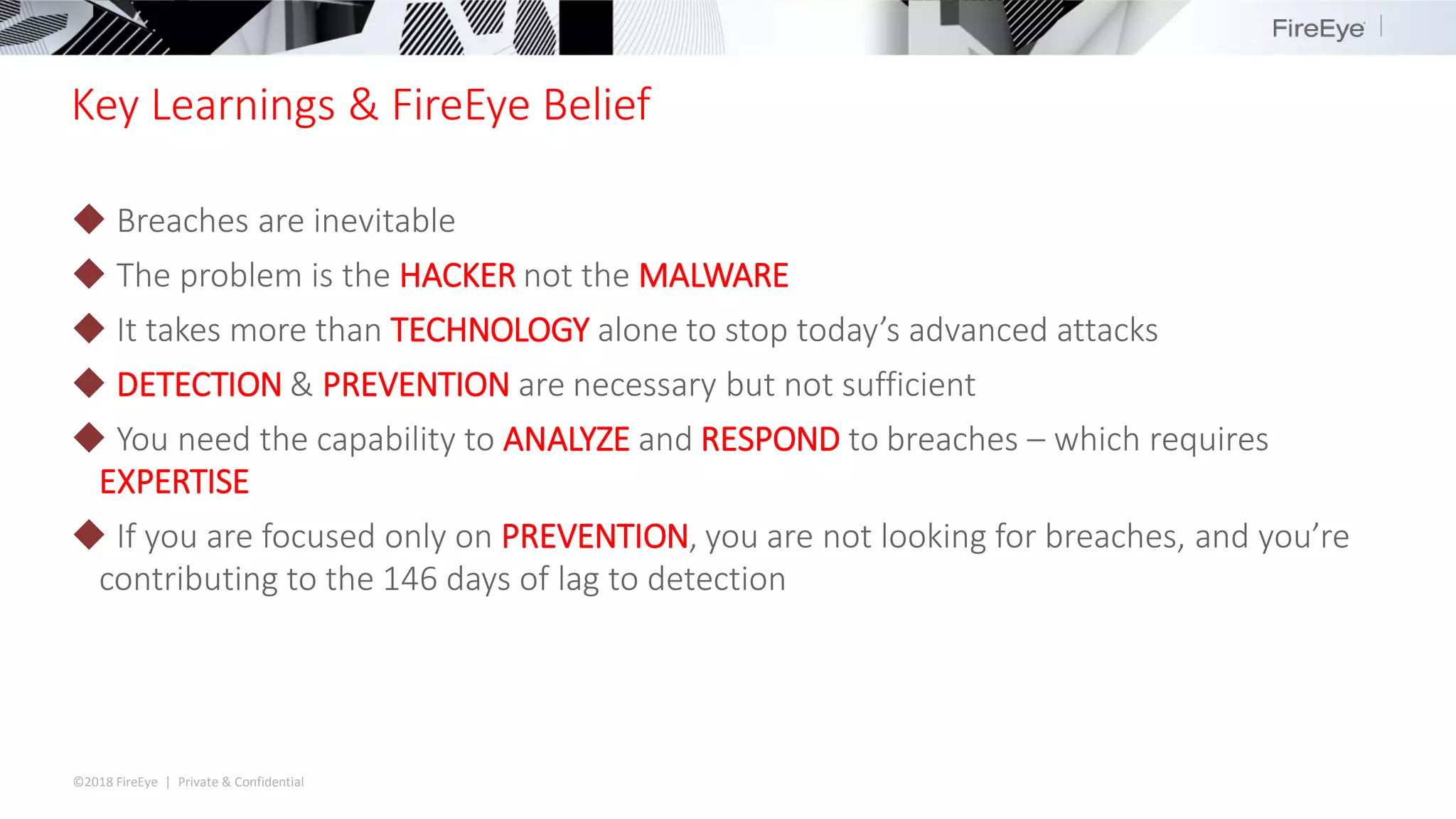
The document summarizes FireEye's cybersecurity products and services. It discusses how the evolving threat landscape is dissolving security perimeters and creating skills shortages. It then outlines FireEye's network security, email security, endpoint security, and Helix security operations platform products. It also describes FireEye's threat intelligence, managed defense services, and Mandiant consulting services for incident response and strategic advisory work.