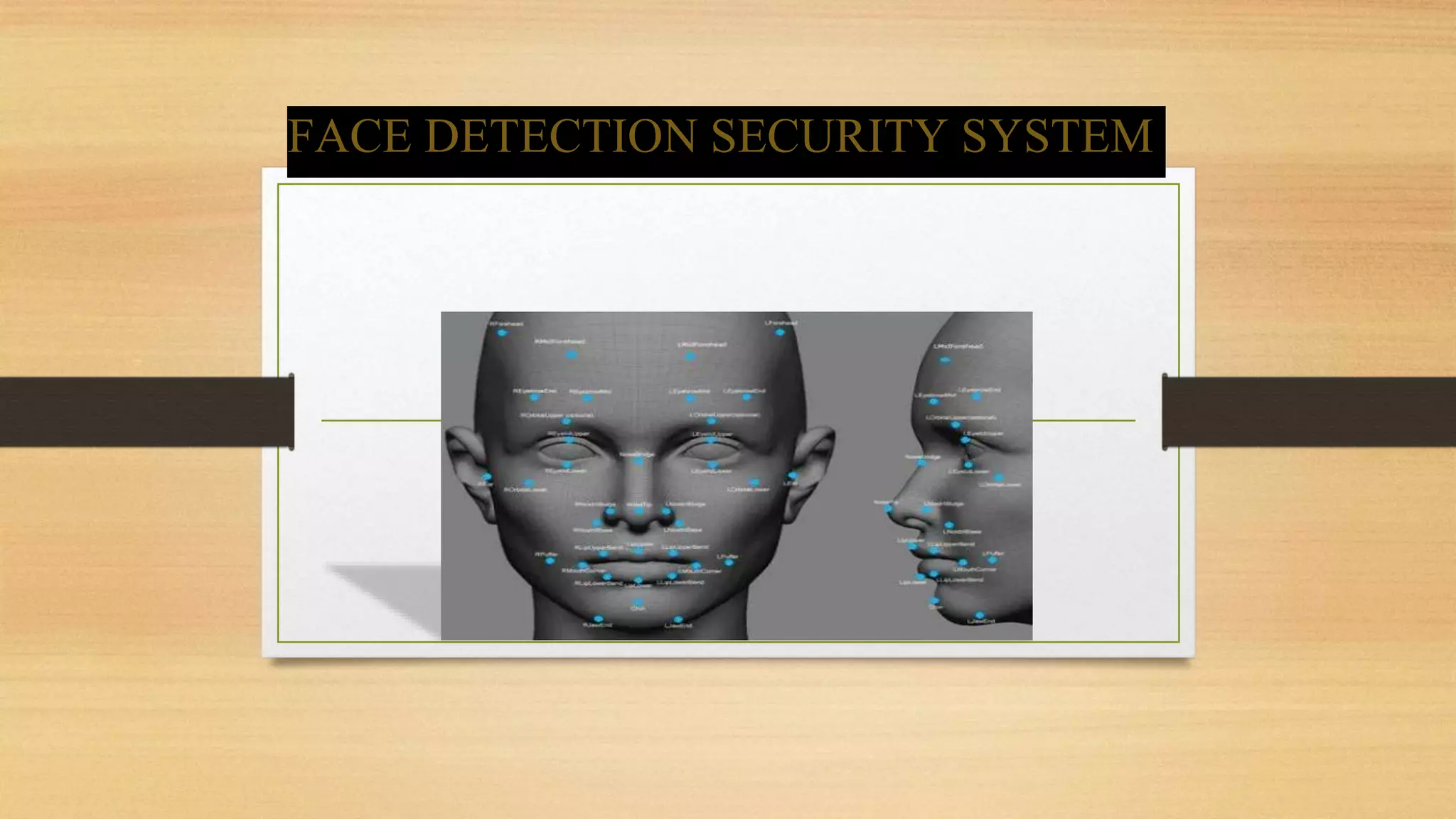
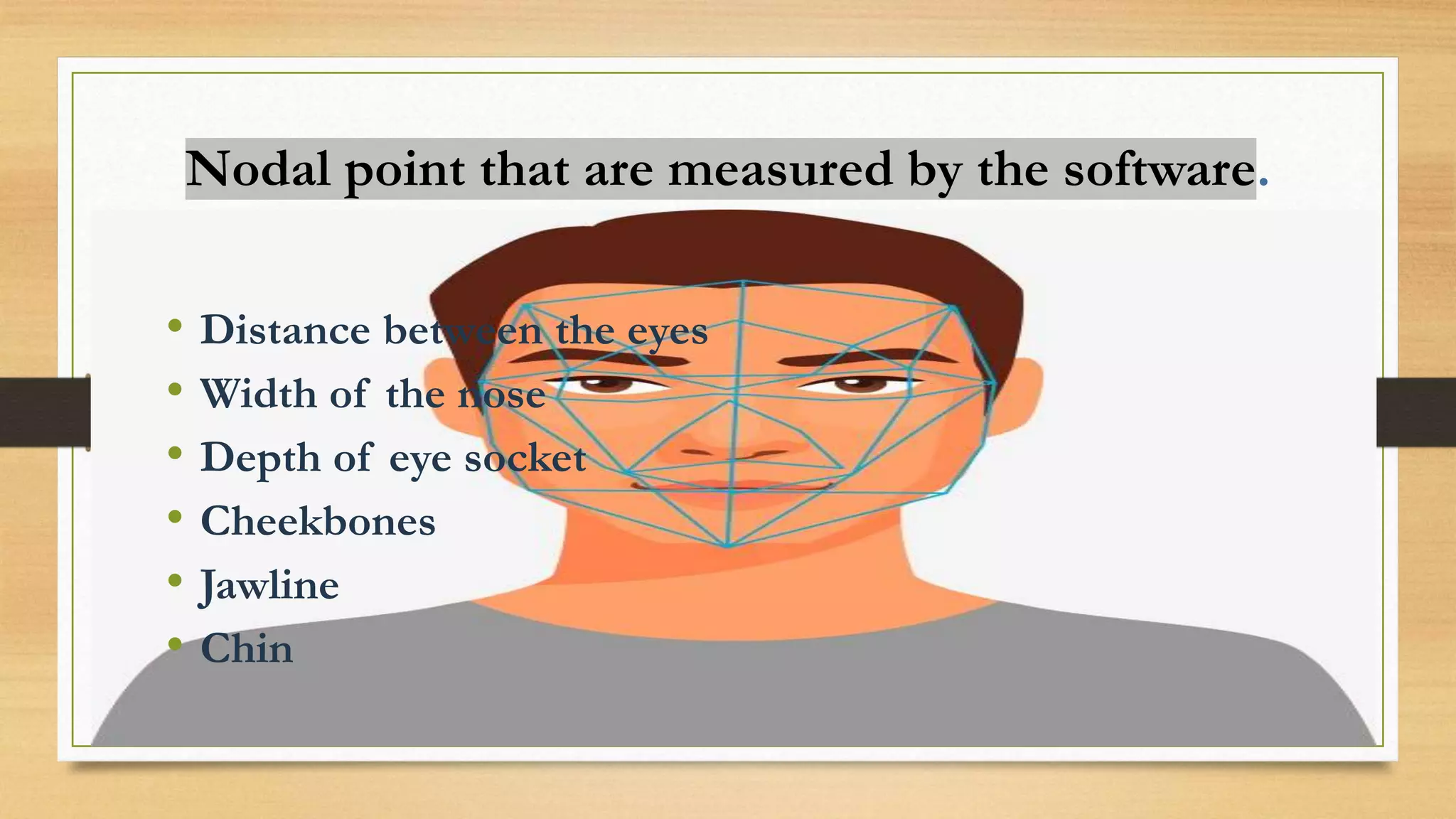
The document discusses the implementation and benefits of a face detection security system aimed at protecting assets and enhancing user privacy. It highlights the advantages of face recognition technology, such as requiring no user interaction and providing quick and accurate identification, while also acknowledging challenges like the need for high-quality images and environmental factors that may affect accuracy. Overall, the system is positioned as a powerful alternative to traditional biometric methods, with potential applications in various security contexts.