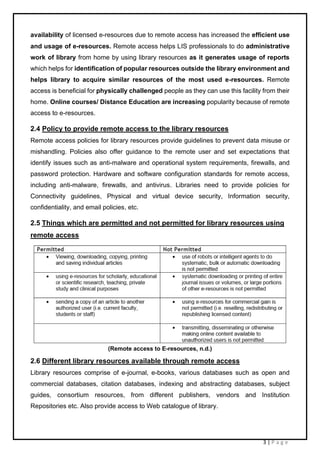
Remote access software allows users to access a library's electronic resources from off-campus locations. It provides a single login interface for accessing subscribed e-journals, e-books, databases, and other resources. Ezproxy is one example of remote access software that libraries can install on their servers. It uses IP authentication and encryption to securely grant remote users access to licensed electronic content. Remote access software increases the availability and usage of library resources by allowing 24/7 access from any internet-connected device.