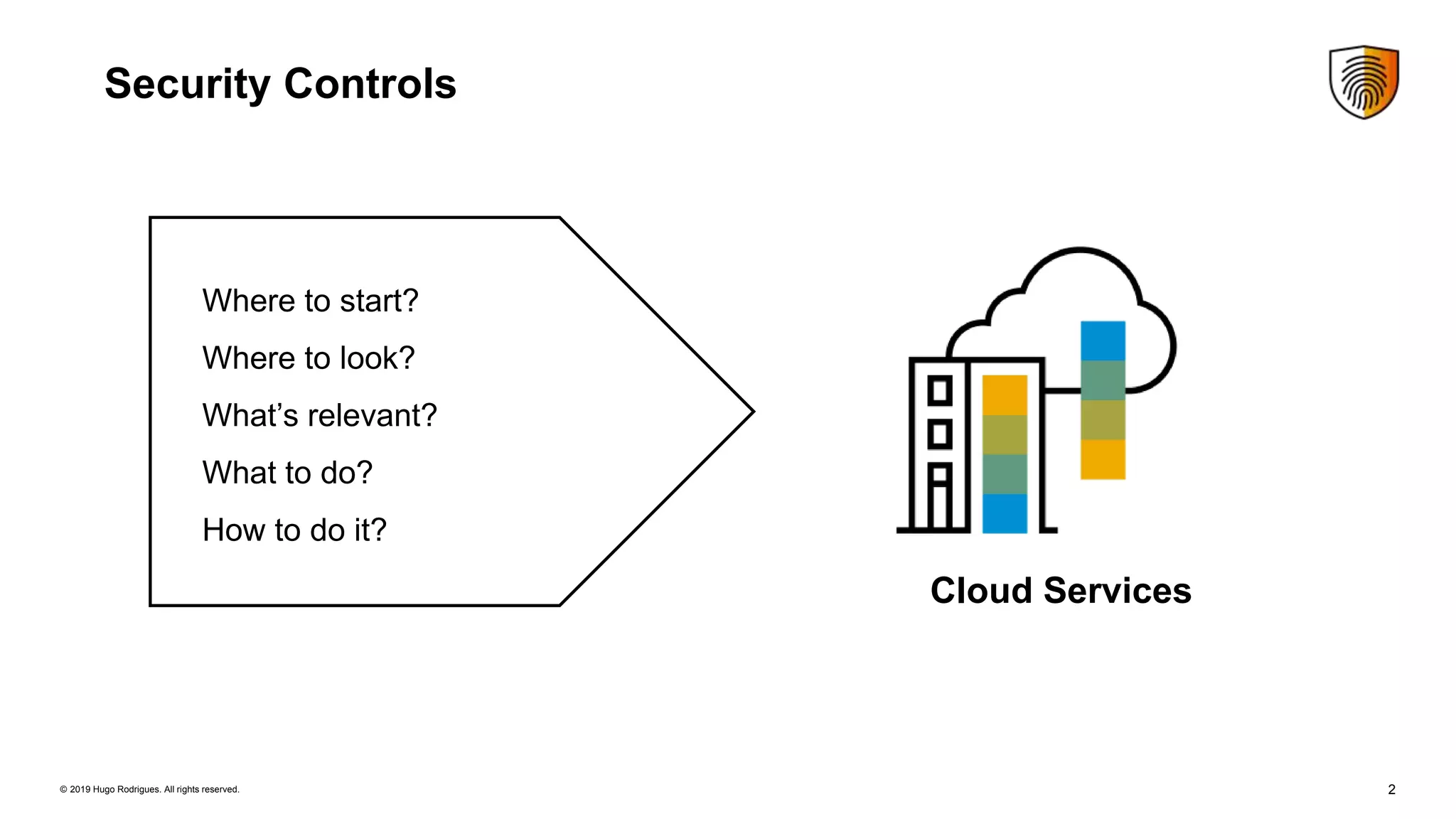
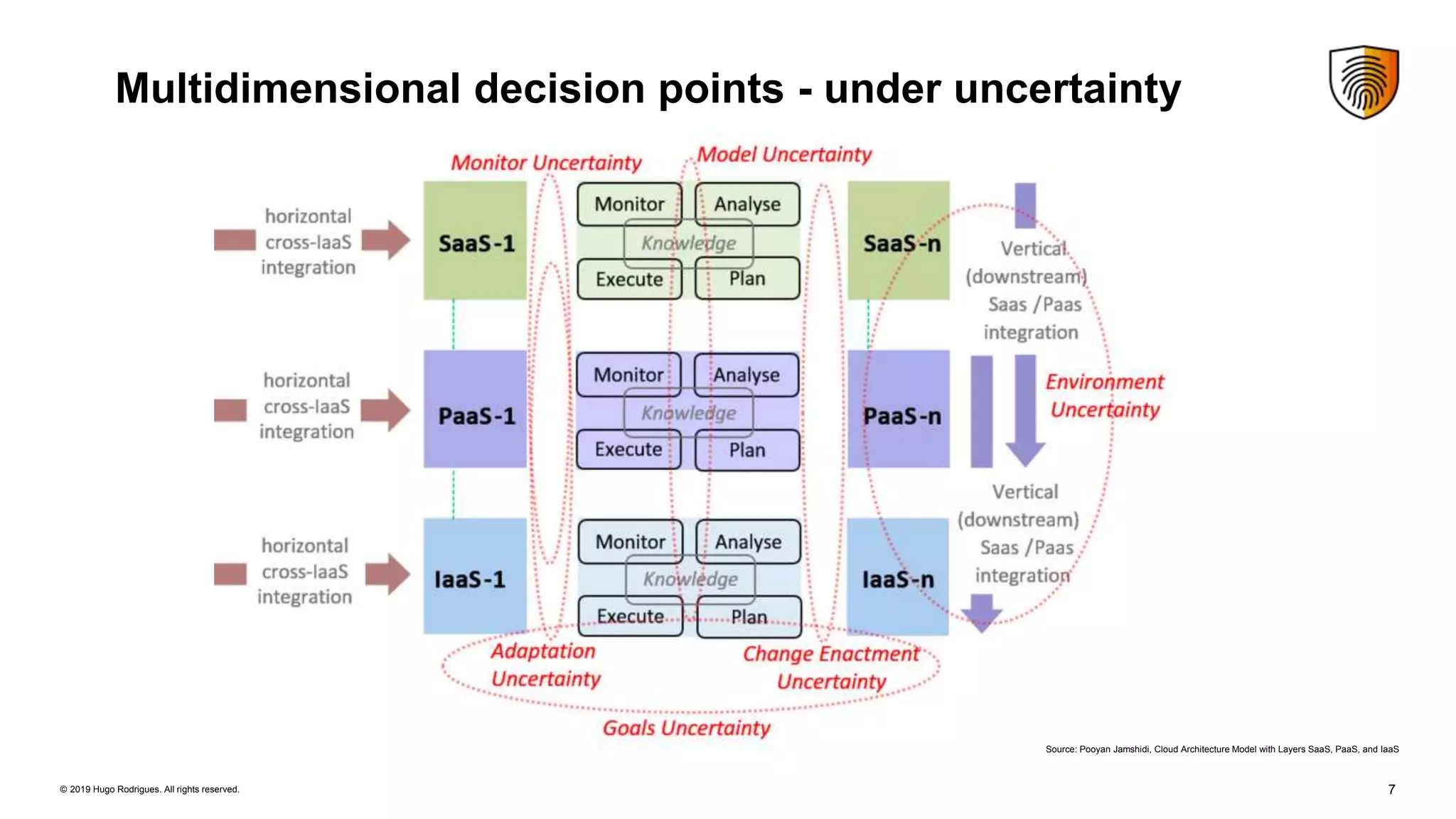
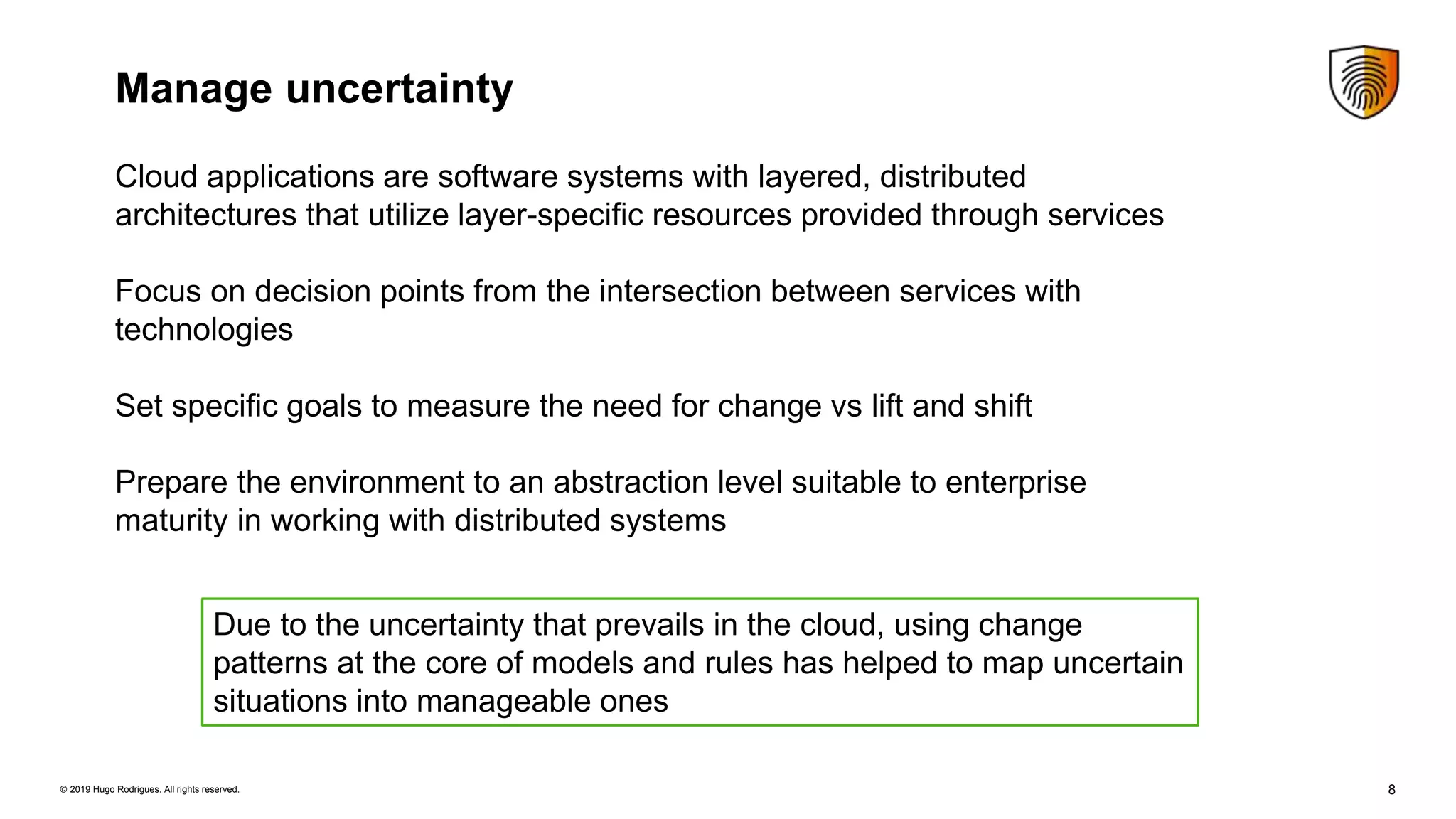
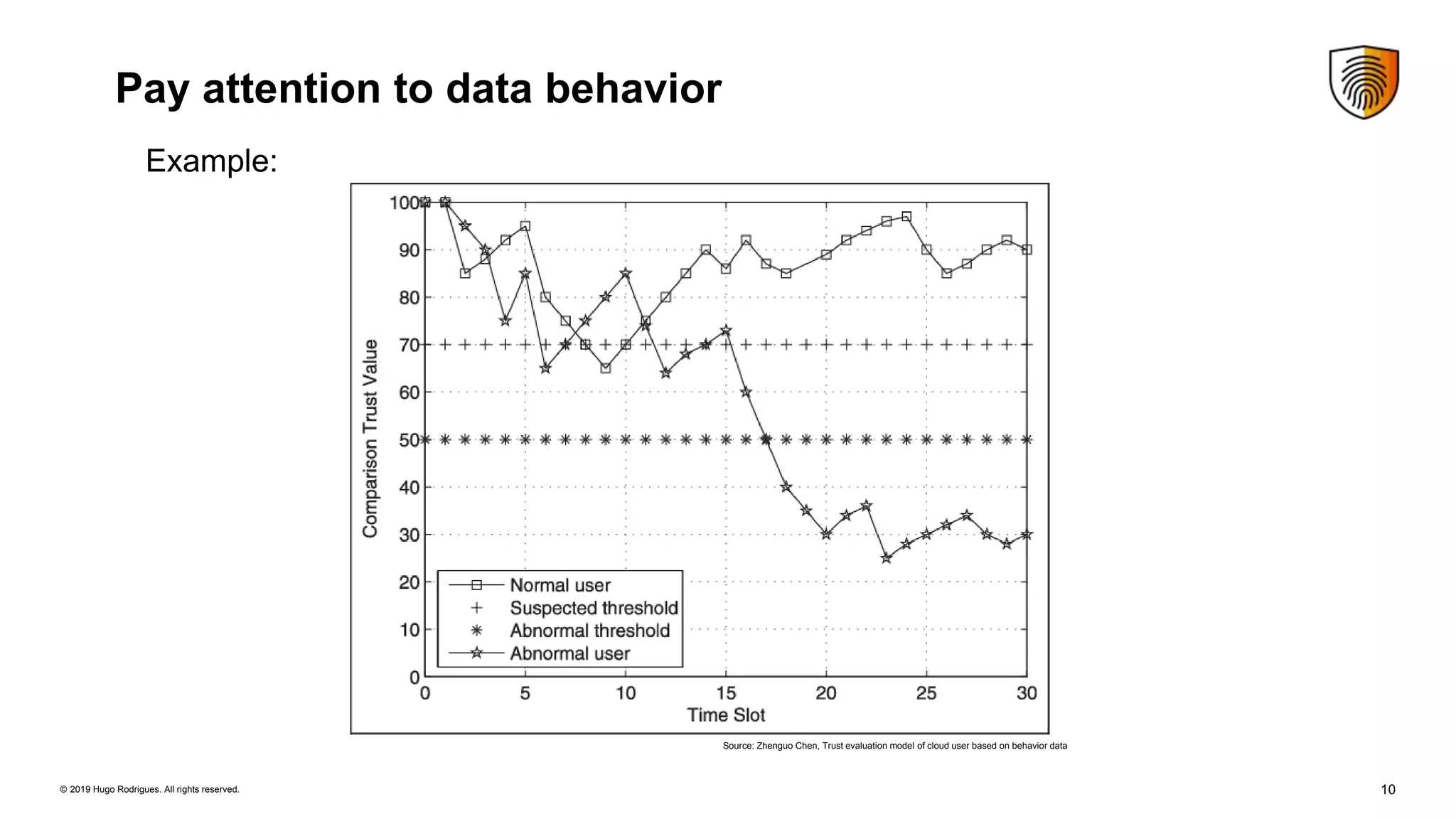
Evolution of Security Controls Towards Cloud Services discusses security controls for cloud services. It summarizes the Cloud Security Alliance's Security Trust Assurance and Risk framework for guiding cloud vendors and assessing cloud security risks. It also discusses the Cloud Controls Matrix version 3.0 which provides guidance on implementing security controls in cloud environments based on 16 security domains. Managing uncertainty is key when using cloud services, and formal verification methods can help ensure security. Continuous monitoring of cloud environments helps gain visibility and detect security issues.