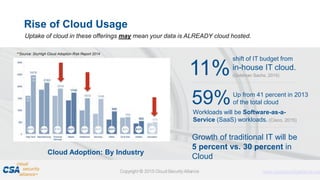
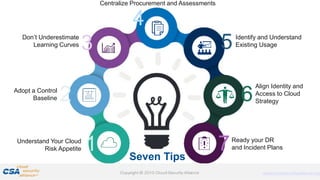
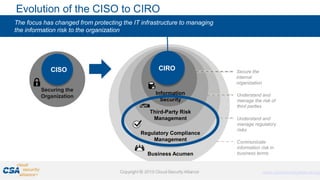
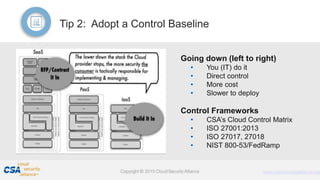
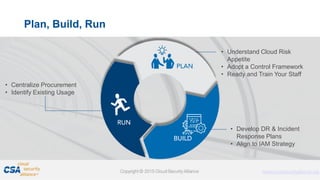
The document discusses trends in enterprise adoption of cloud computing and provides seven tips for managing security risks associated with cloud adoption. It notes that not adopting cloud is becoming a competitive disadvantage. The seven tips are to understand risk appetite, adopt a control baseline, don't underestimate learning curves, centralize procurement and assessments, identify existing usage, align identity and access strategies, and ready disaster recovery and incident response plans. The document emphasizes that security fundamentals extend to cloud environments and organizations should leverage frameworks for controls and engage stakeholders to manage risks.