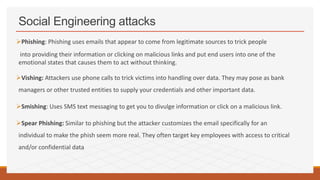
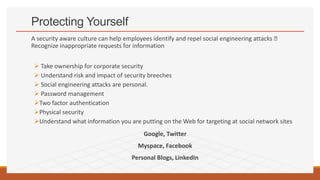
The document discusses the skills required to become an ethical hacker. It outlines several important skills including programming languages, computer skills, database skills, SQL skills, Linux skills, and social engineering skills. Specific programming languages that are useful for hacking include HTML, JavaScript, PHP, SQL, Python, Ruby, Bash, Perl, C/C++, and Java. Social engineering involves manipulating users to gain access to confidential information and can include techniques like phishing and vishing. Protecting against social engineering requires security awareness training for employees.