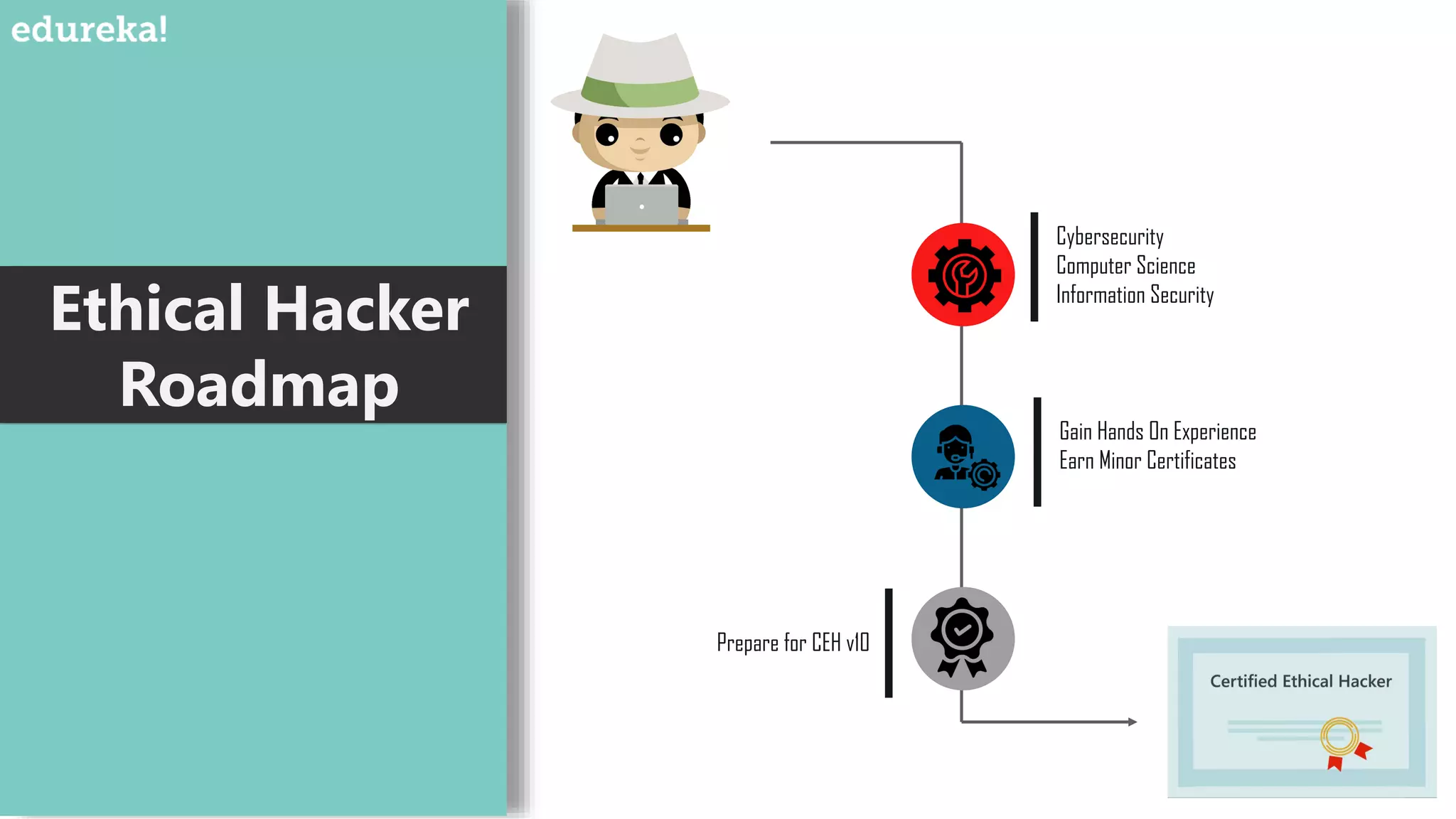
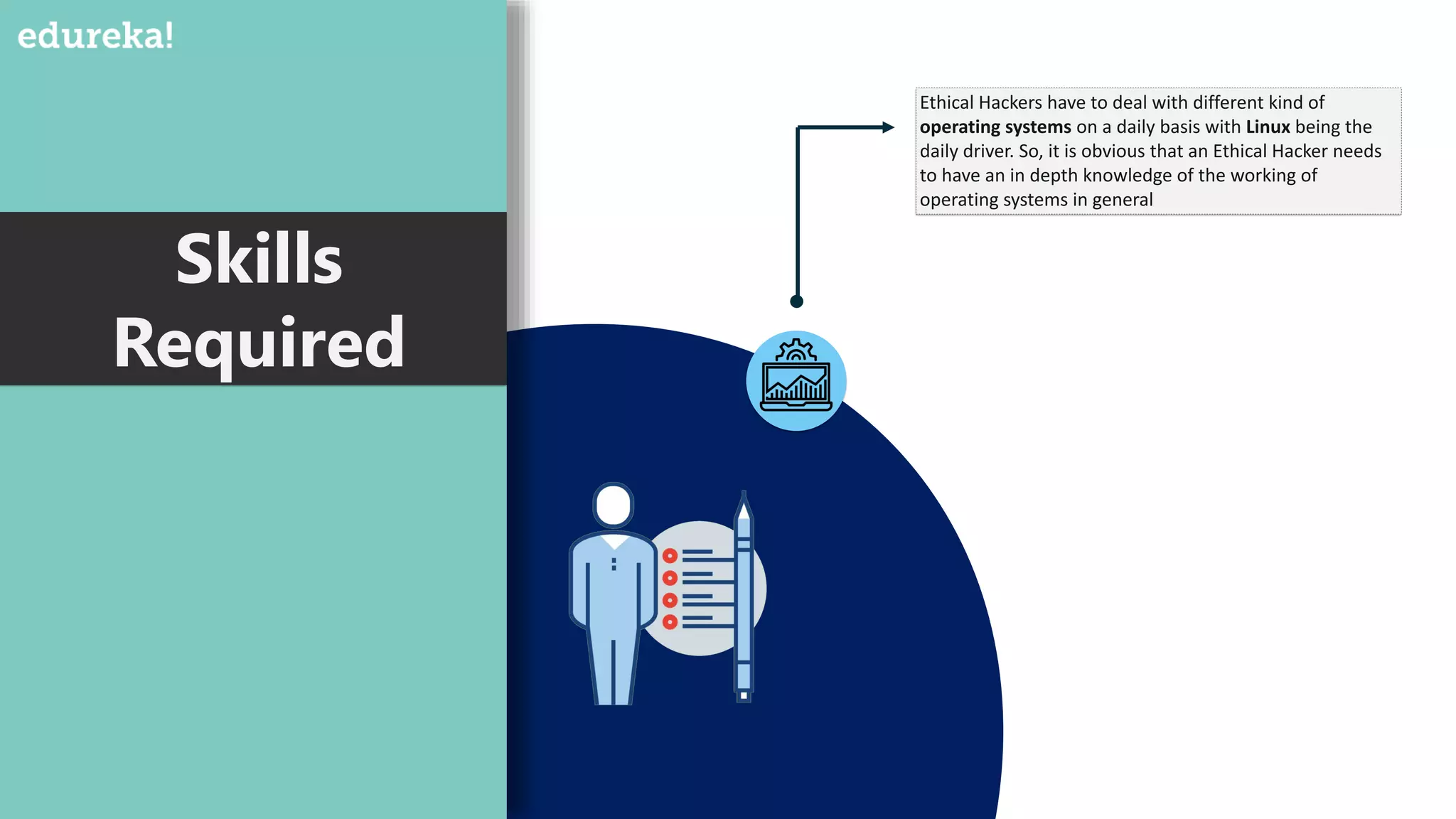
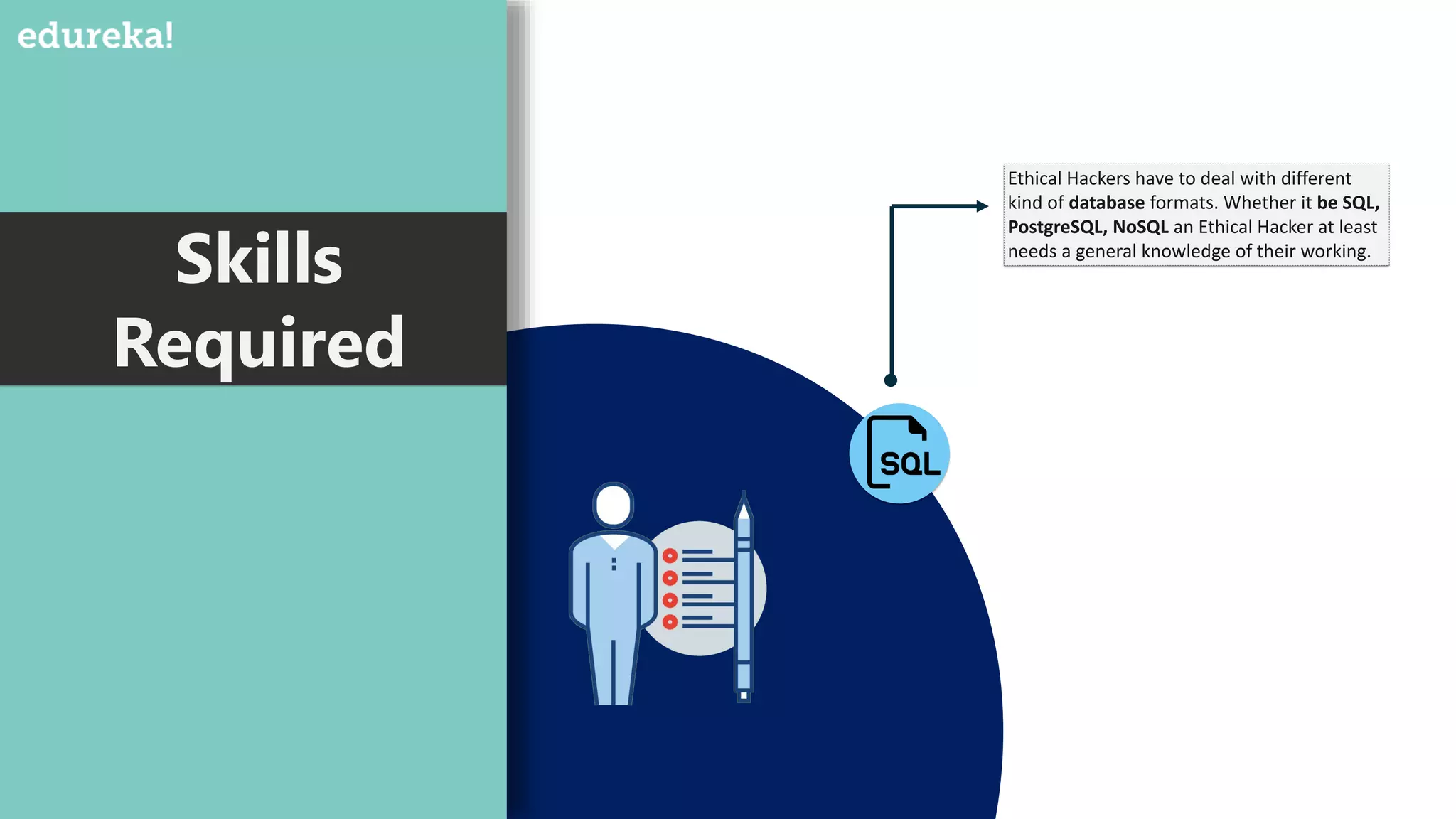
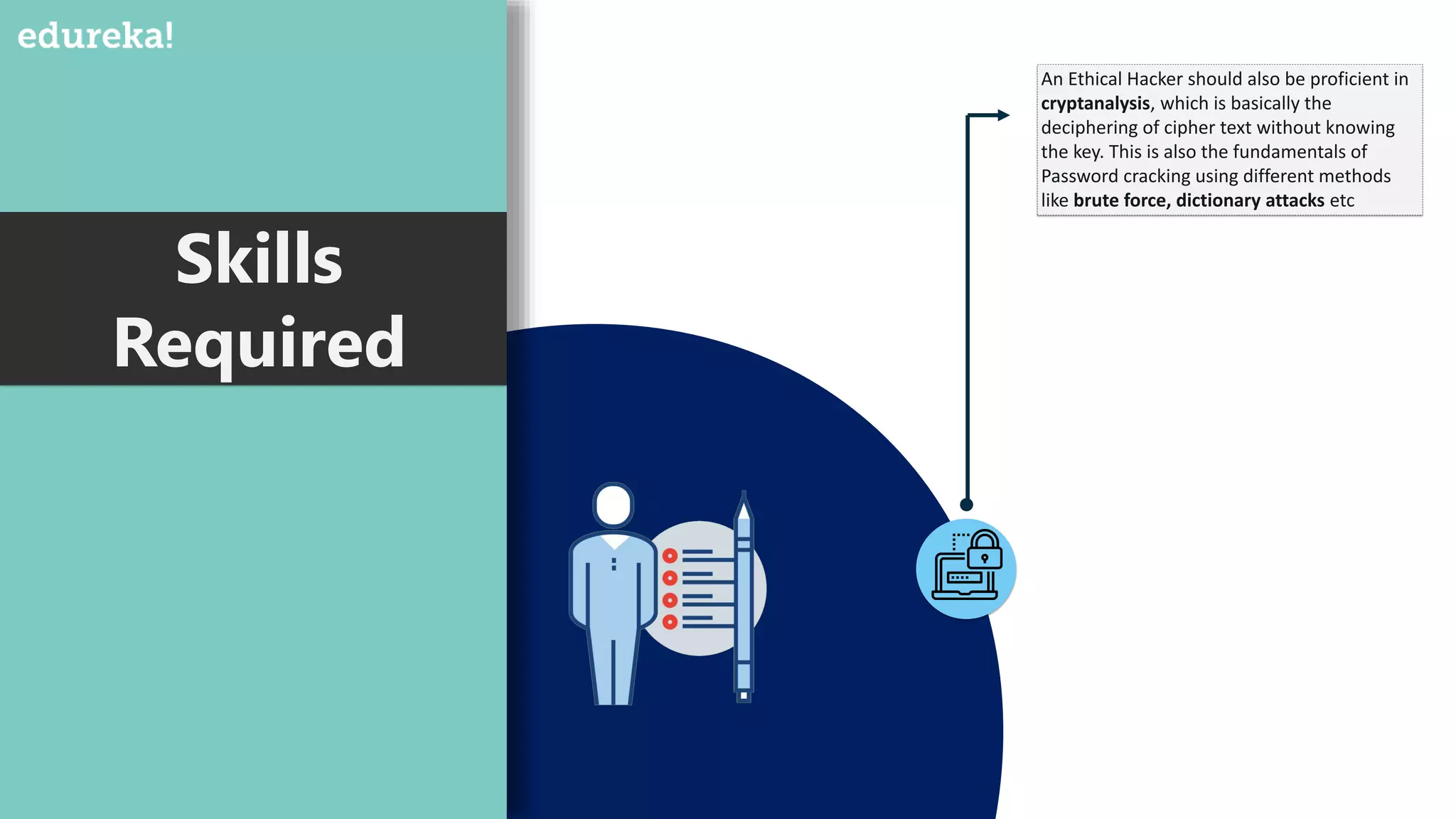
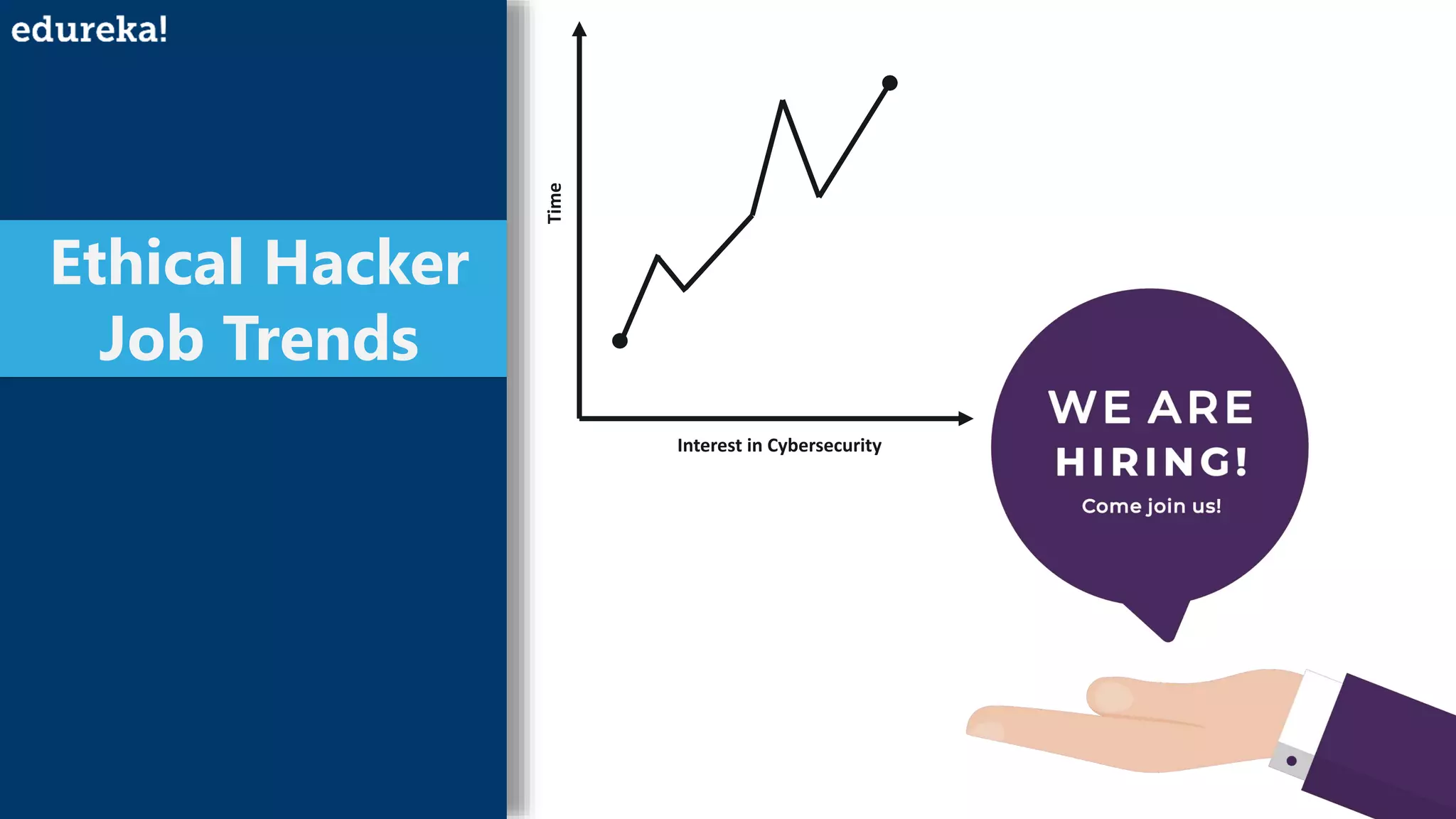
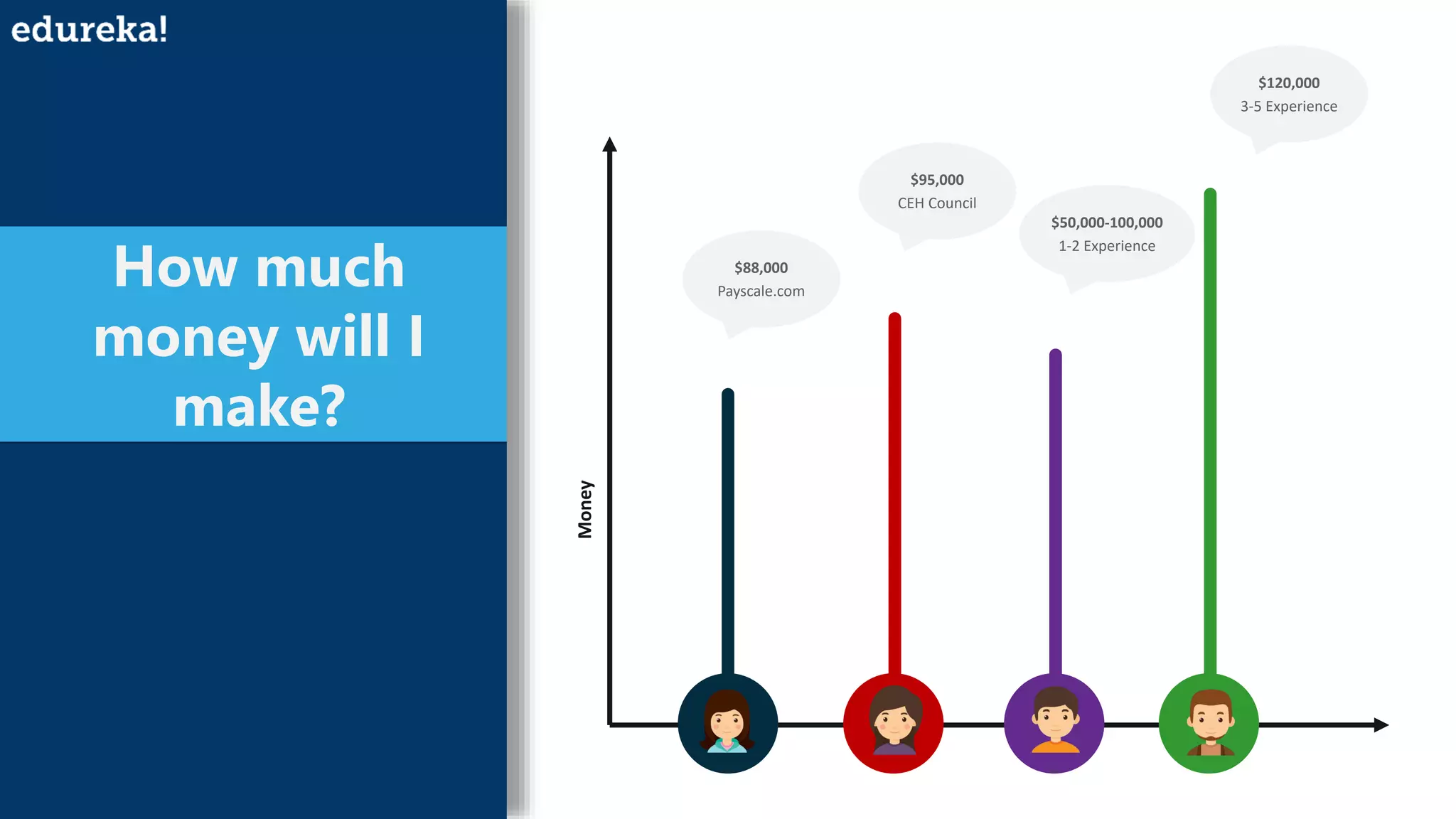
An ethical hacker, or white hat hacker, is a cybersecurity expert who tests systems for vulnerabilities with permission, employing various techniques such as port scanning and social engineering. They must have a broad skill set, including knowledge of operating systems, database formats, cryptanalysis, and custom software development, to effectively prevent and respond to security threats. Job trends show a salary range from $50,000 to $120,000 depending on experience, reflecting the high demand for skilled professionals in this field.