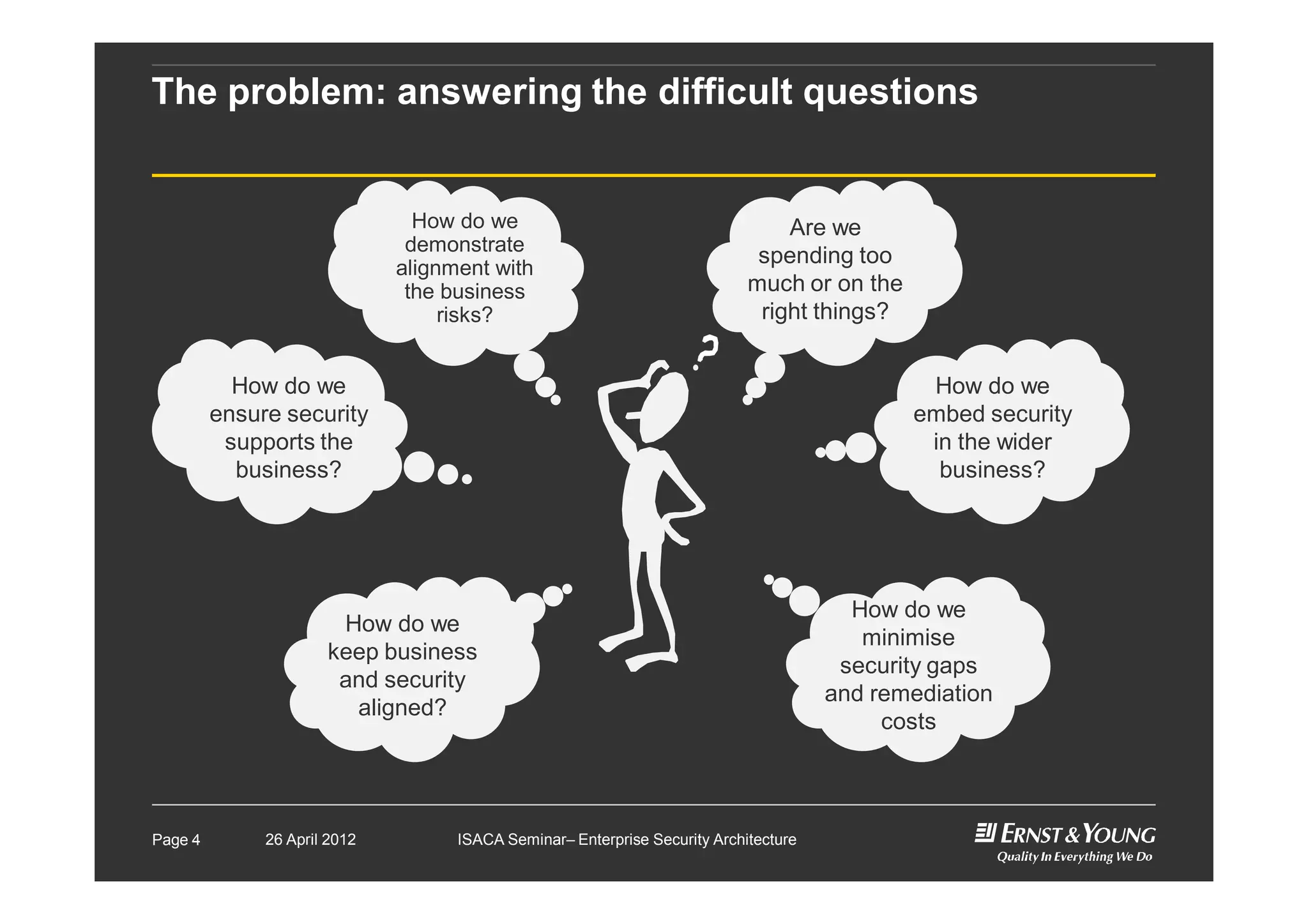
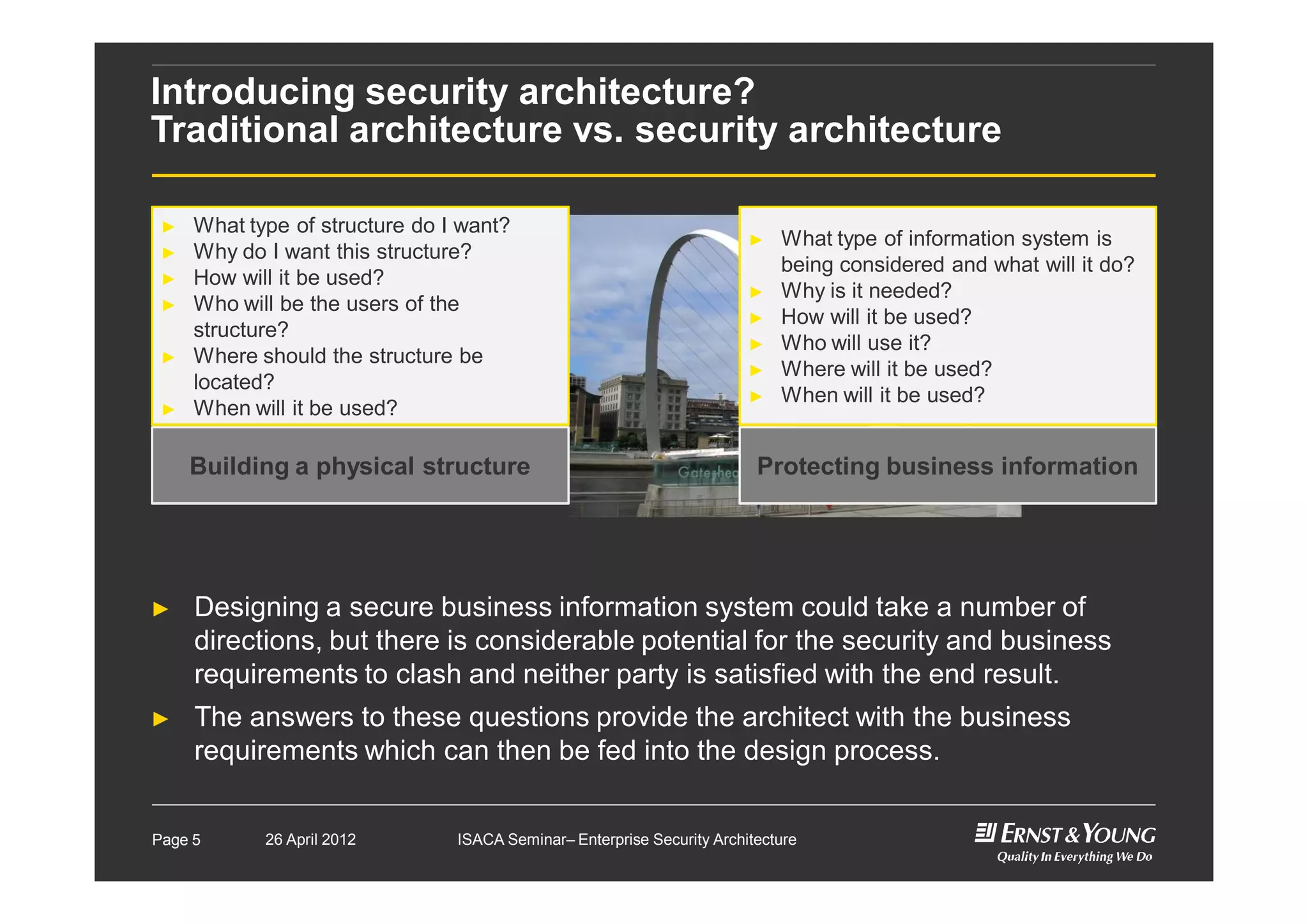
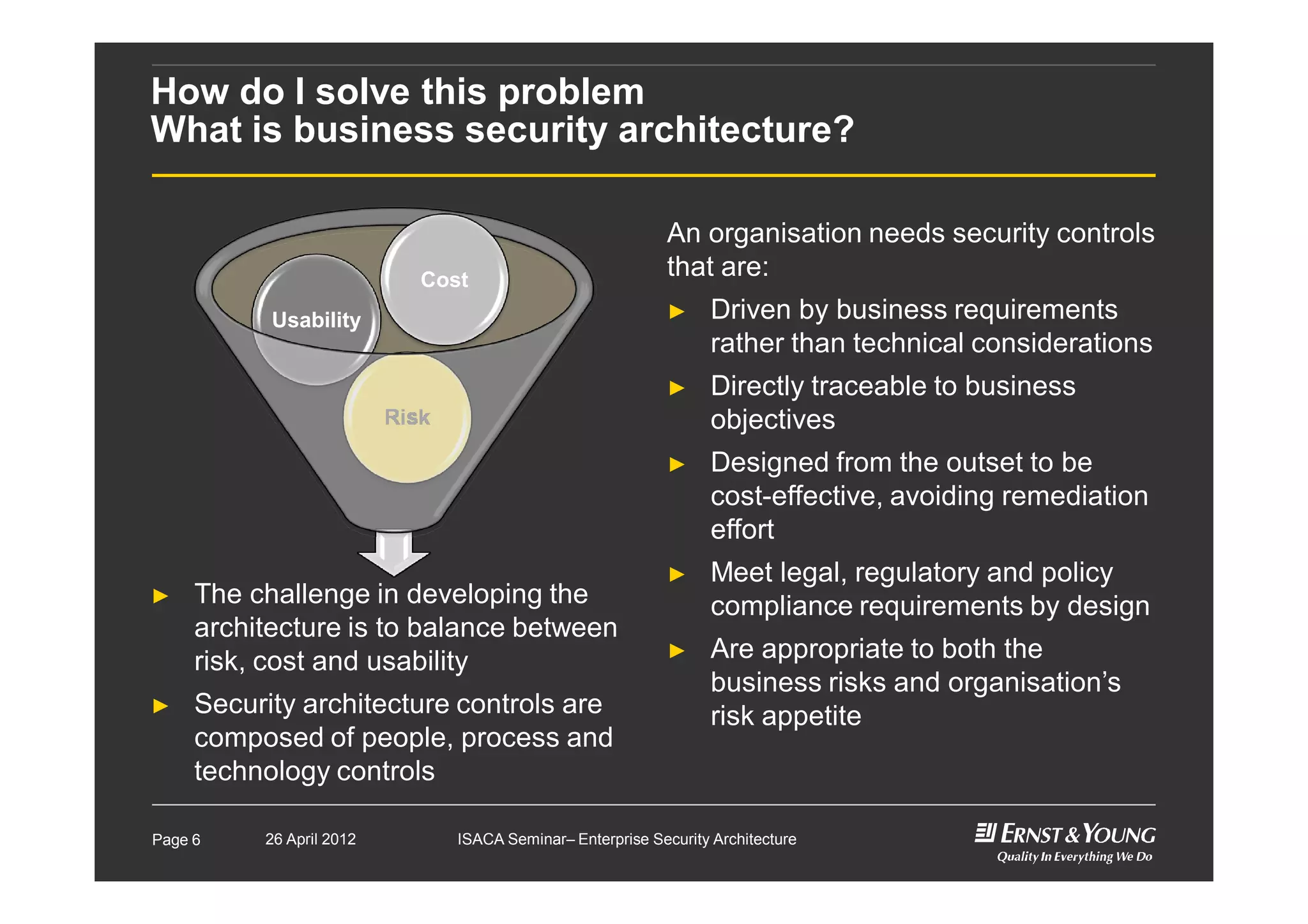
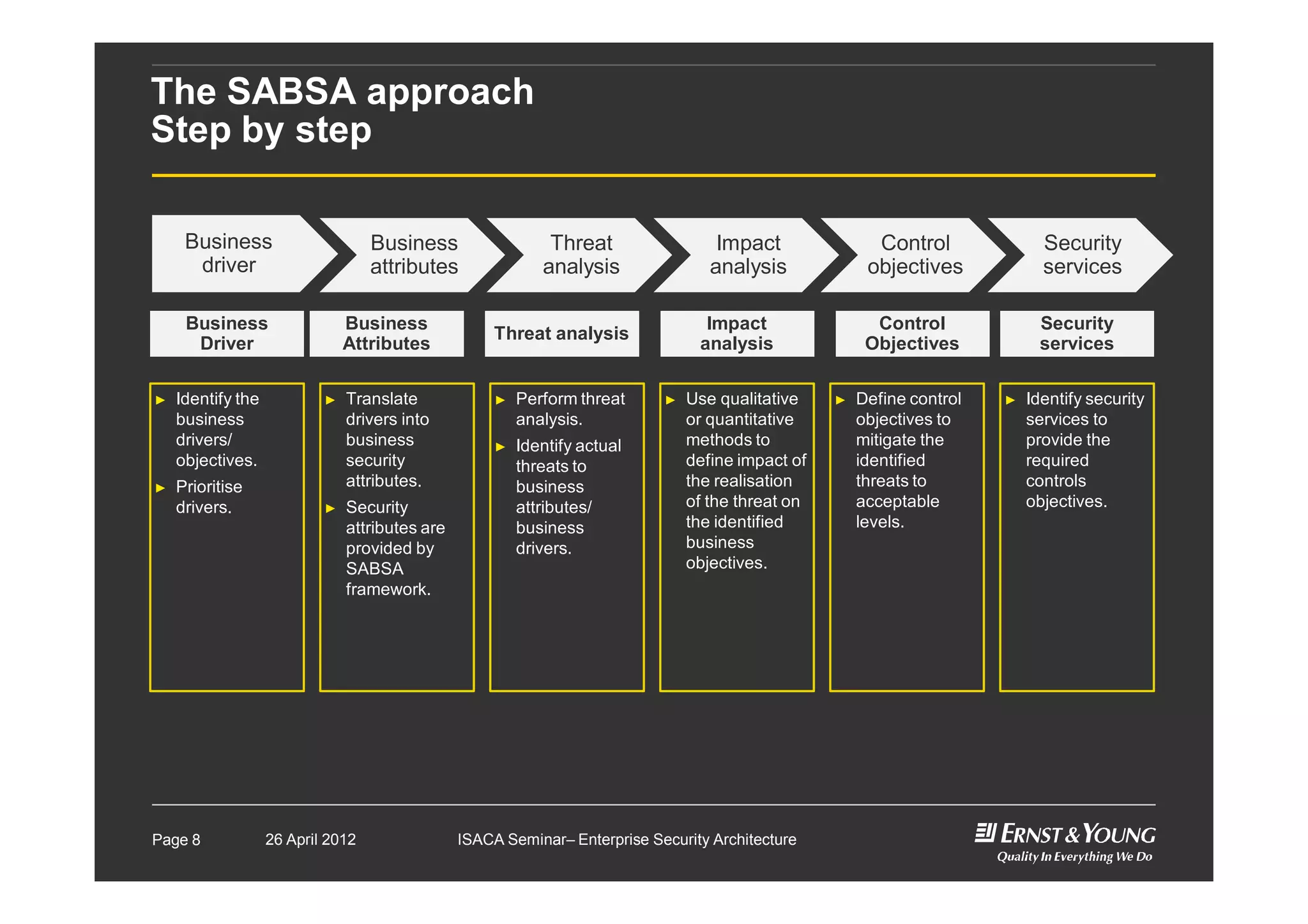
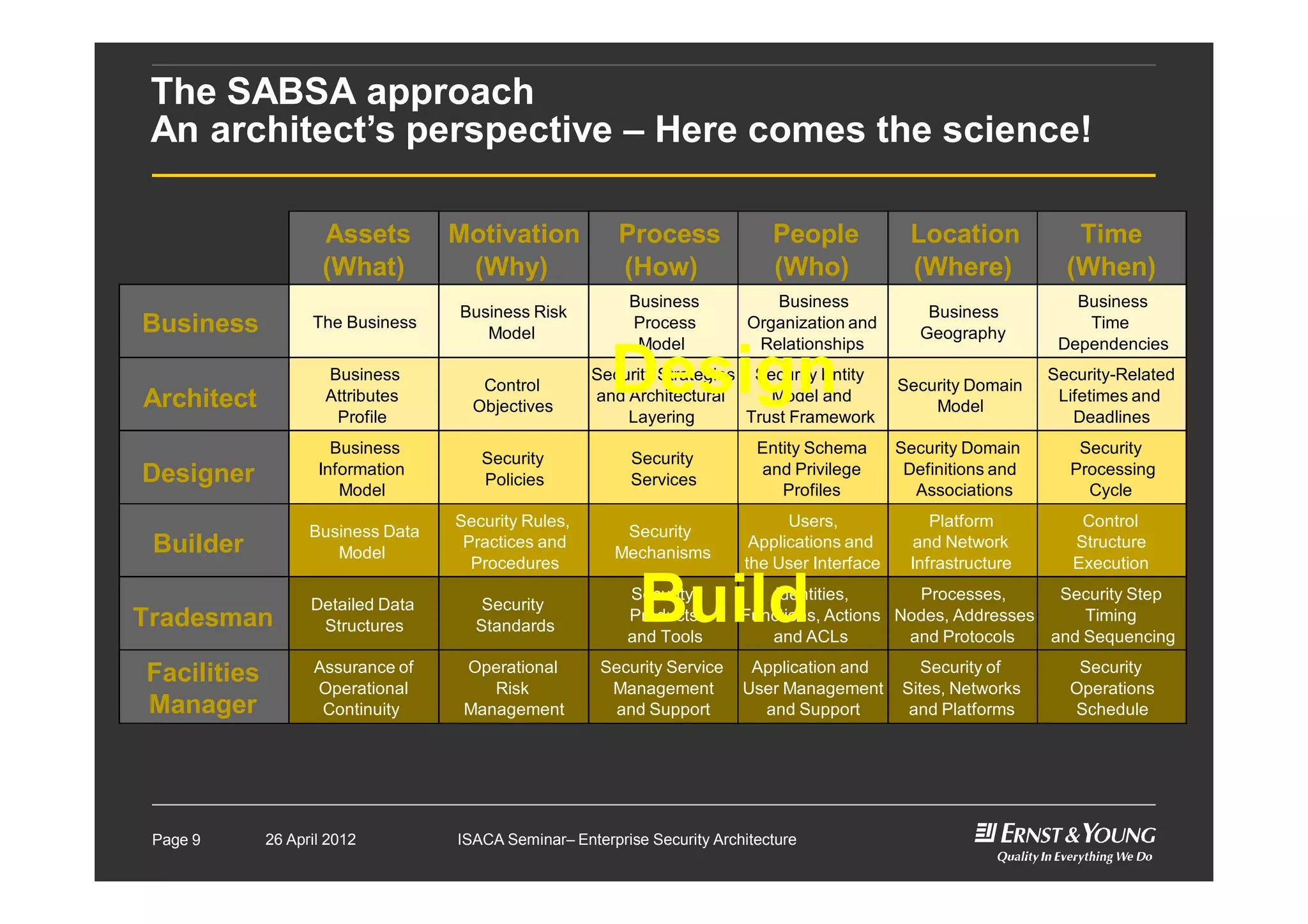
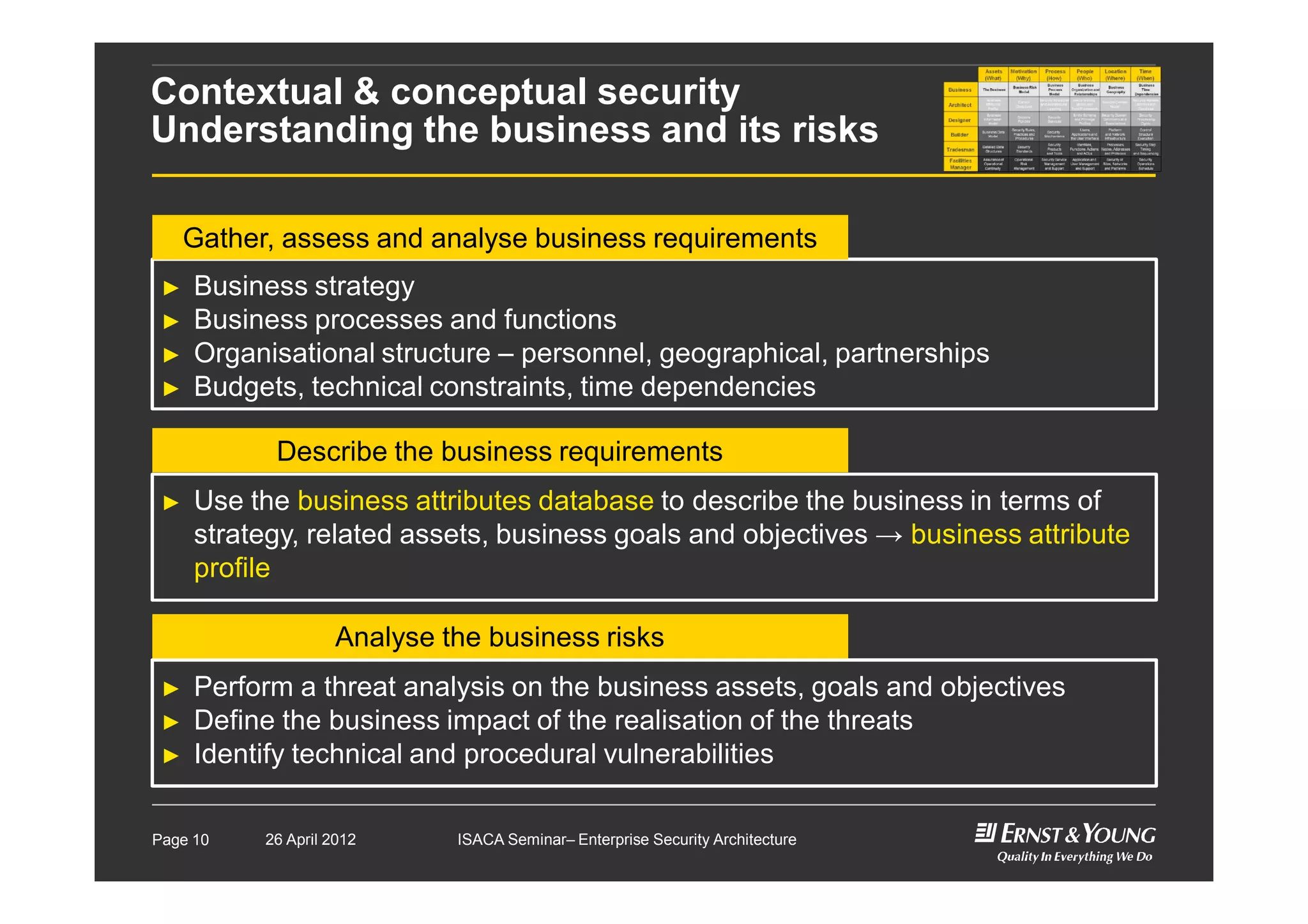
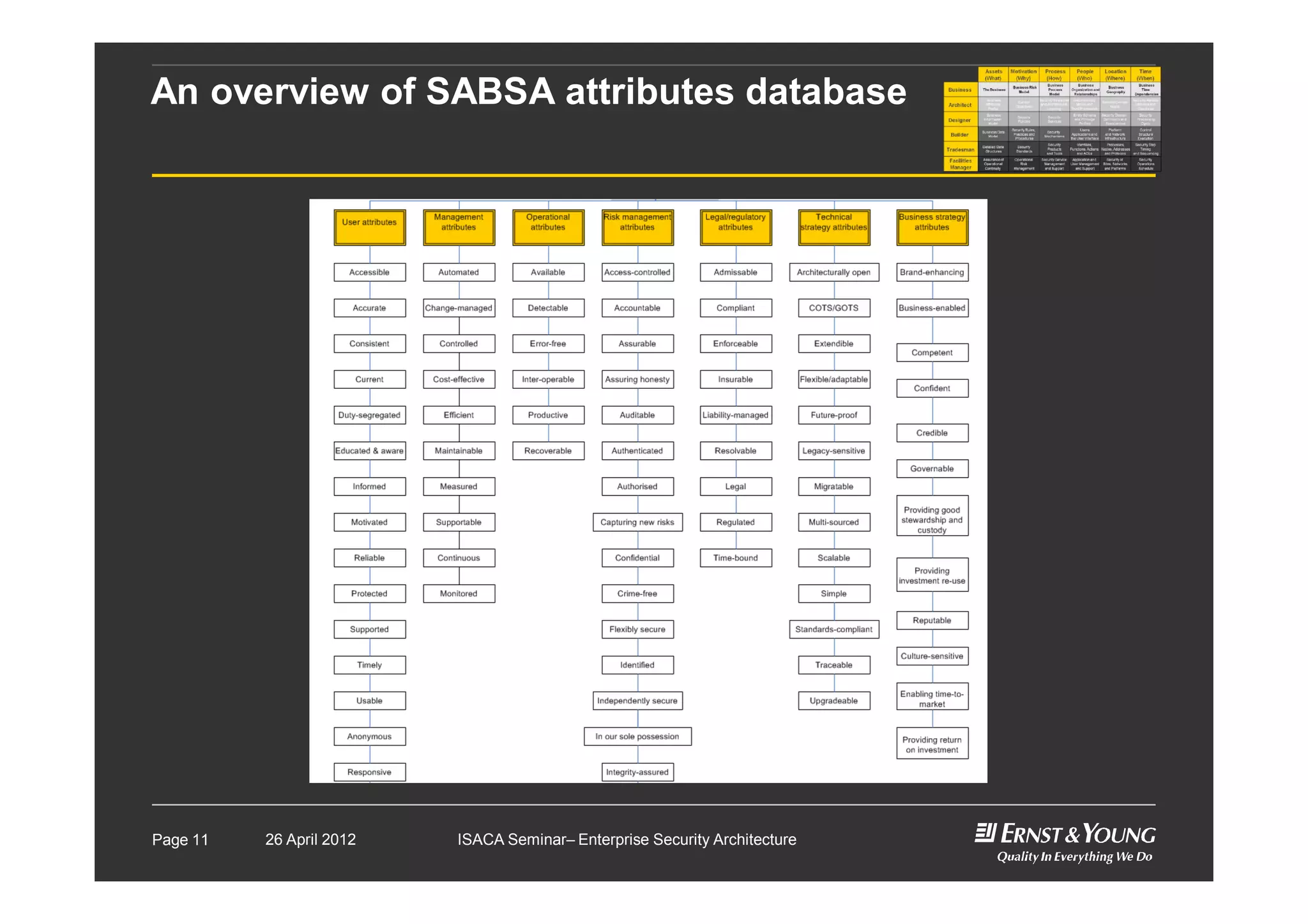
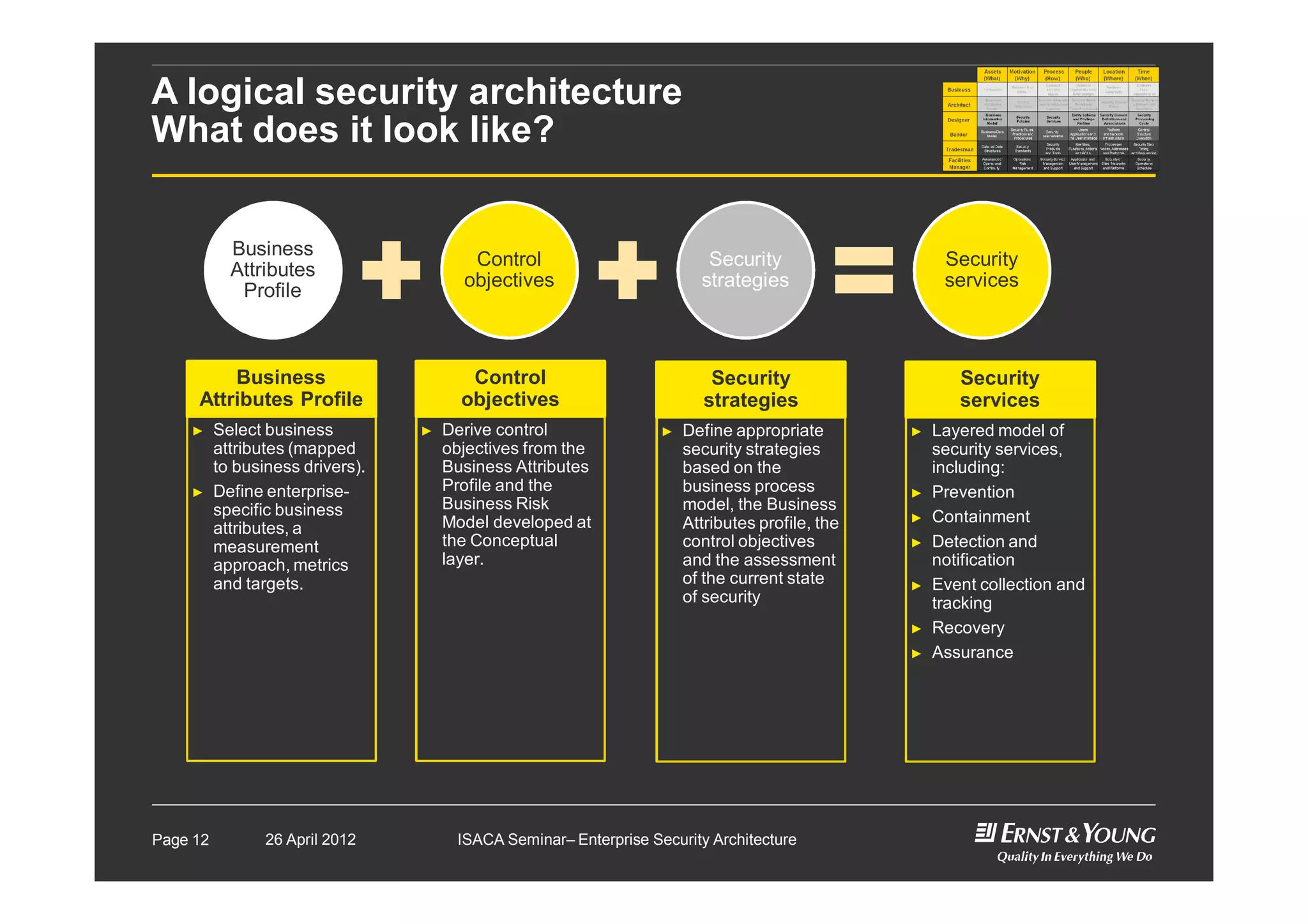
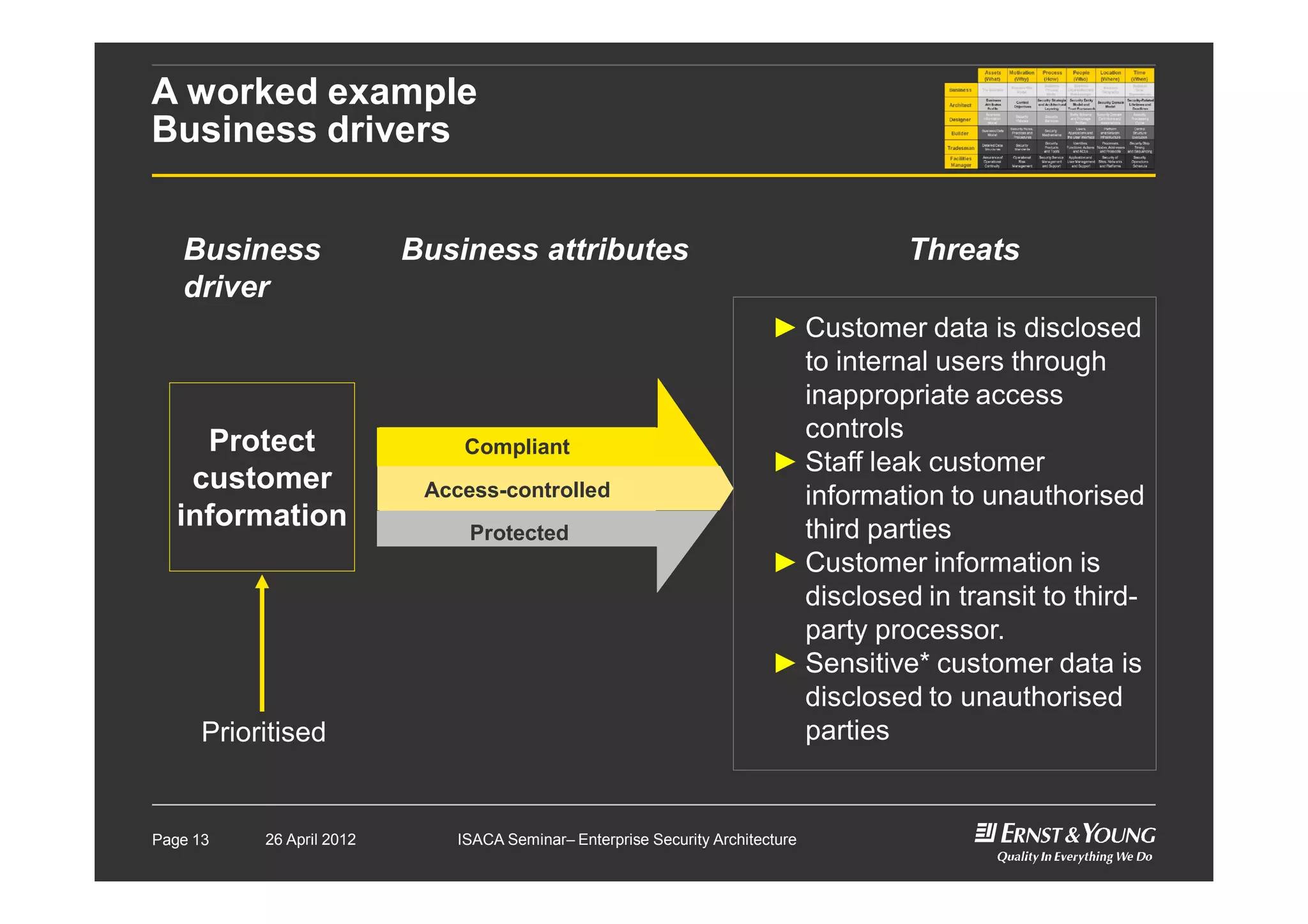
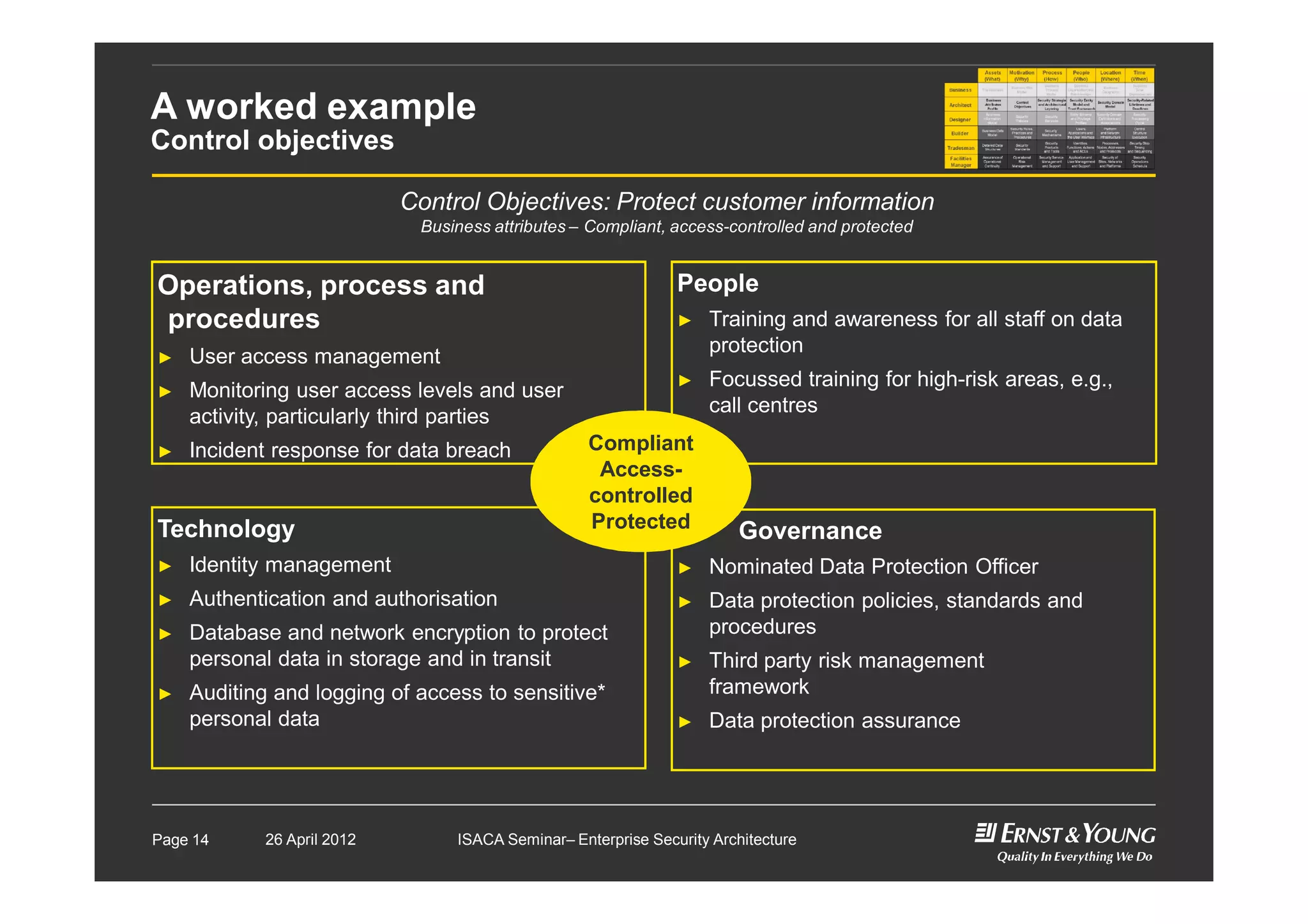
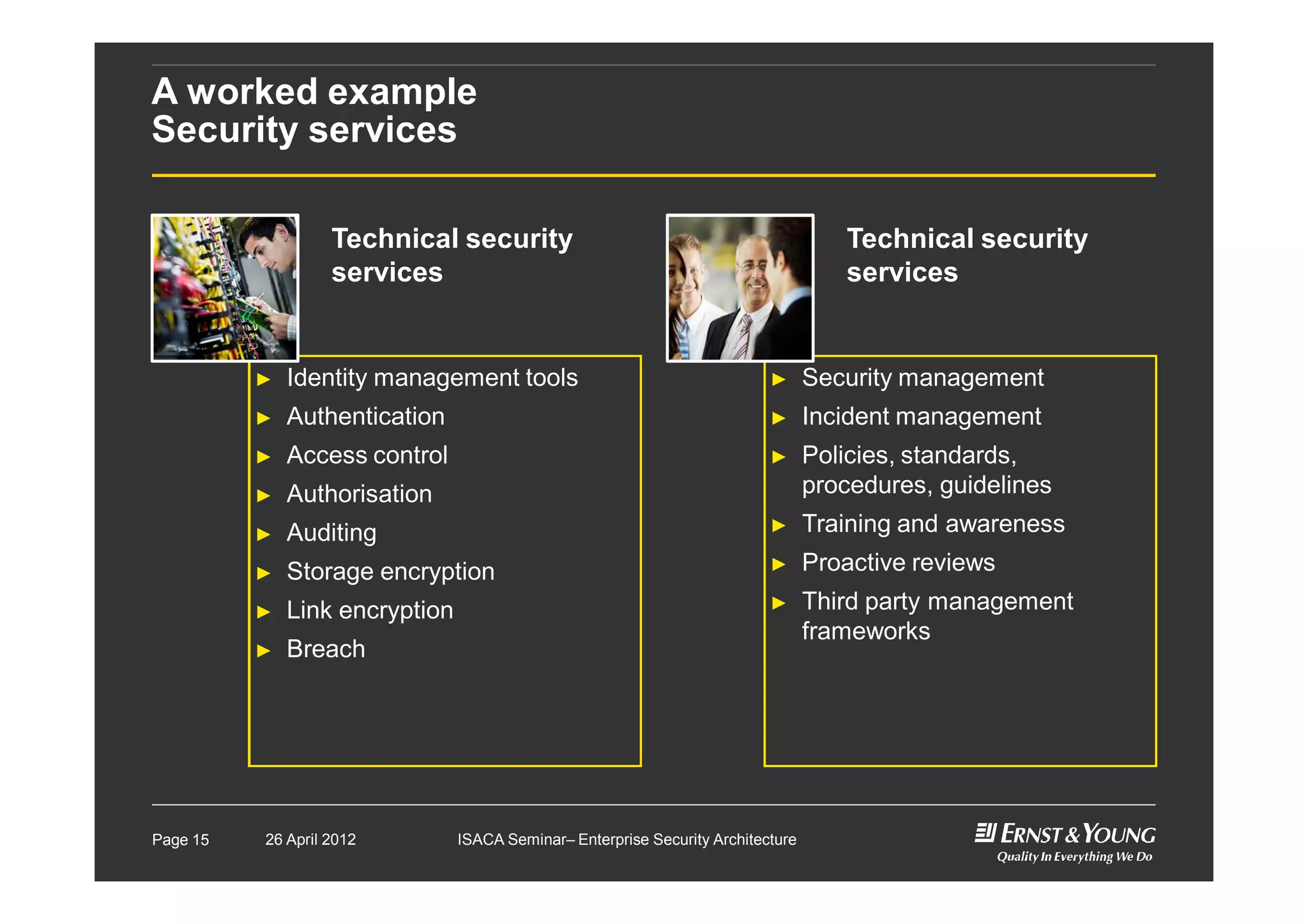
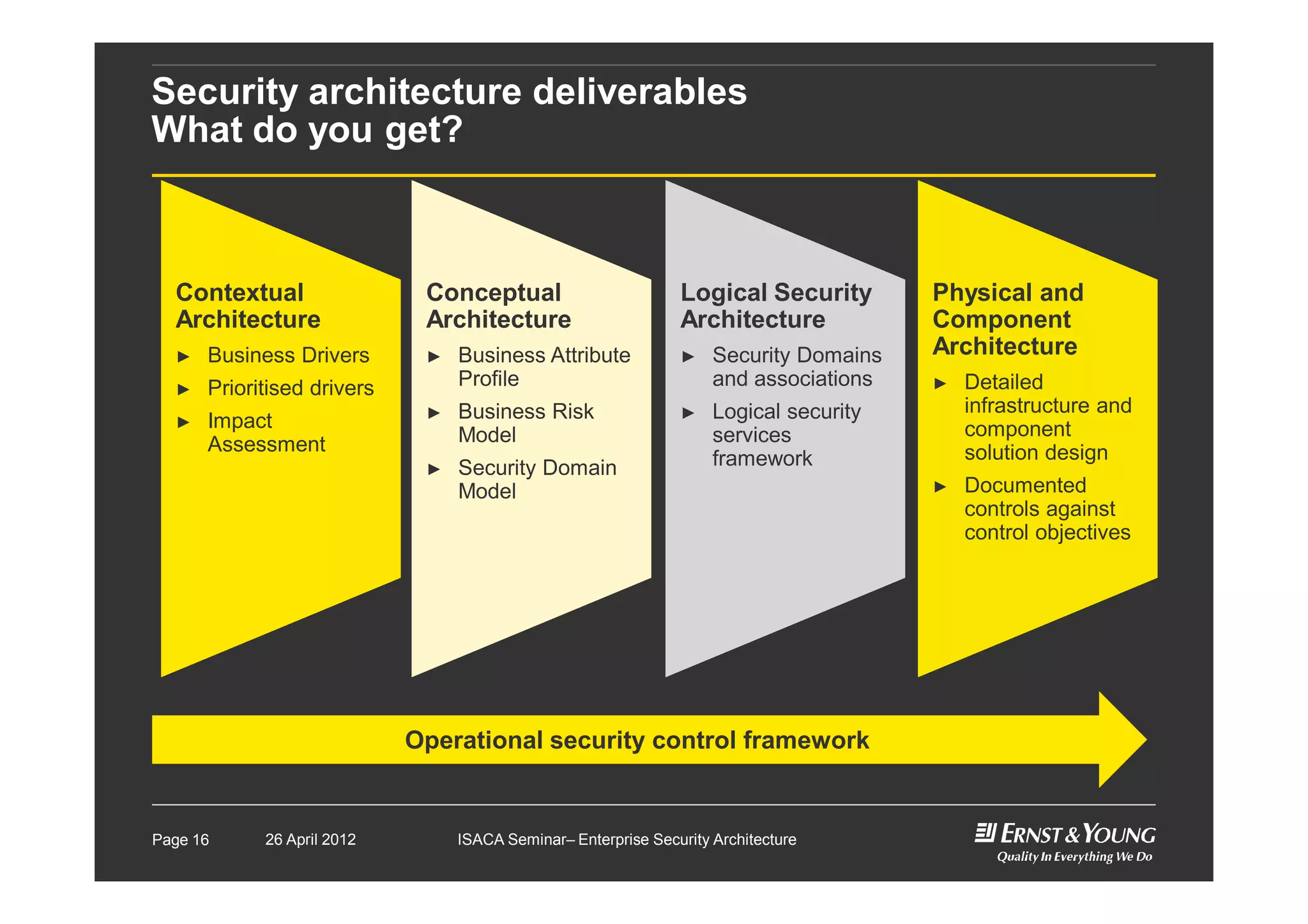
This document outlines an enterprise security architecture seminar. It introduces security architecture and the SABSA framework. SABSA is a step-by-step approach that involves identifying business drivers, attributes, threats, control objectives, and security services. A worked example is provided that protects customer information. The seminar covers developing a contextual and conceptual security understanding, logical security architecture components, and deliverables including control frameworks.