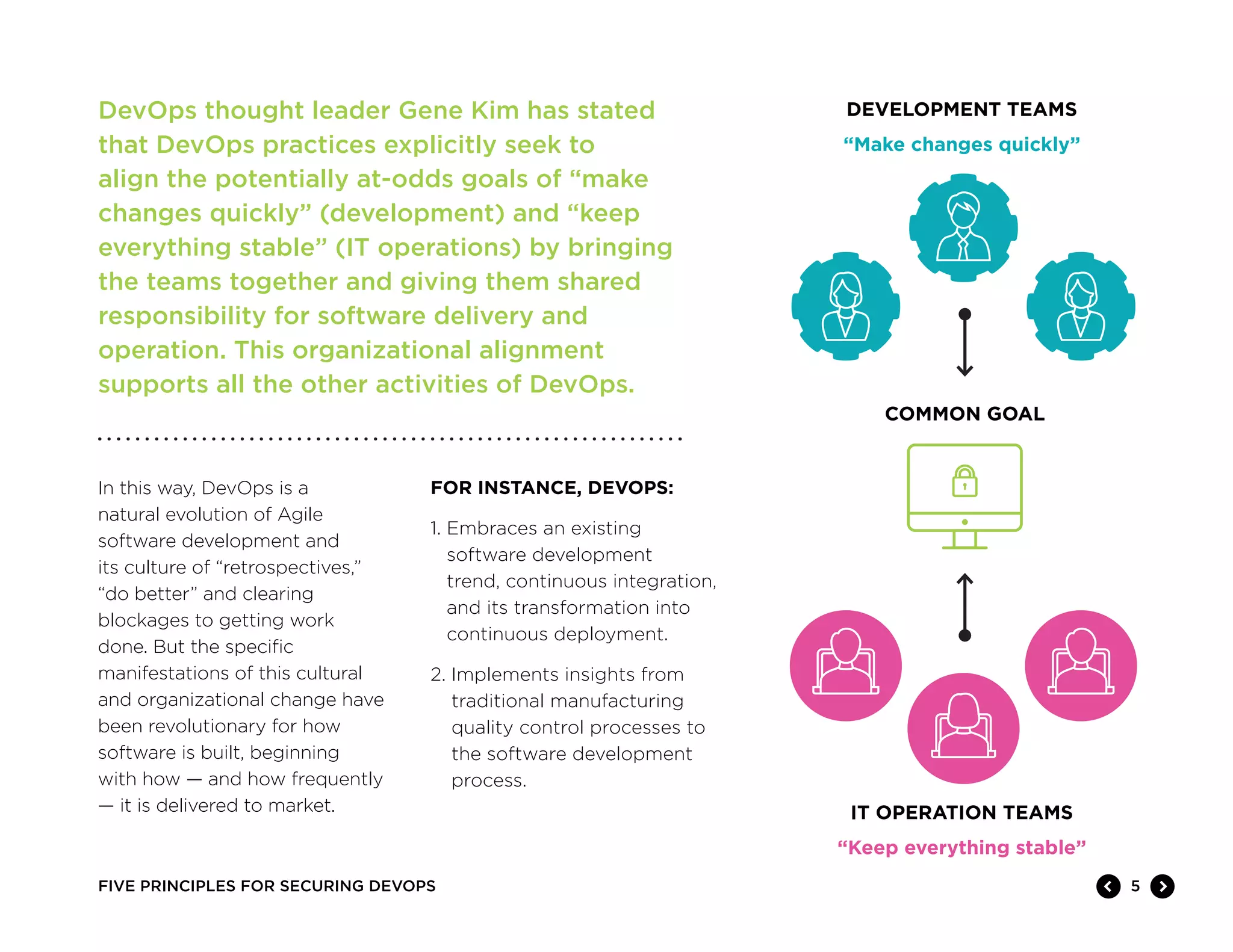
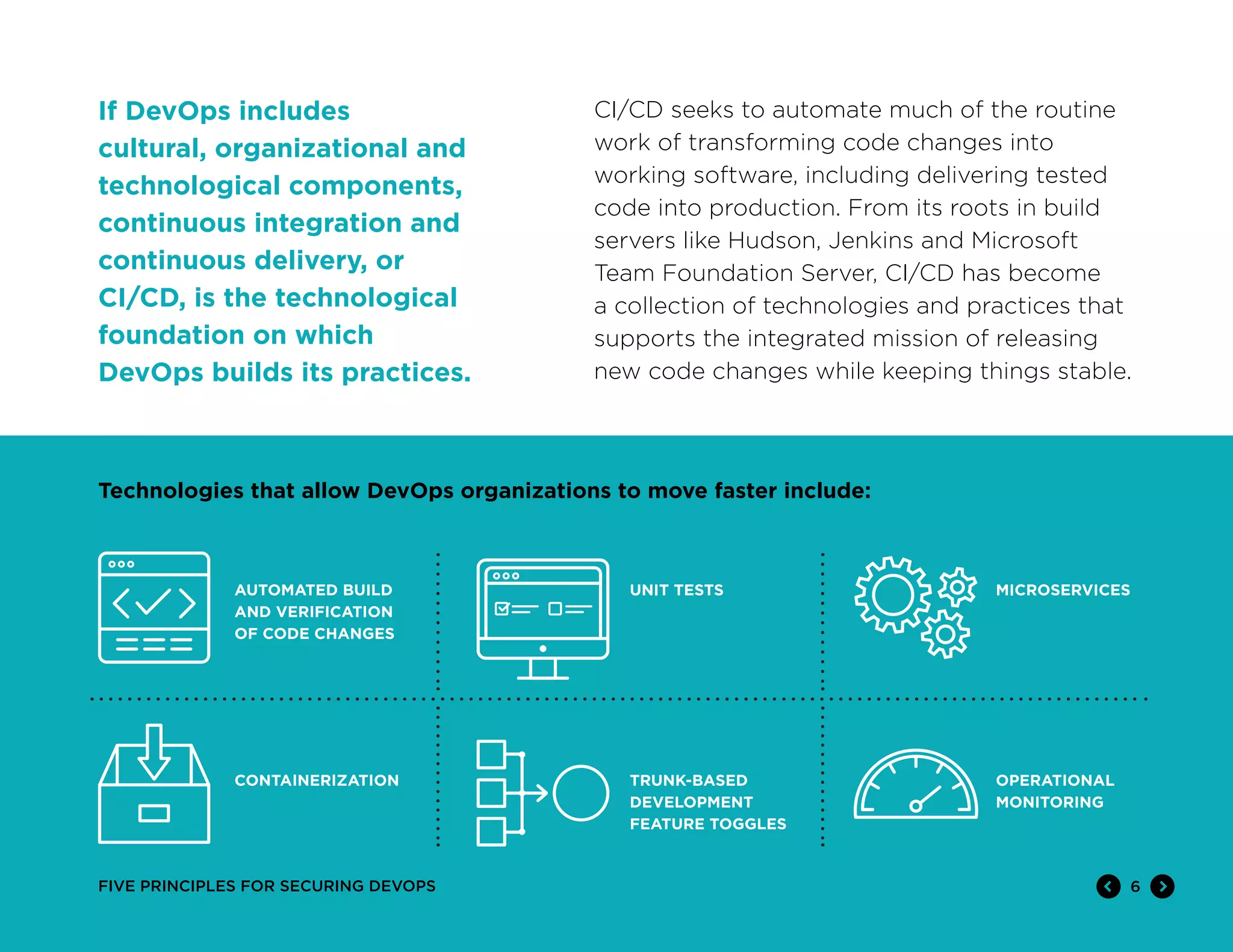
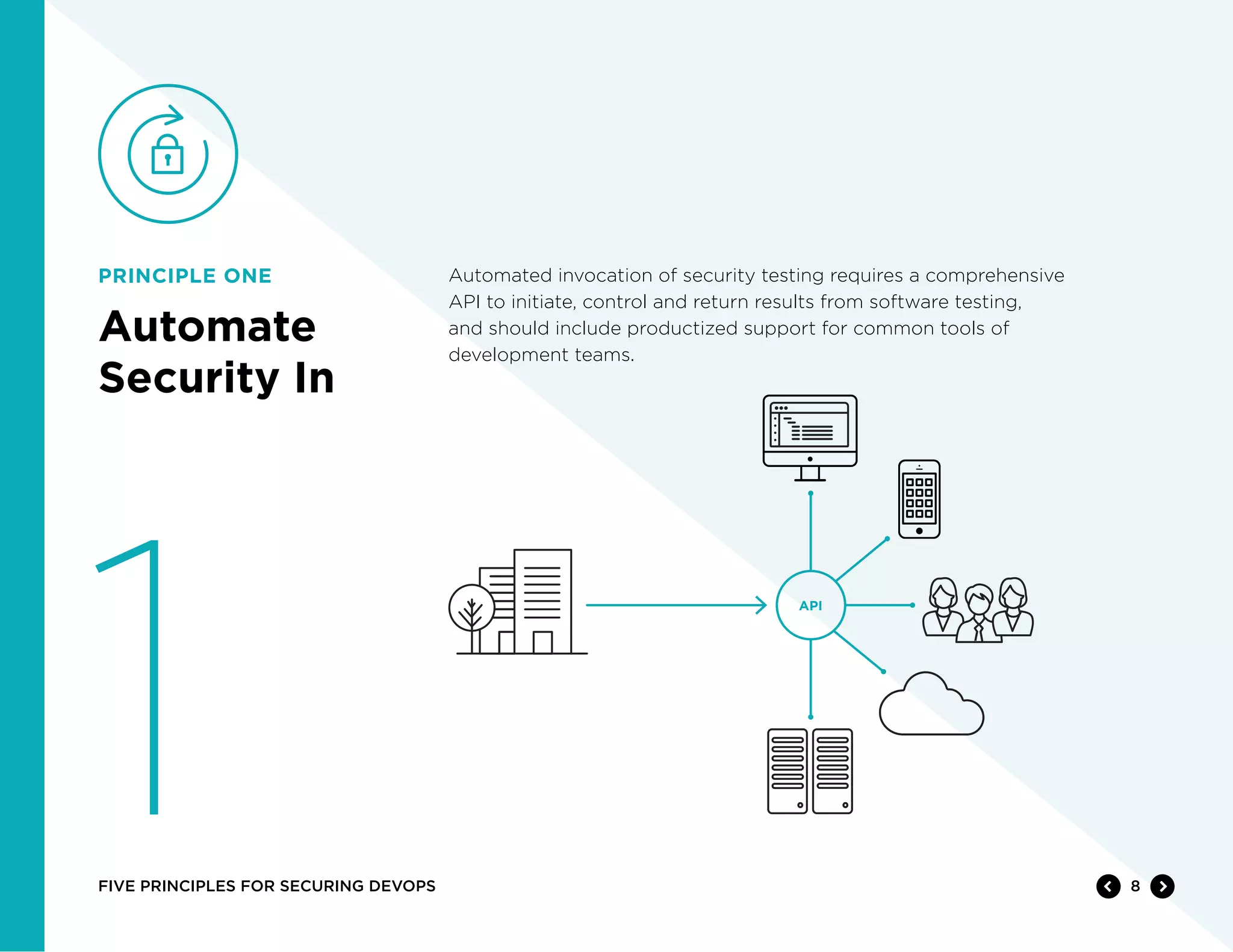
The document discusses five principles for securing DevOps:
1) Automate security testing by integrating it into CI/CD pipelines.
2) Integrate security testing early to "fail quickly" and avoid issues late in the process.
3) Avoid false positives from security tests to prevent blocking critical updates.
4) Build security expertise among developers by training them in secure coding practices.
5) Maintain visibility into application security for deployed software to enable quick responses to attacks.