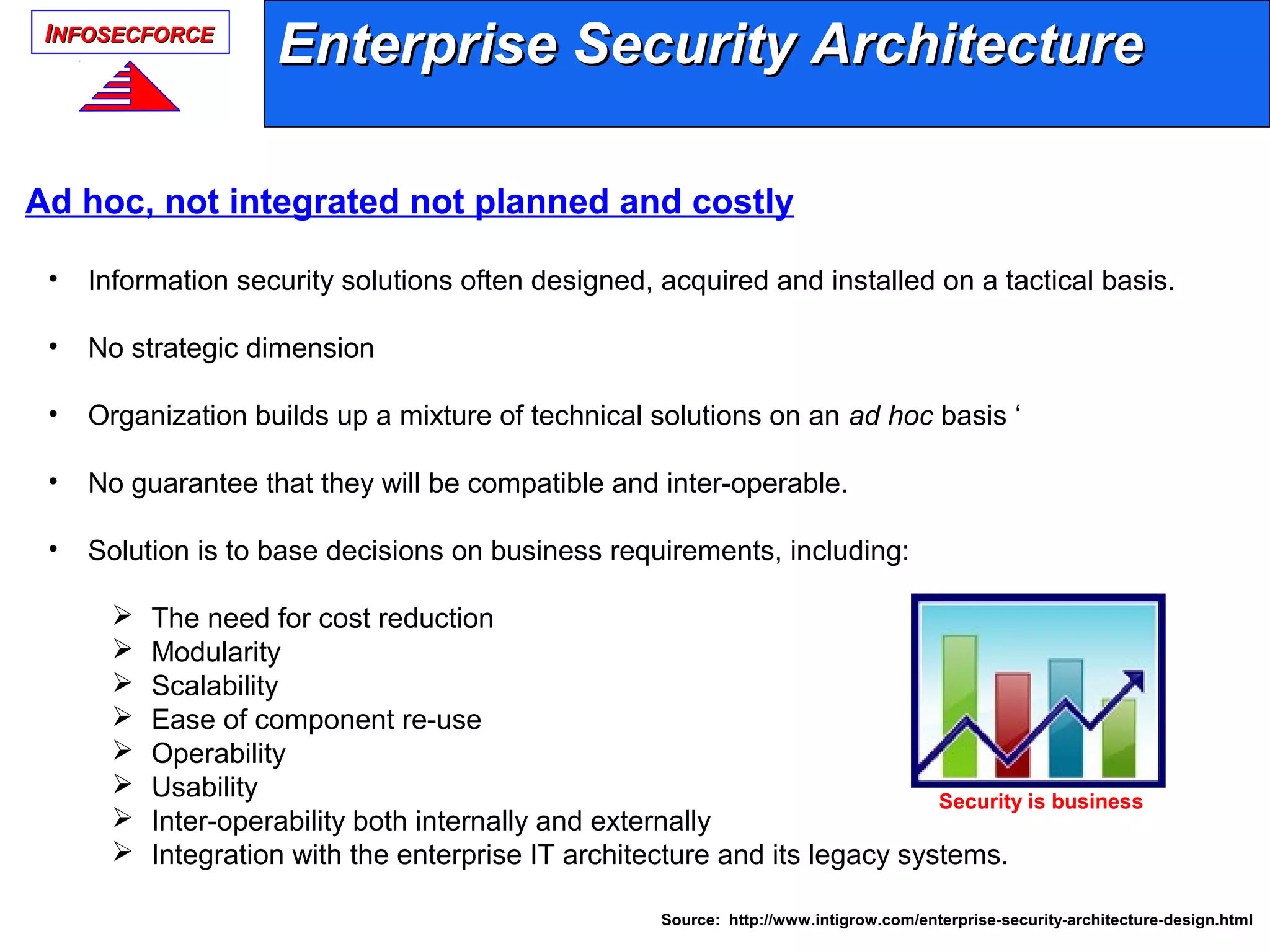
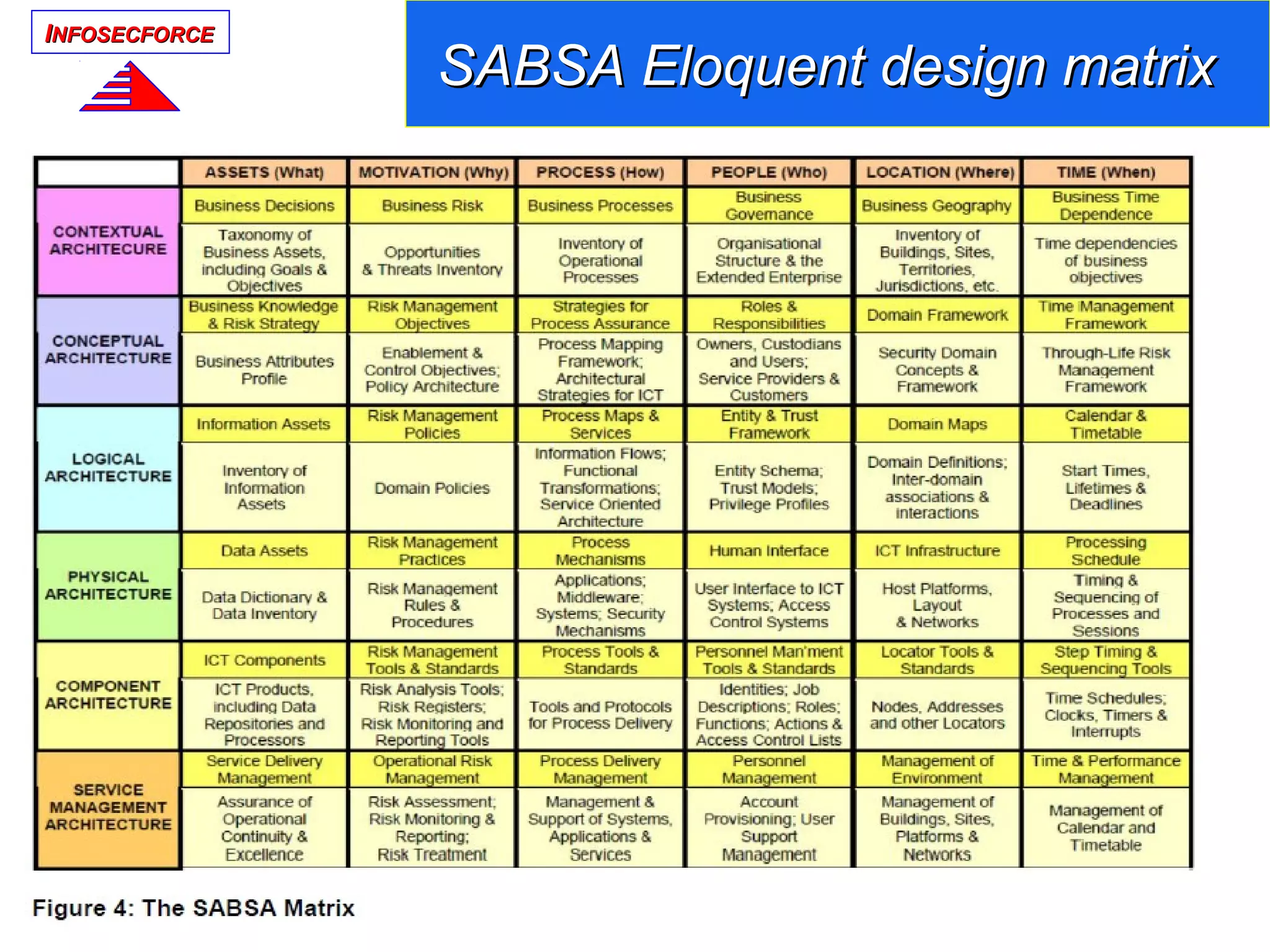
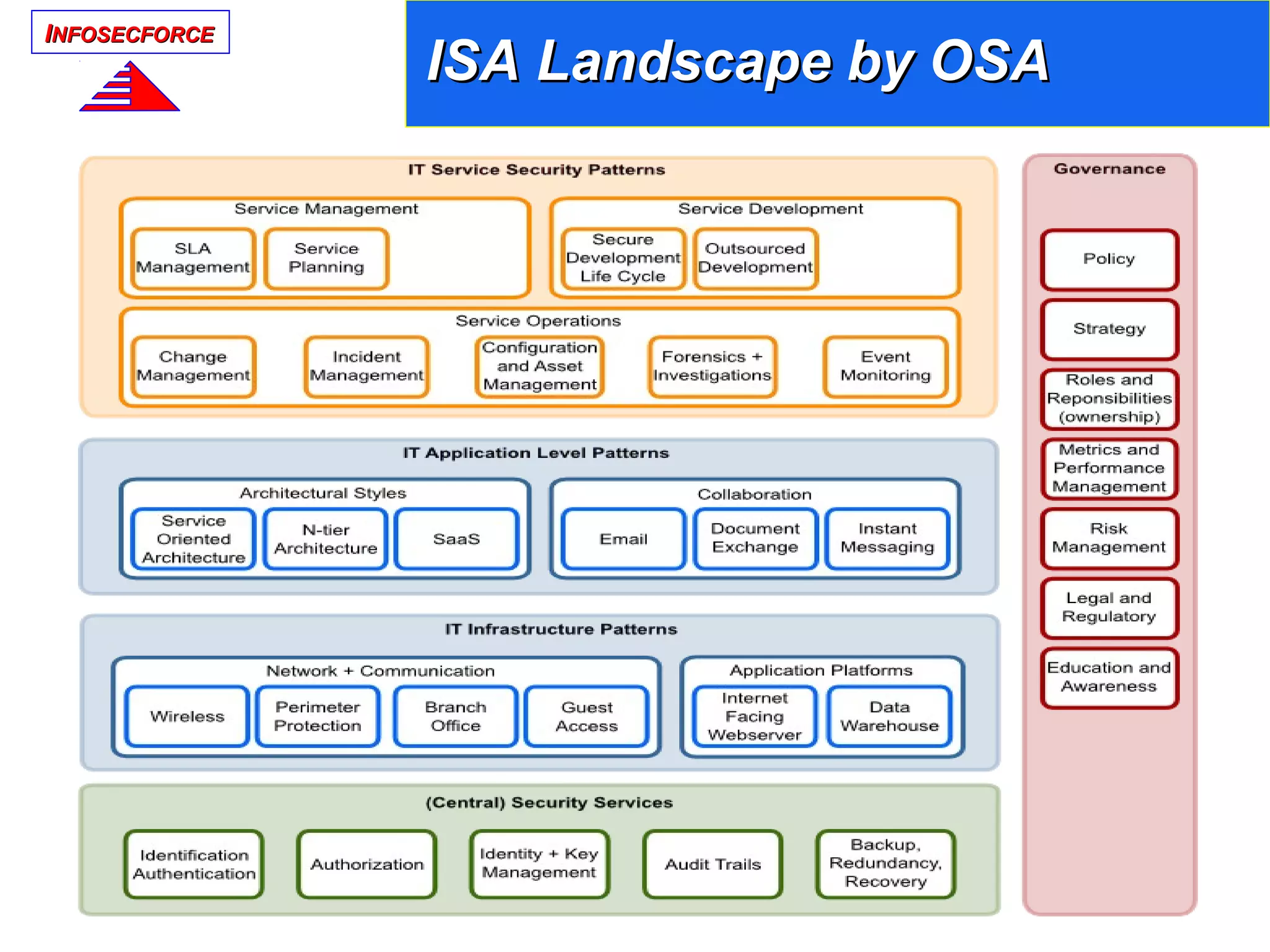
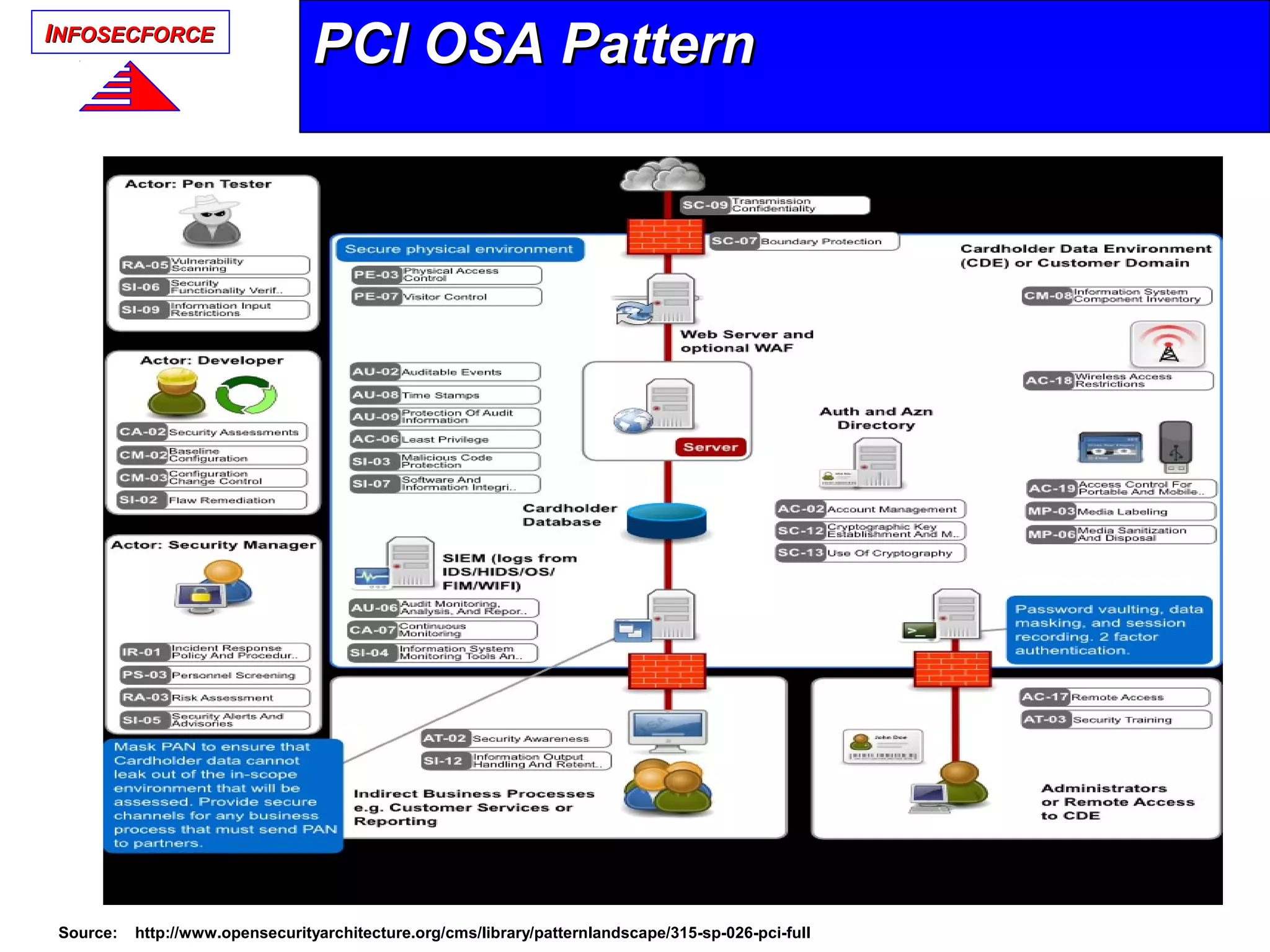
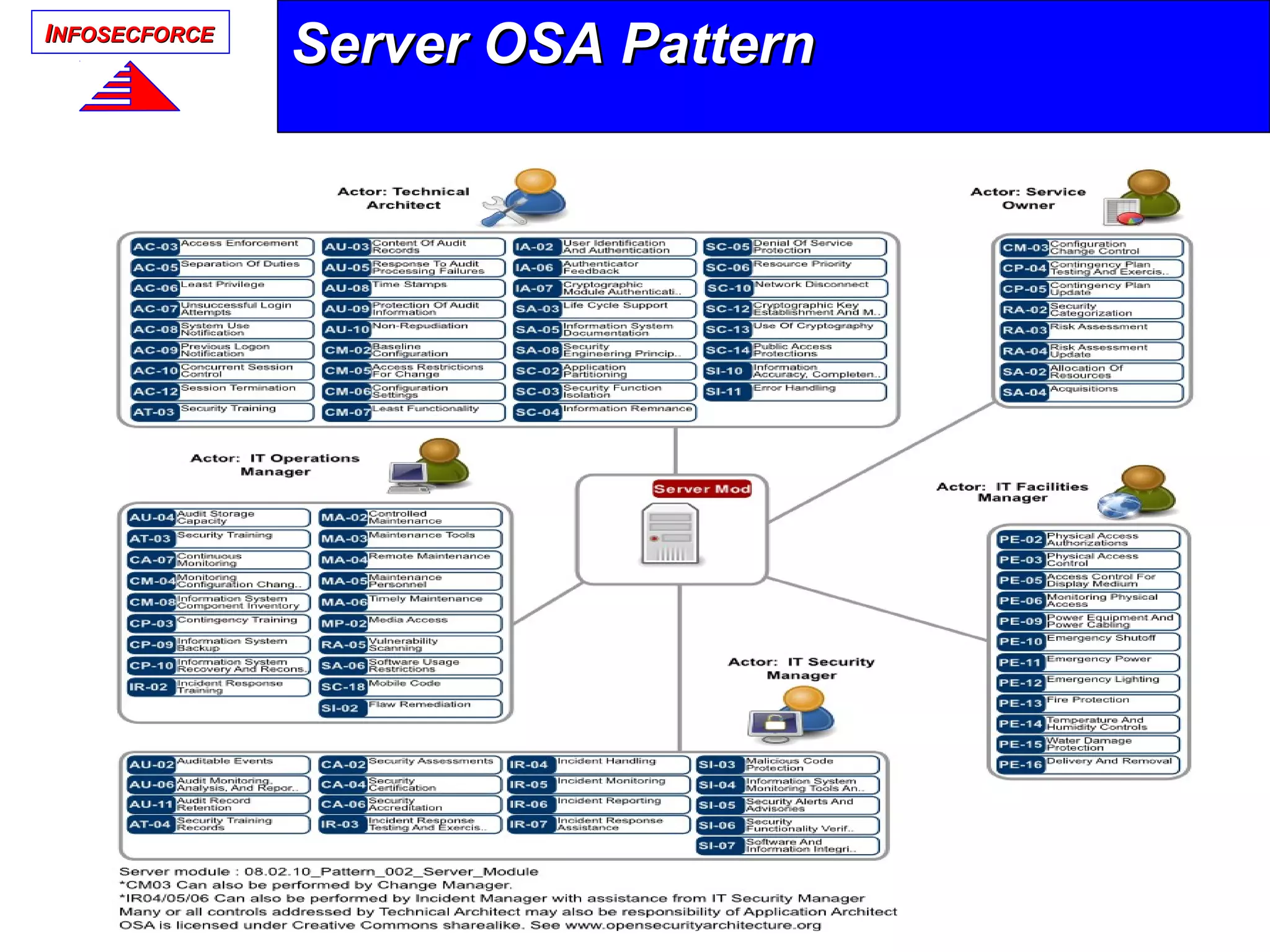
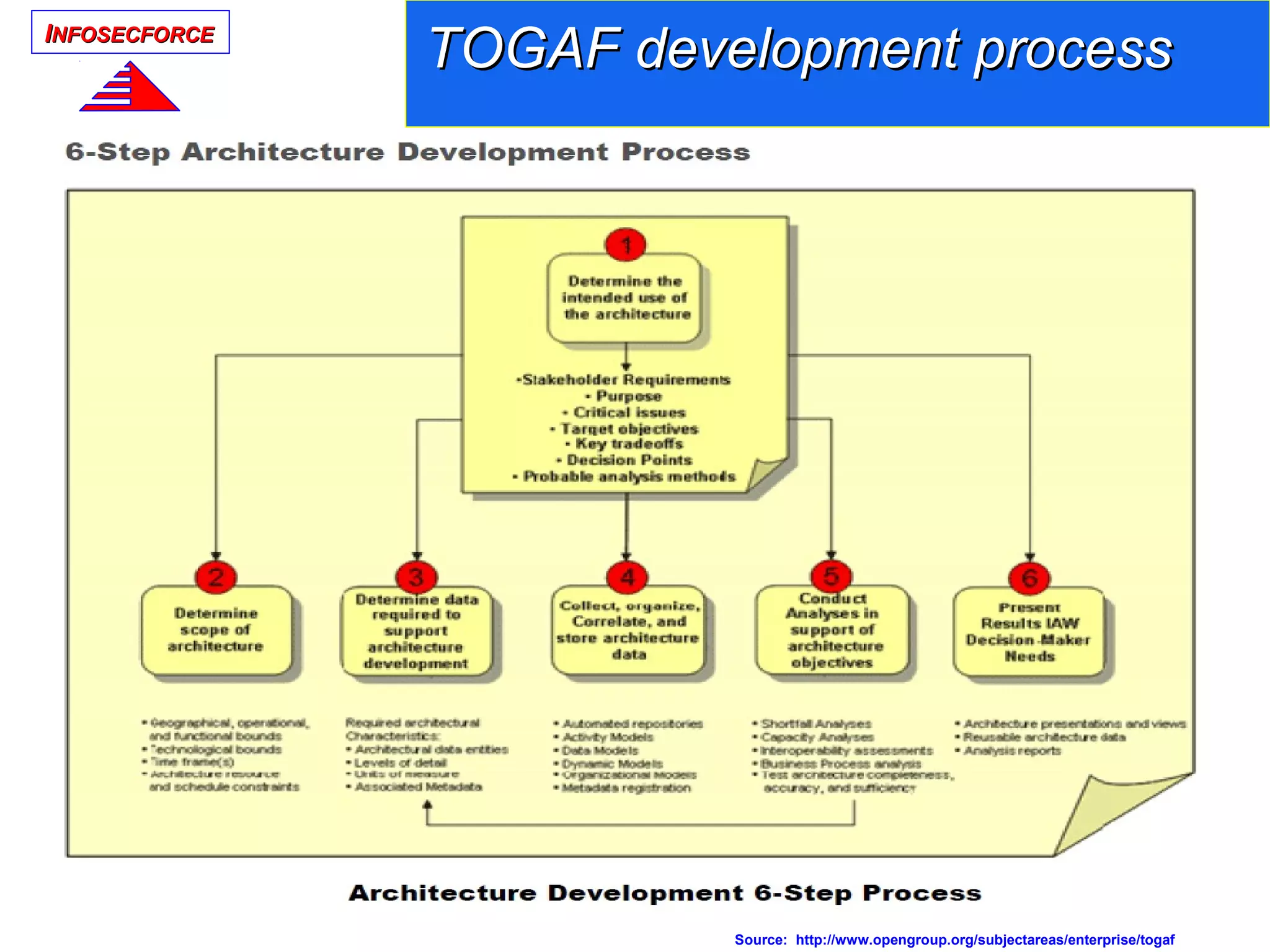
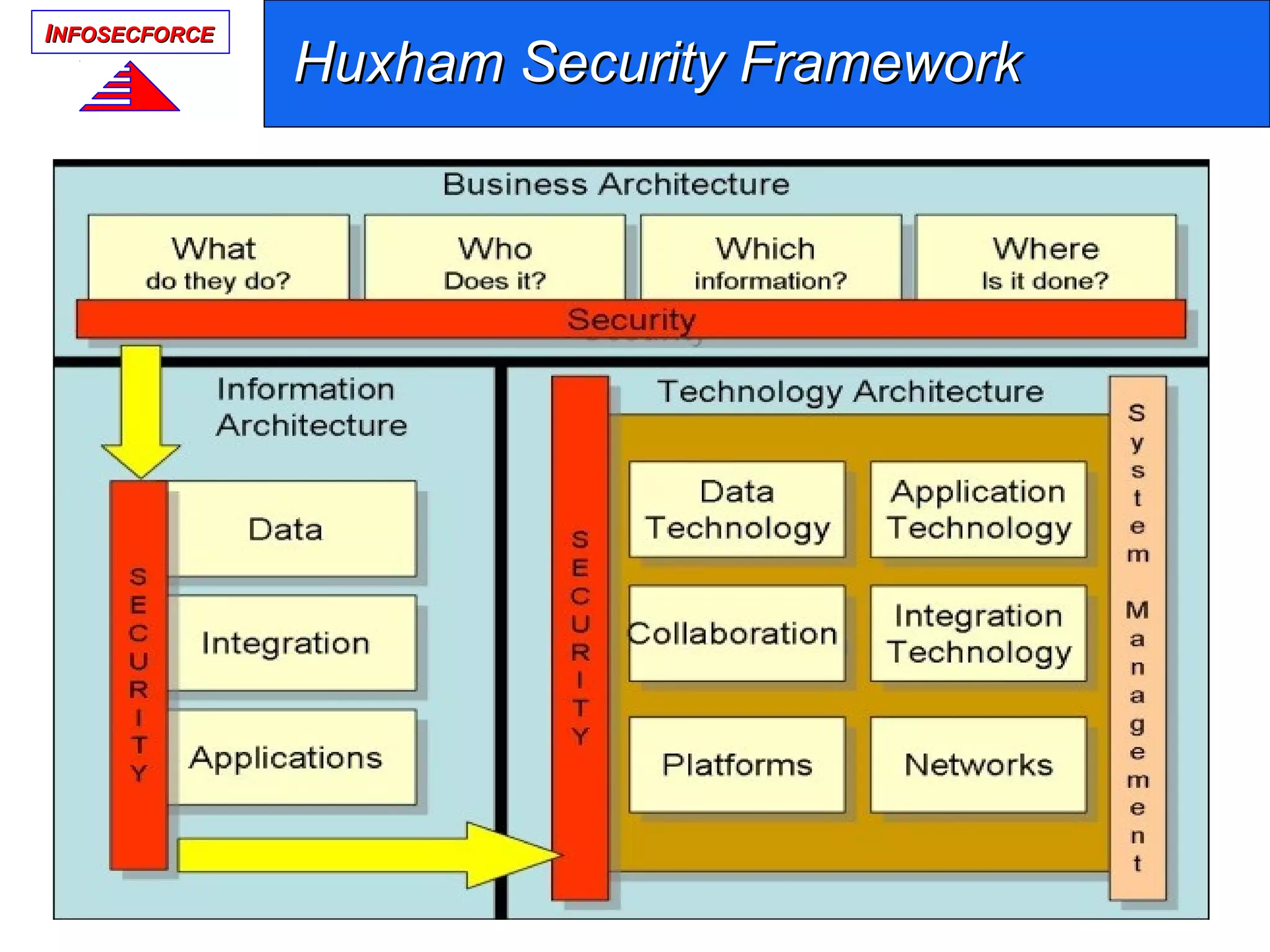
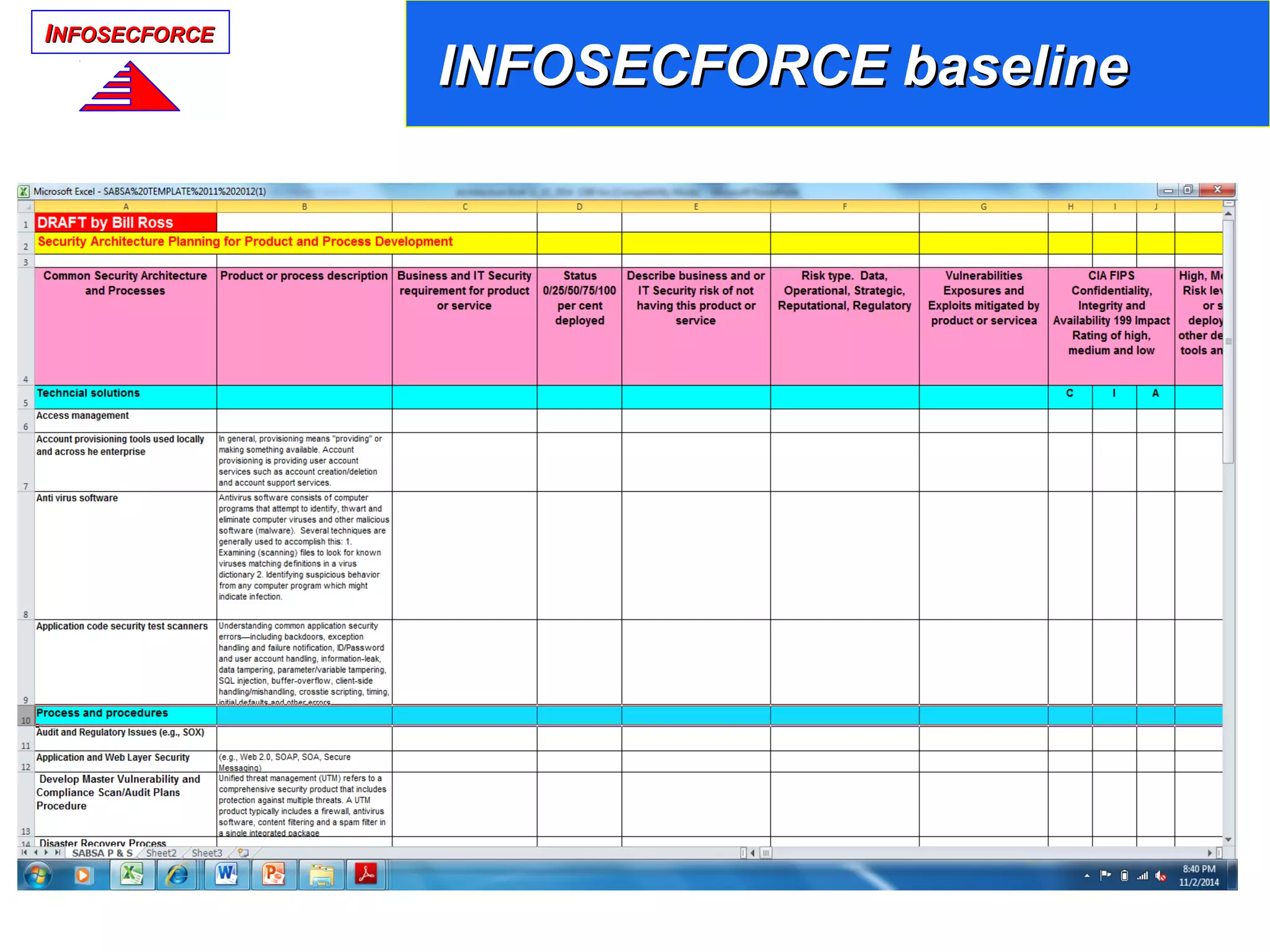
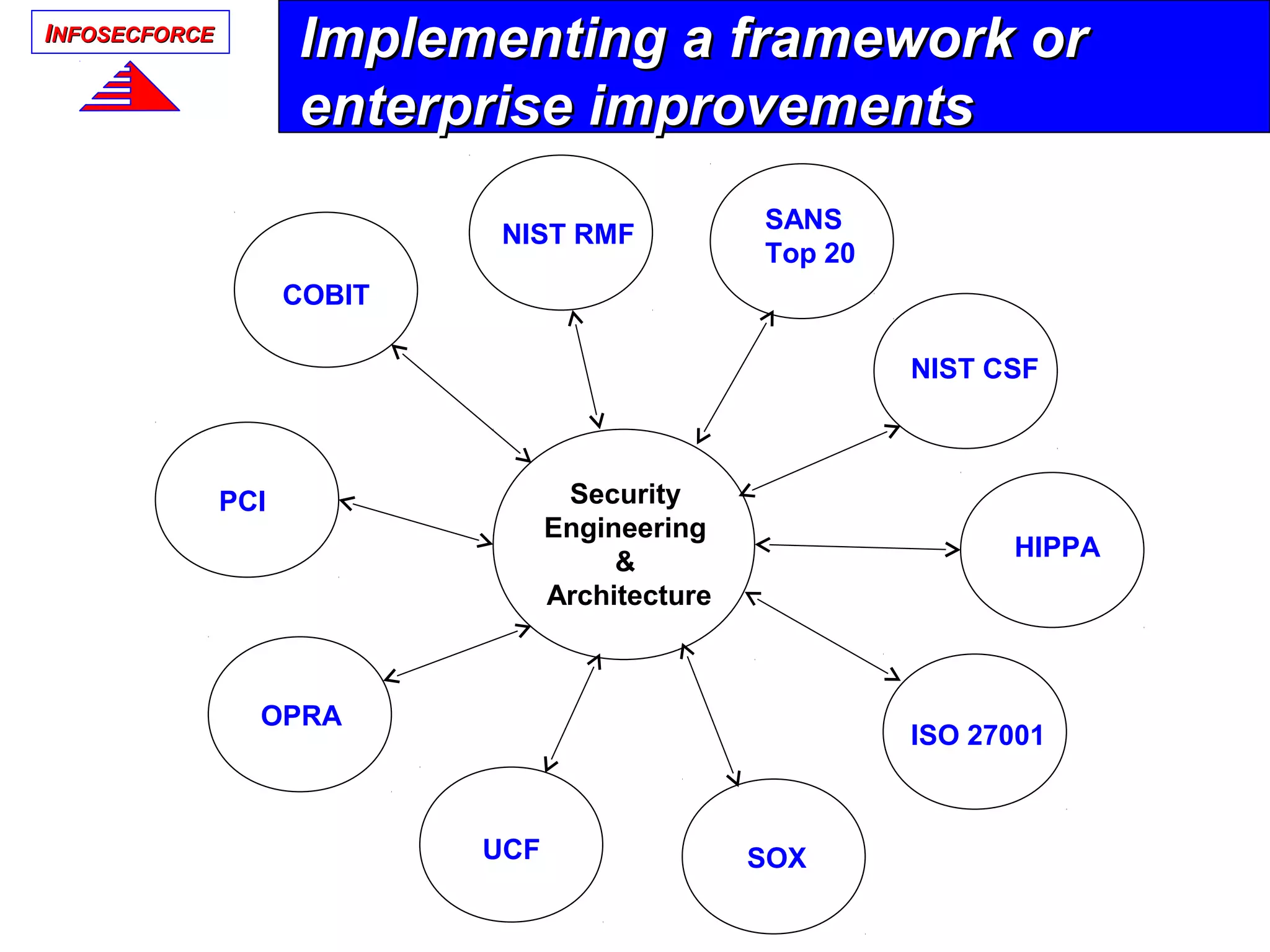
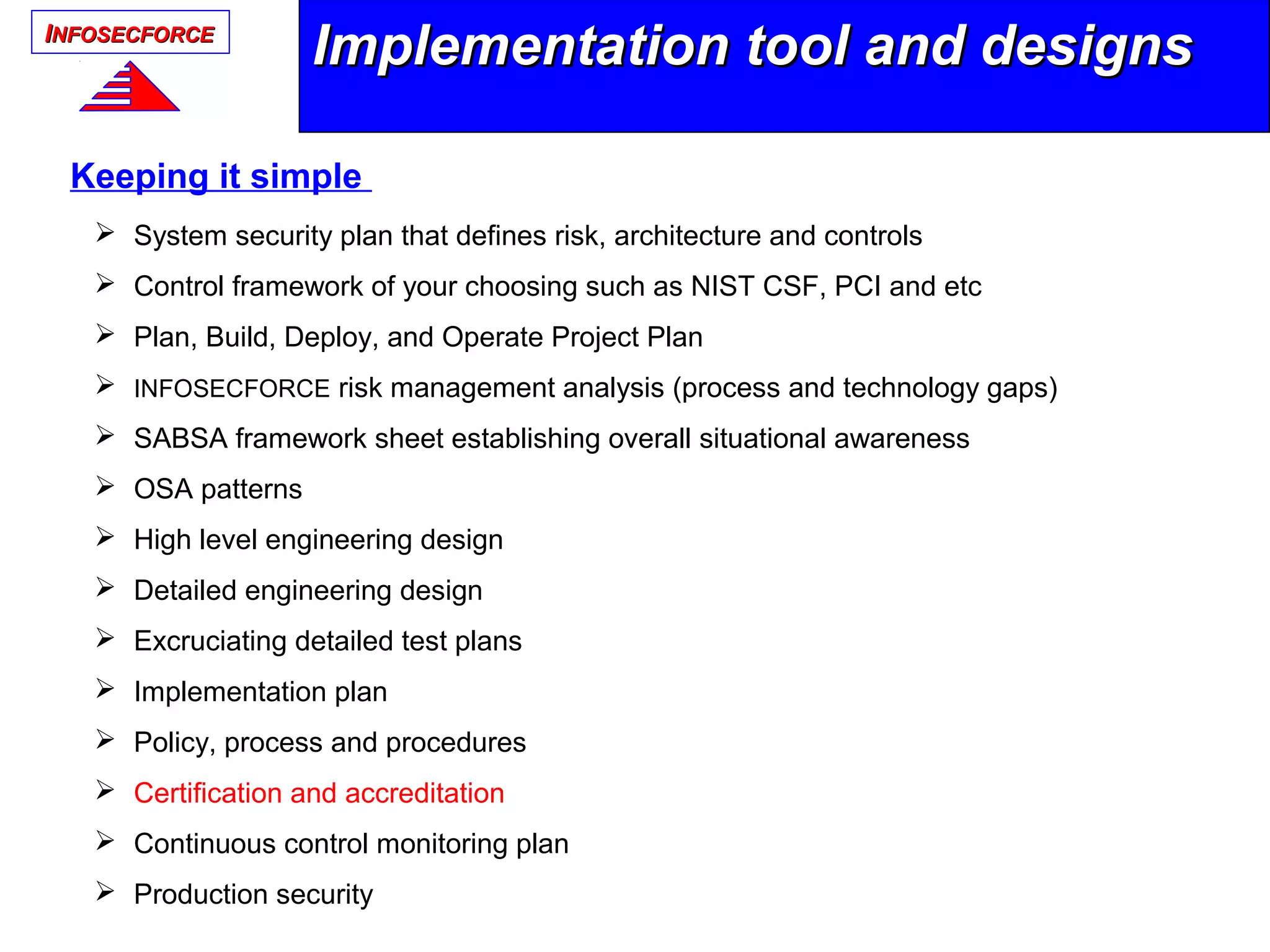
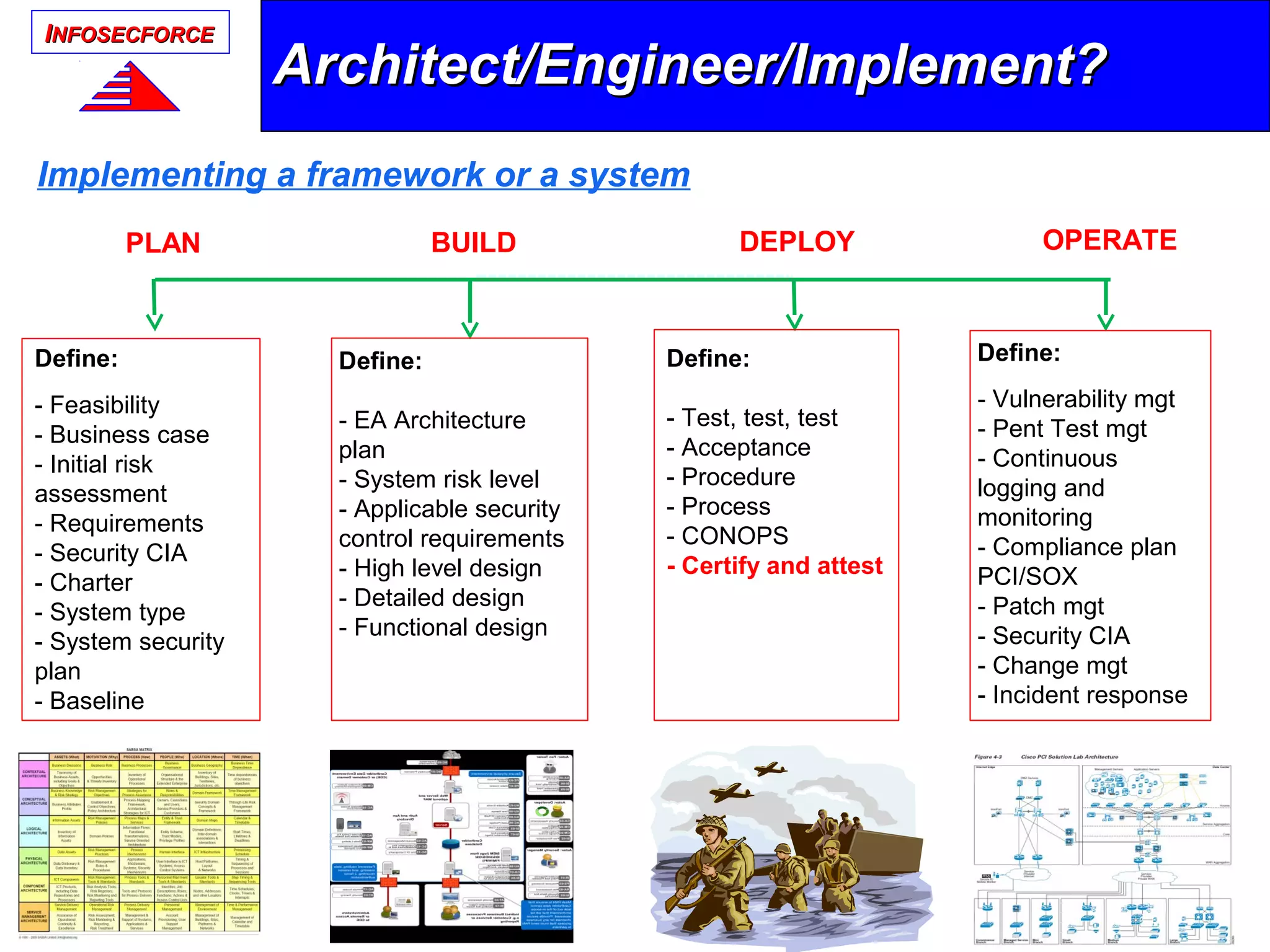
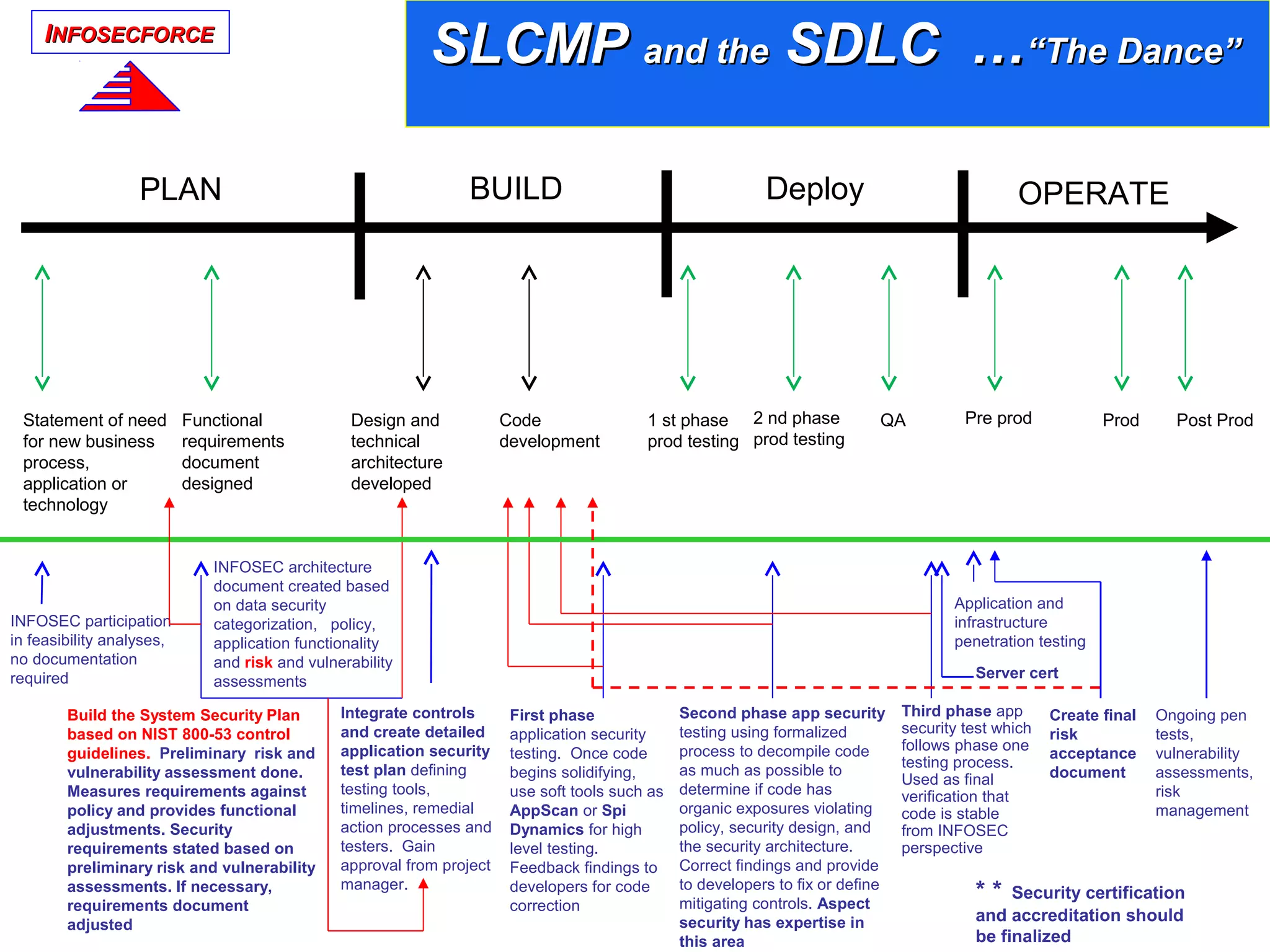
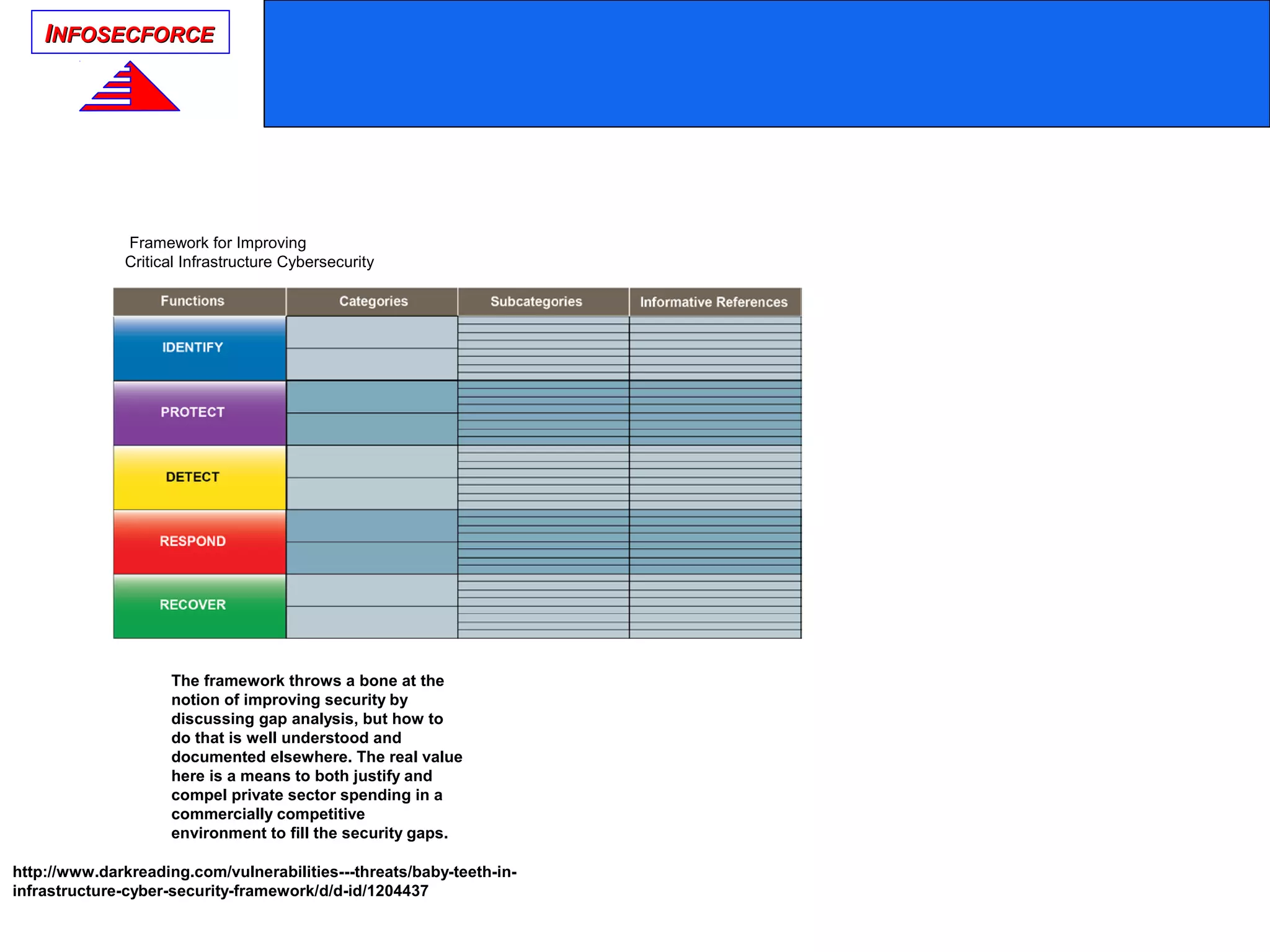
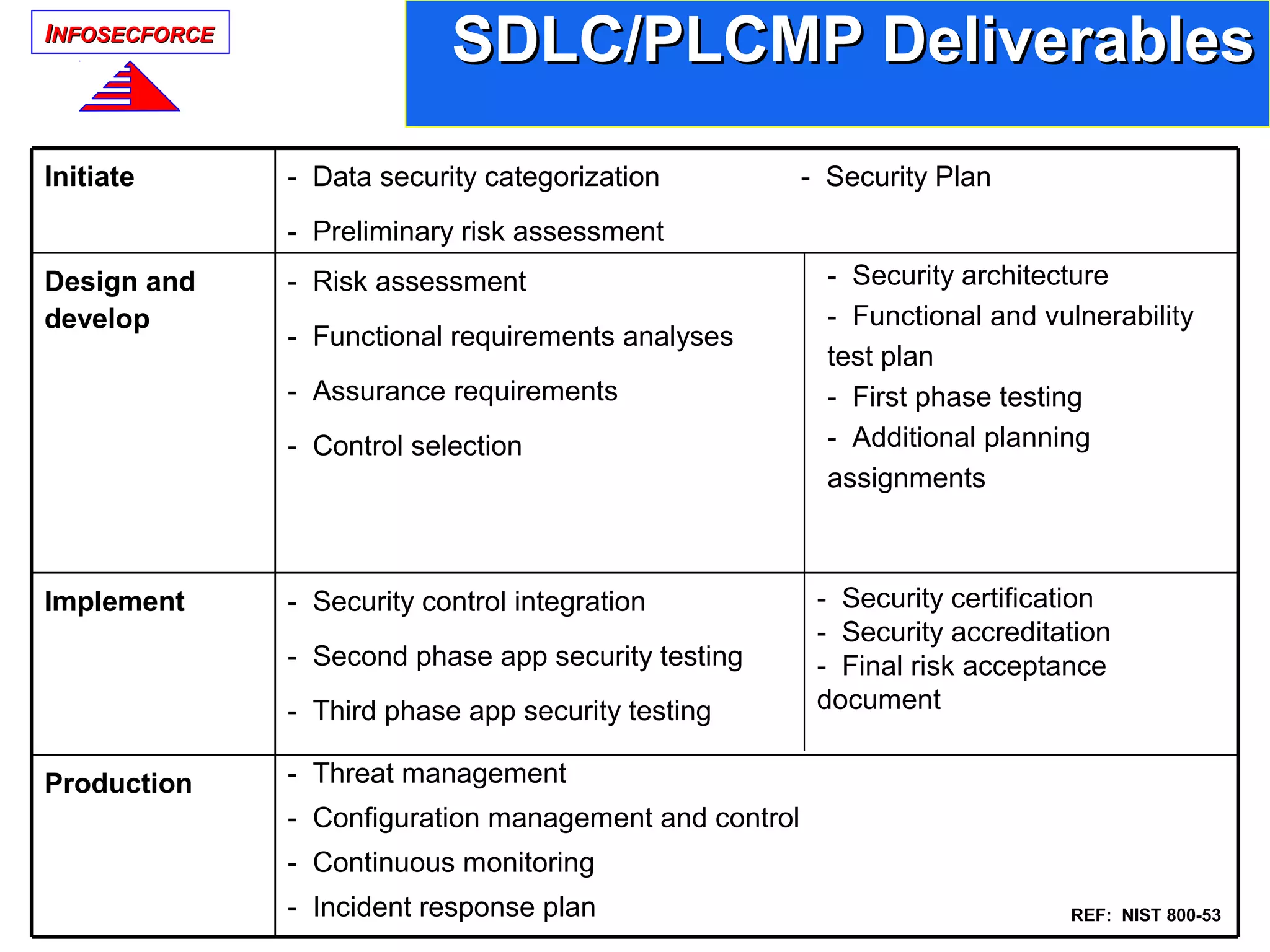
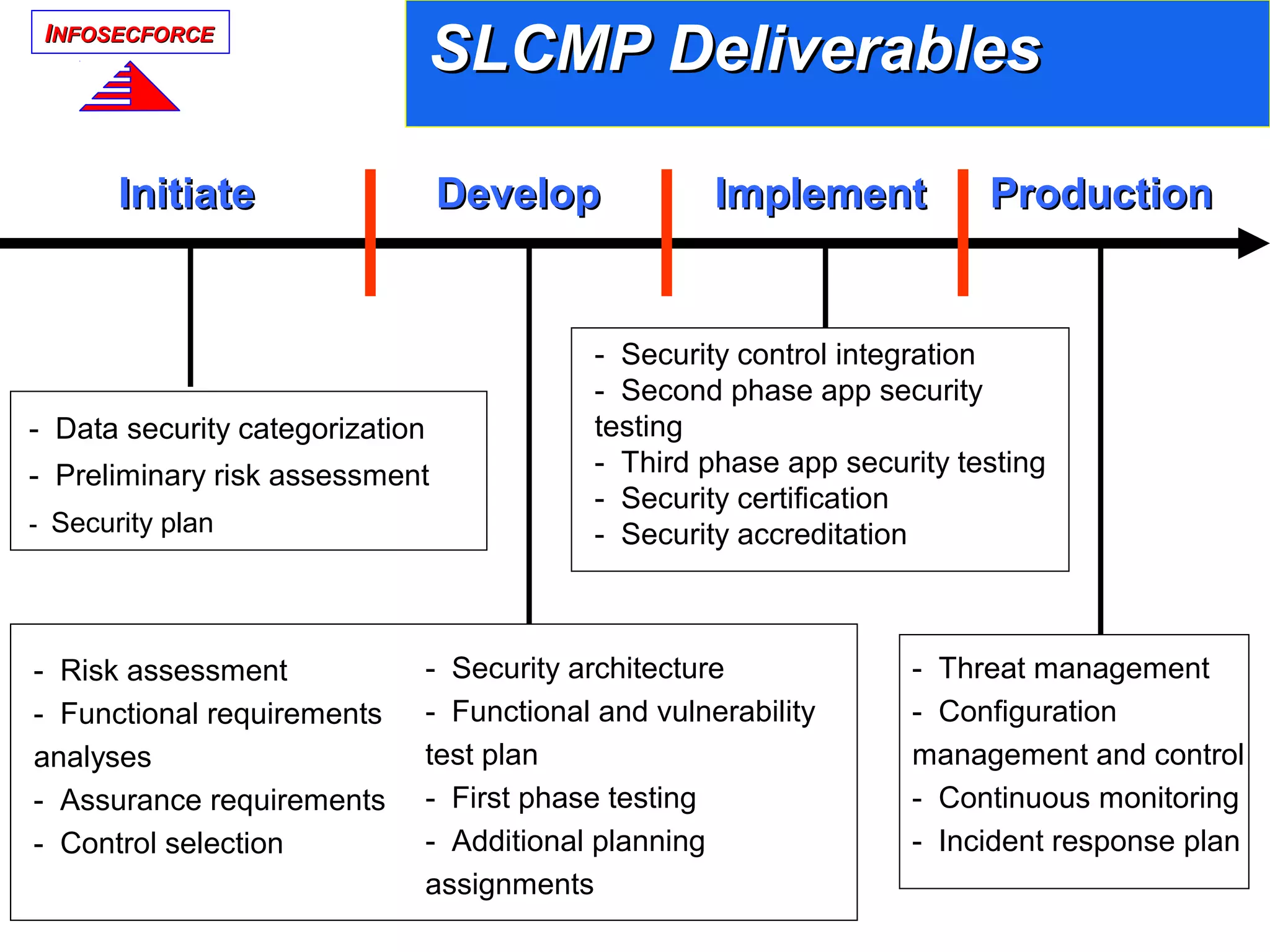
The document discusses the vital role of Information Security Architects (ISA) in combatting cyber threats and establishing cohesive security frameworks within organizations. It emphasizes the need for a clear definition of the ISA role, as current interpretations are varied and often lead to misunderstandings. The text calls for a unified approach to security architecture that aligns with business objectives and standards to enhance the effectiveness of information security practices.










![IINFOSECFORCENFOSECFORCE
SAN thinkSAN think
“ Can you build a Defense in Depth architecture without an architect ? “
“ Of course, you are not going to get very far with an architectural approach to Defense in Depth
without an architect. Unfortunately, the industry is still unclear as to exactly what an
IT Security Architect is.
The concept is, however, starting to mature.
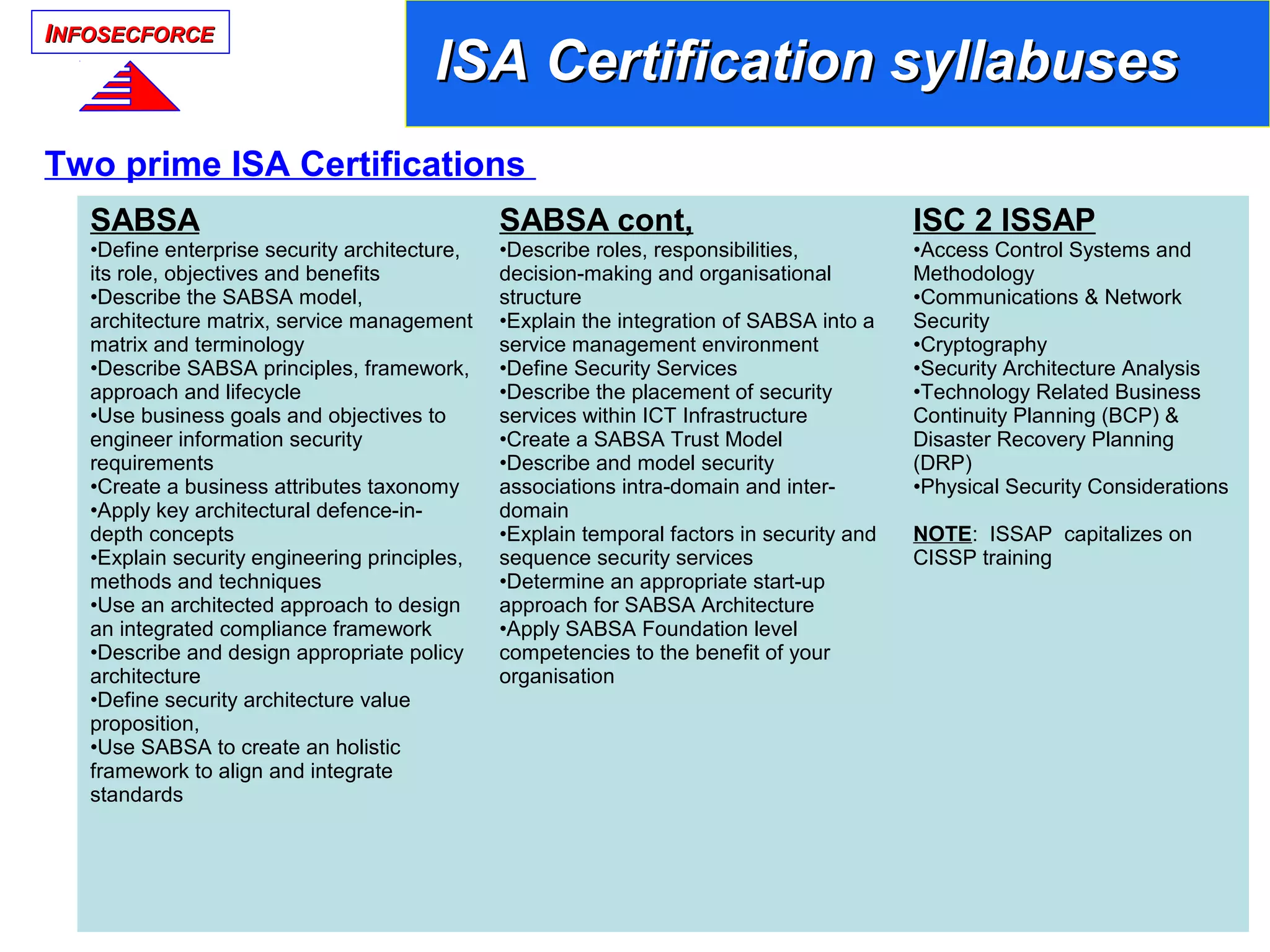
(ISC)2 organization has created an ISSAP (Information Systems Security Architecture
Professional) certification[2].
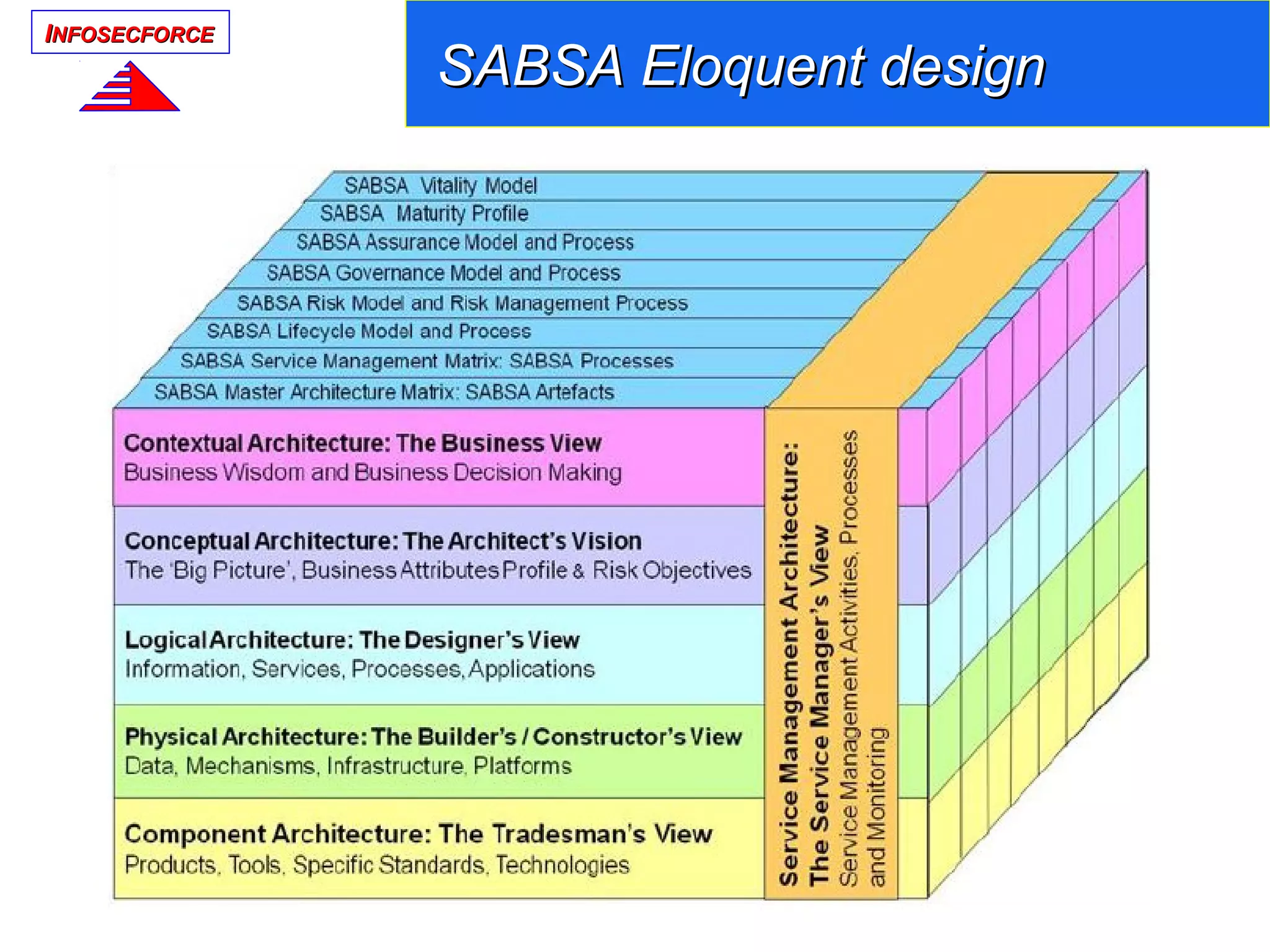
SABSA organization has three levels of certifications for Security Architects: Foundation,
Practitioner, and Master.
There are job opportunities for positions labeled as "Security Architects," although many times
they sound more like engineers than architects.
Though specific knowledge about systems and networks is important, an architect should have
the ability to assemble and disassemble pieces of knowledge to/from a whole.
“
Stephen Northcutt, J. Michael Butler and the GIAC Advisory Board](https://image.slidesharecdn.com/securityarchitectureanalysesbrief21april2015-150422155159-conversion-gate01/75/Security-architecture-analyses-brief-21-april-2015-15-2048.jpg)