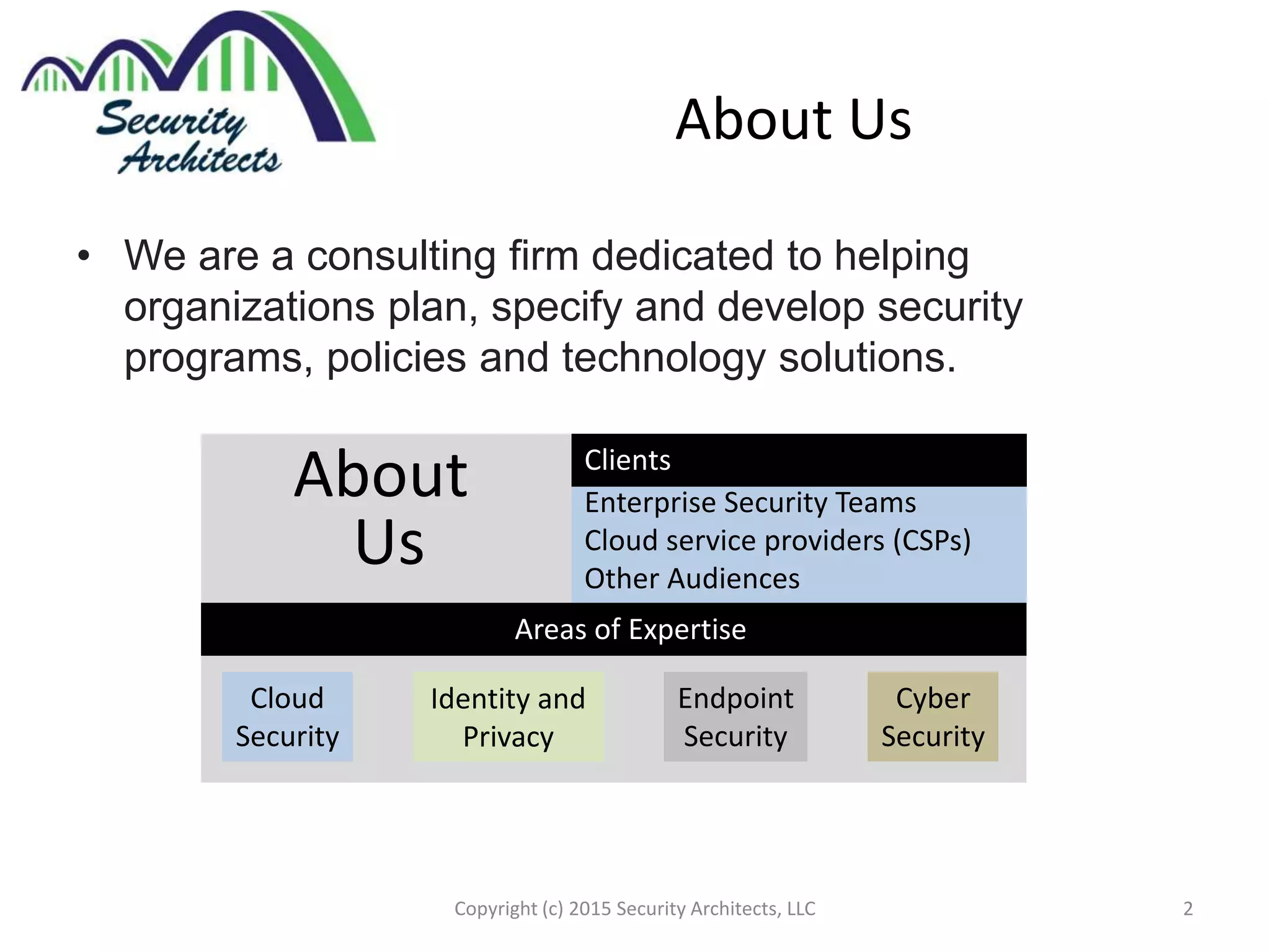
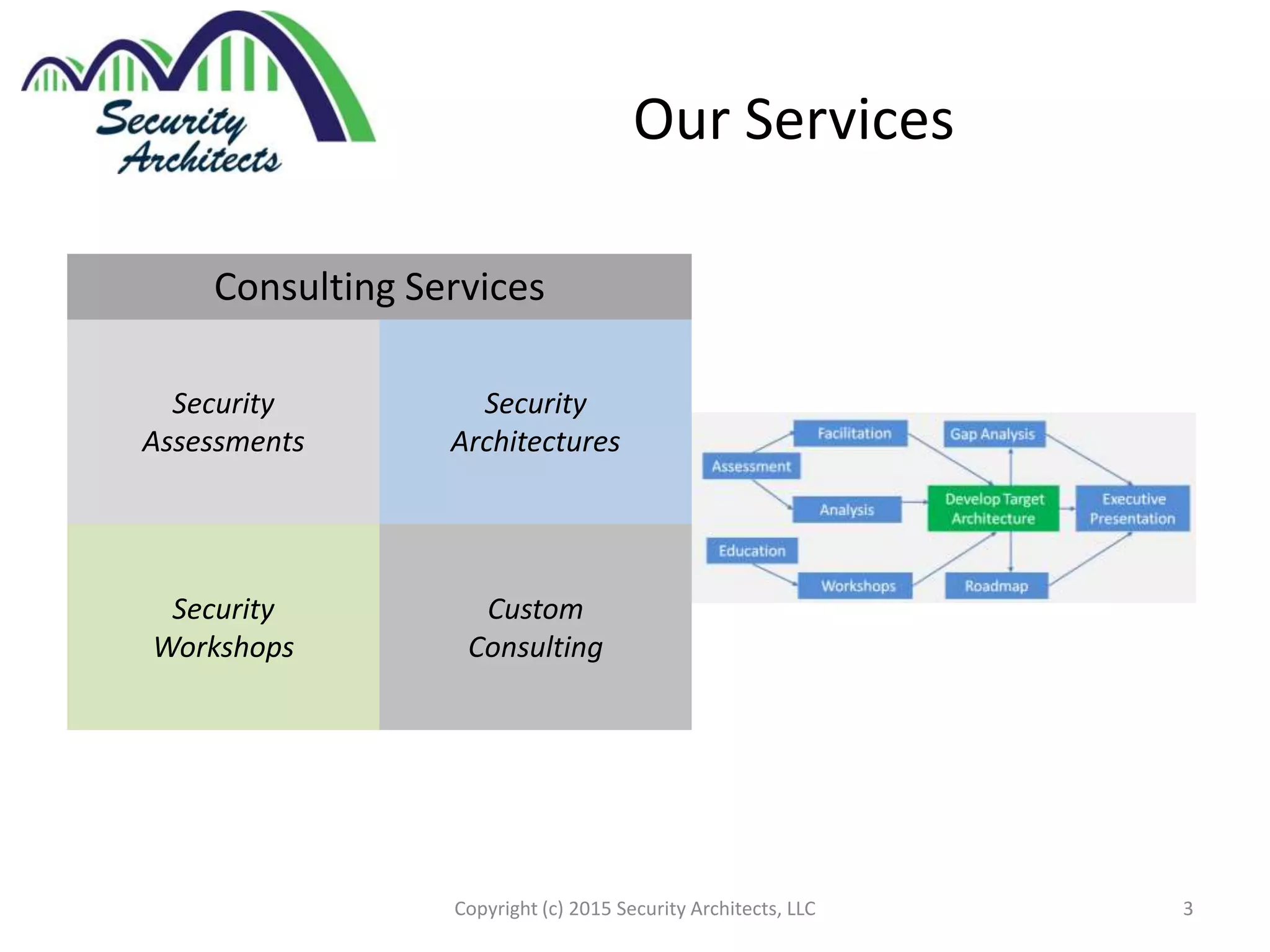
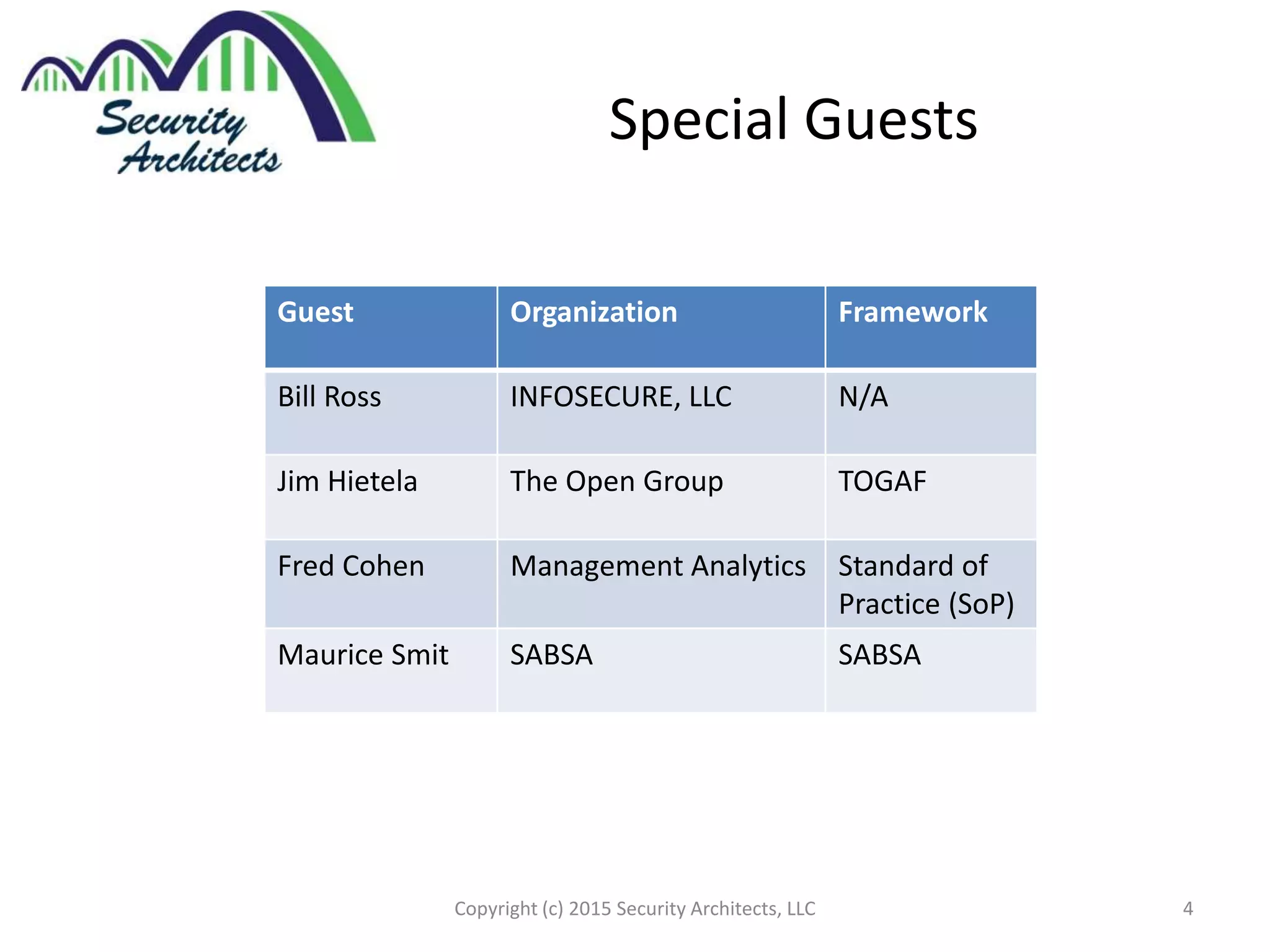
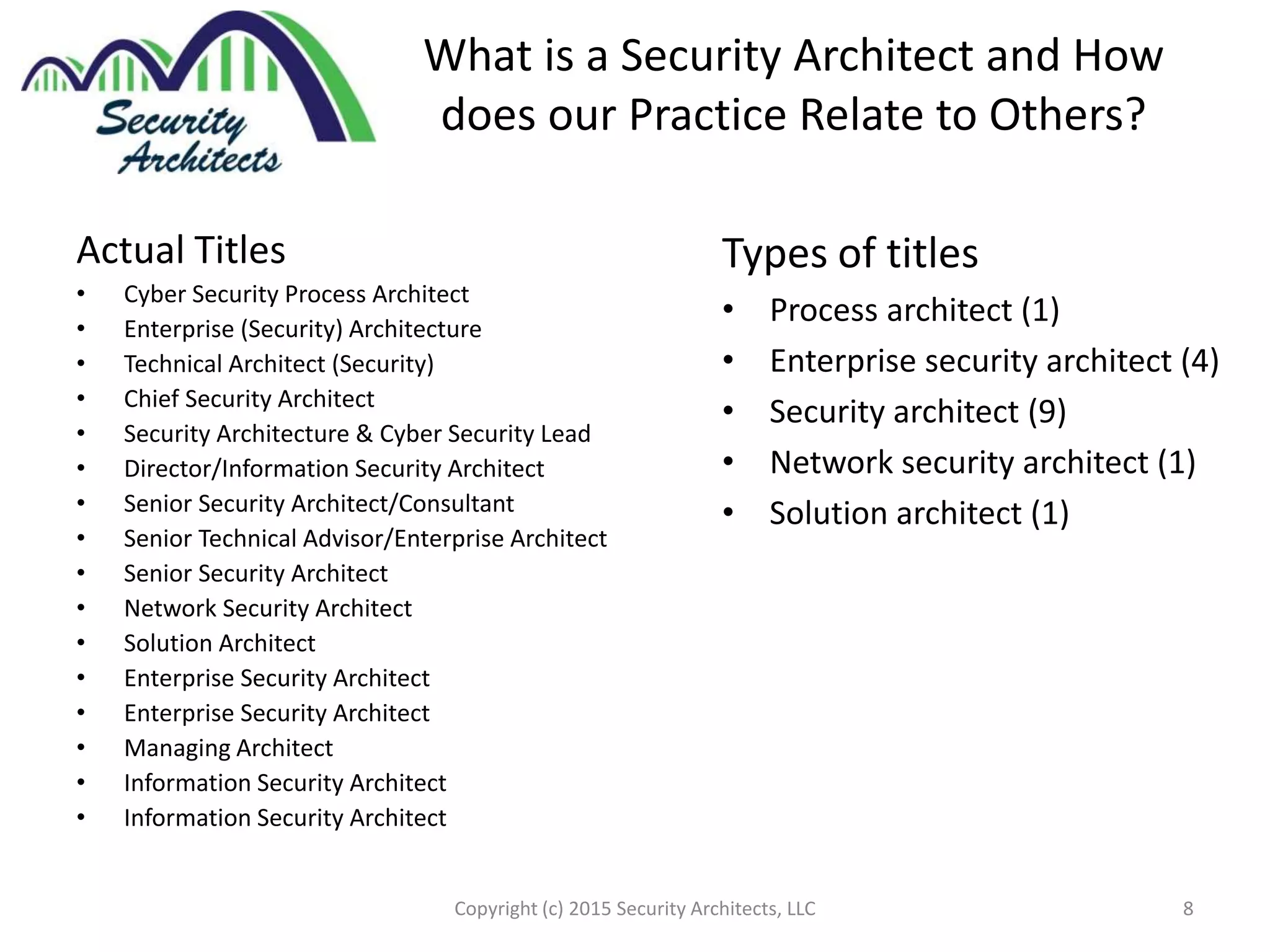
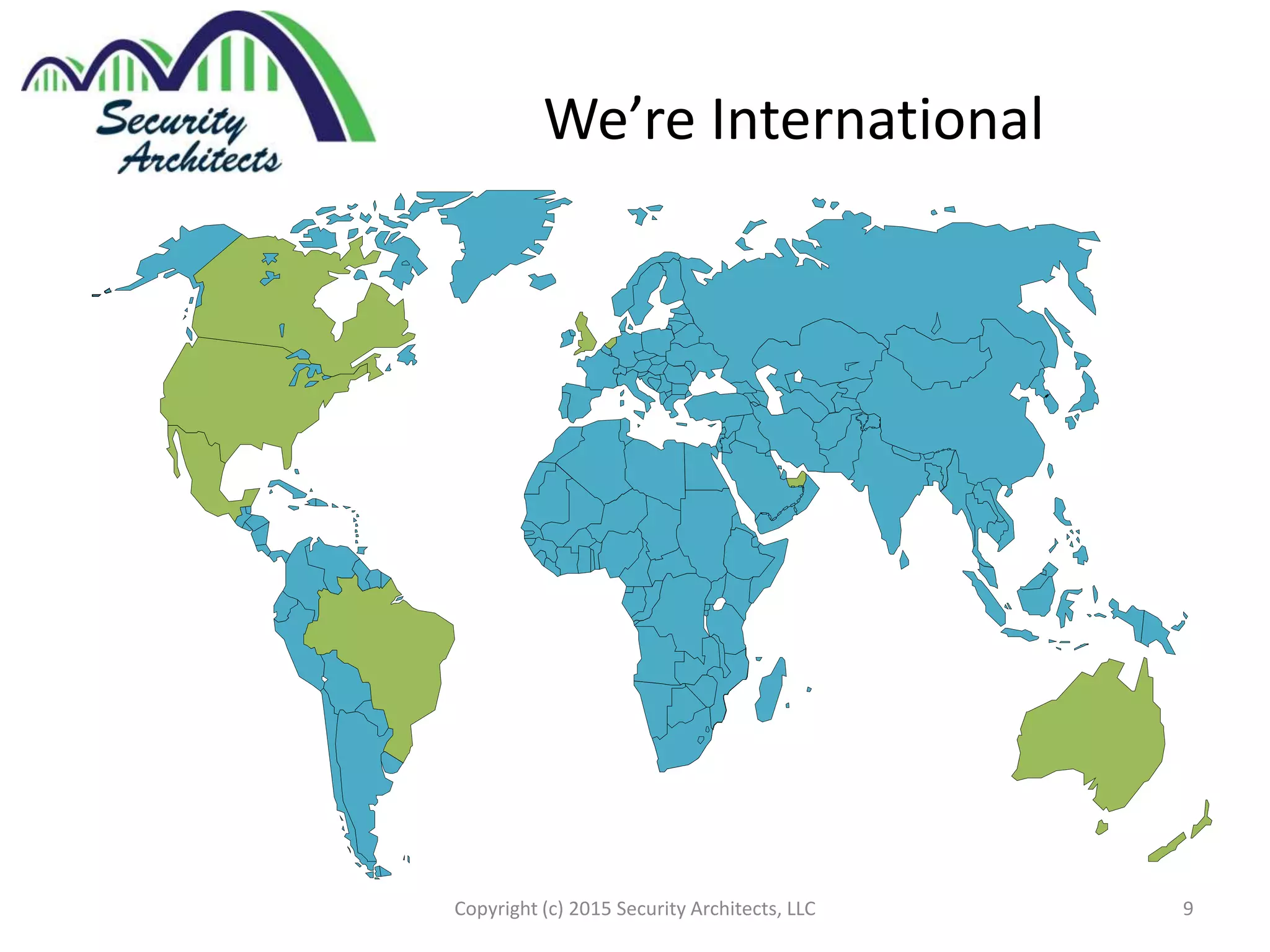
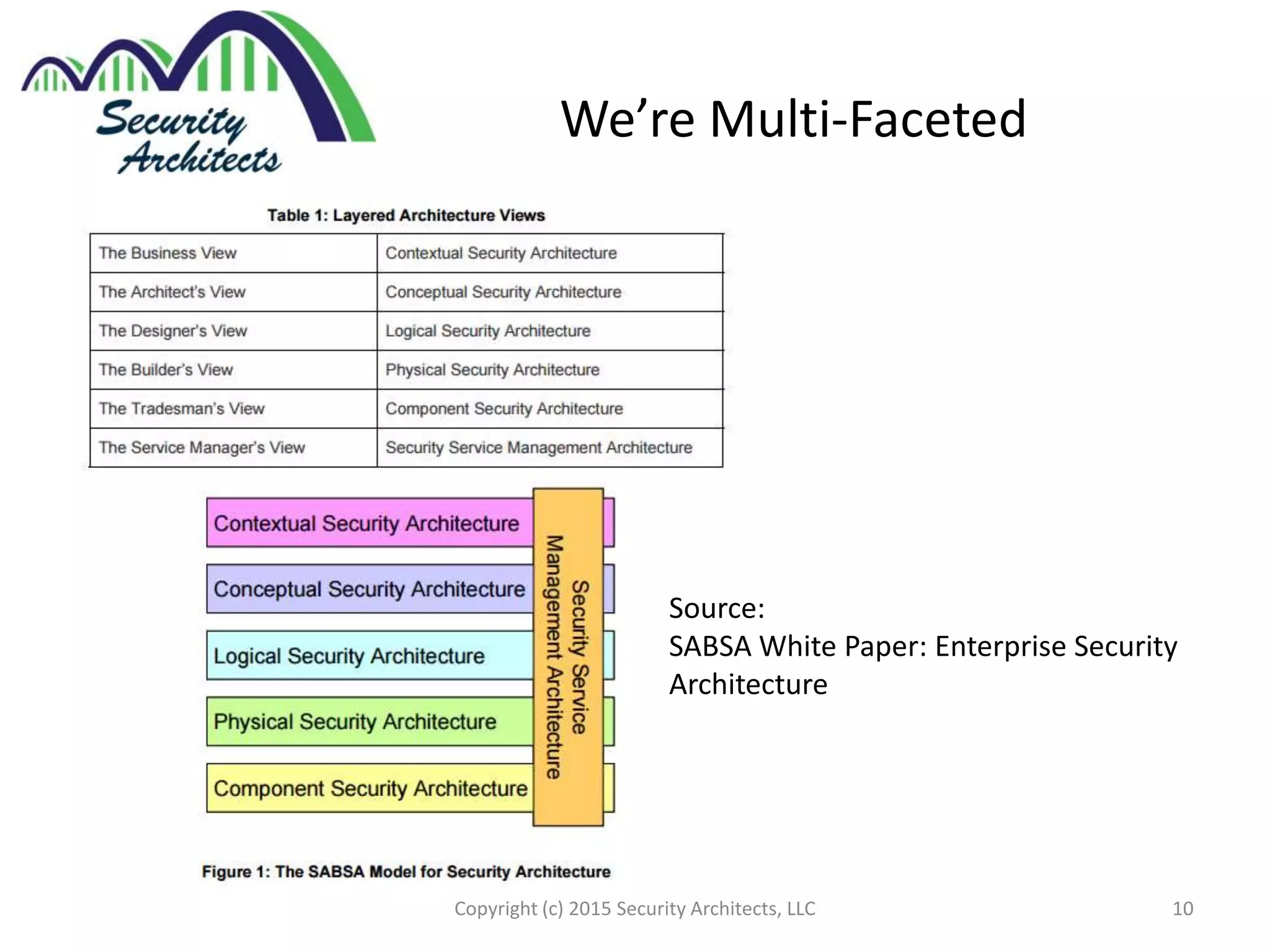
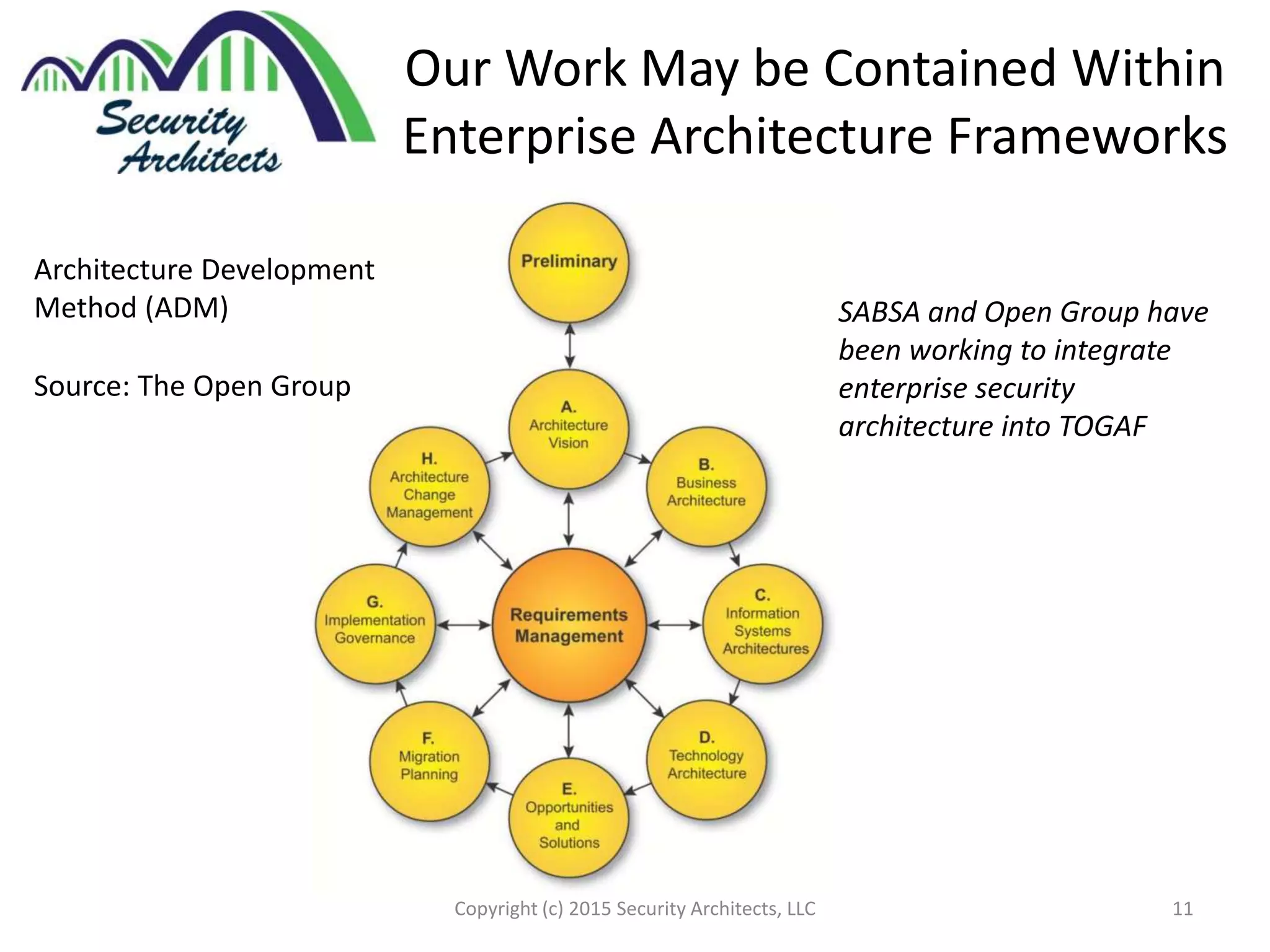
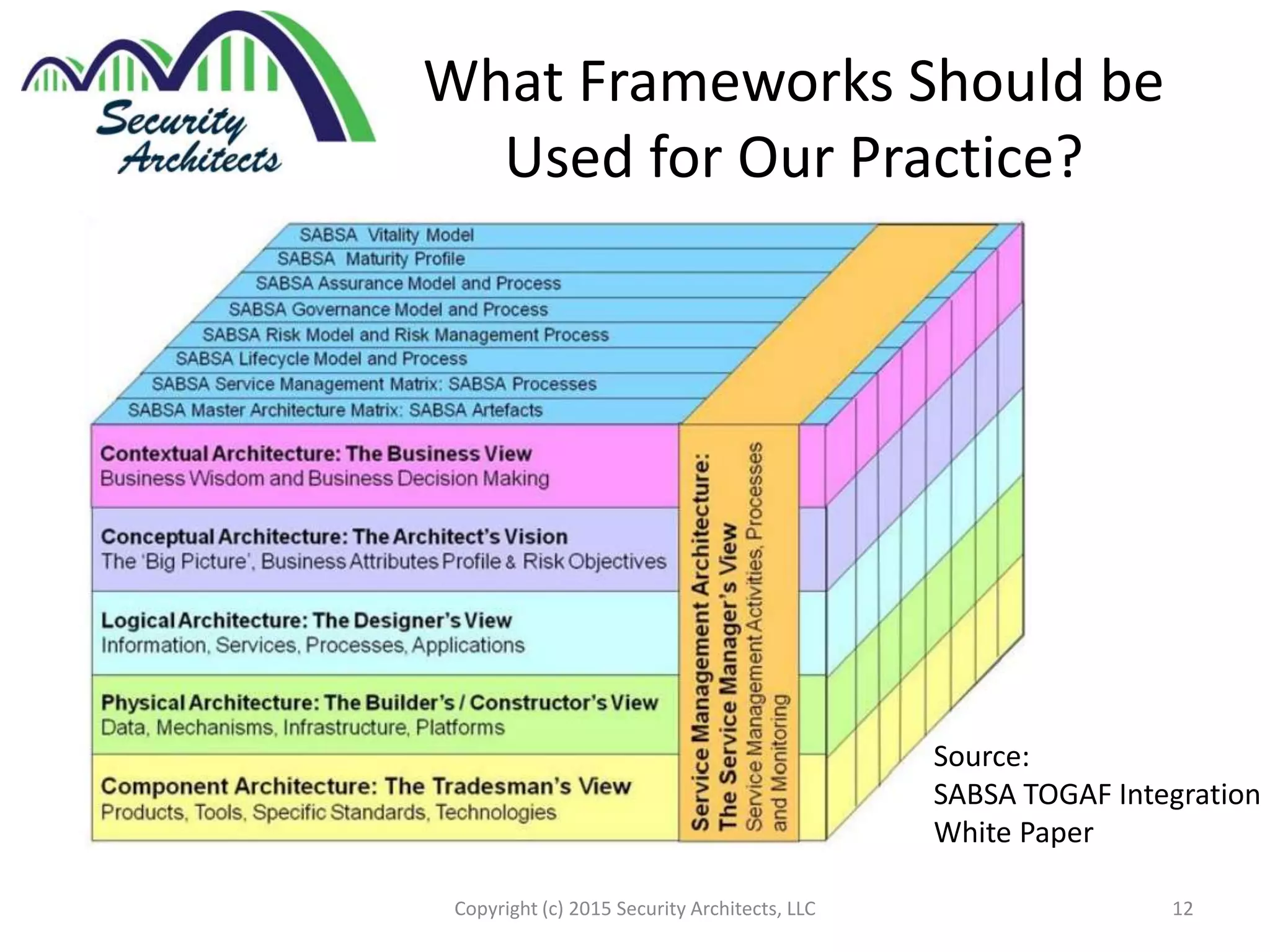
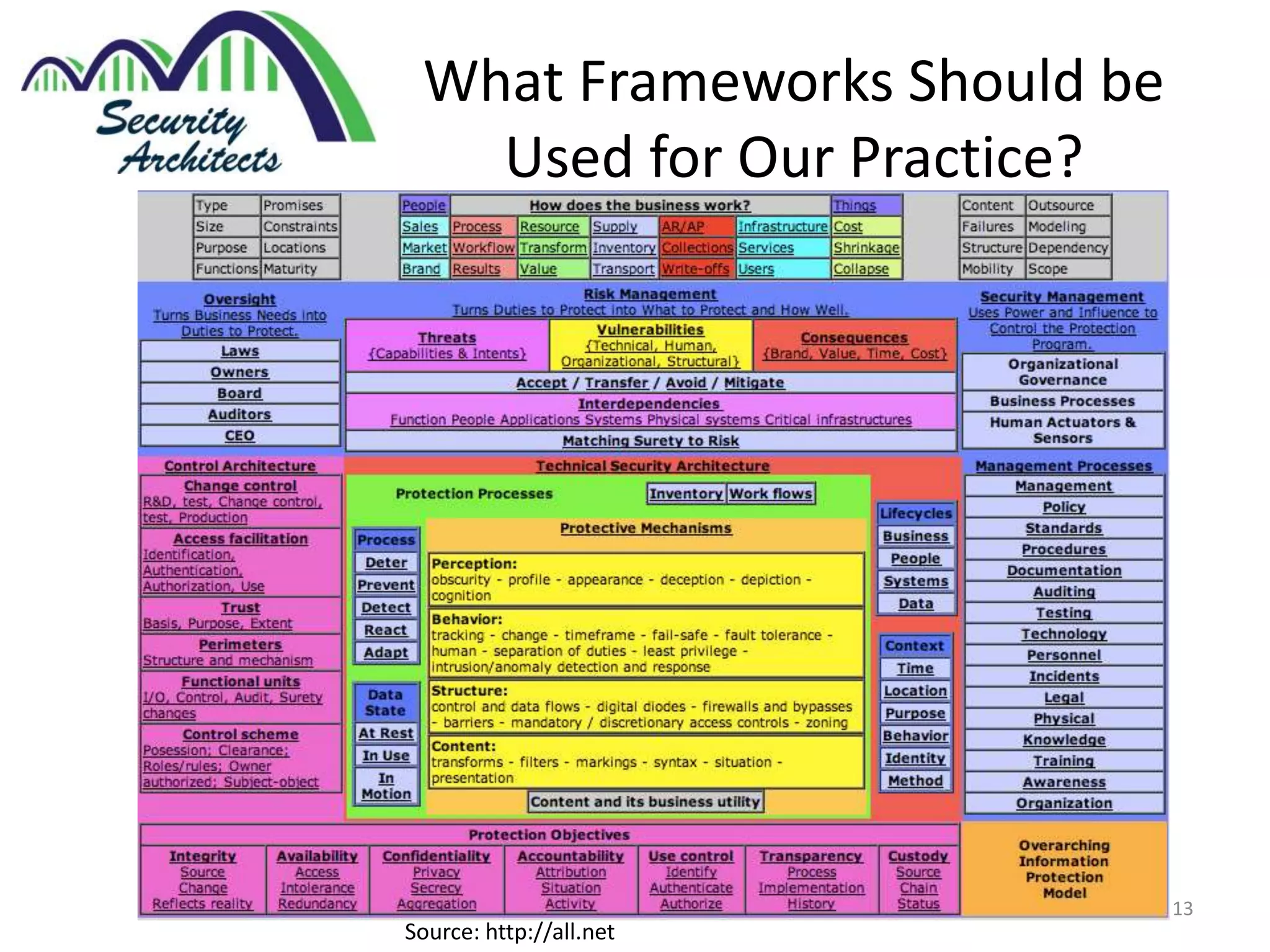
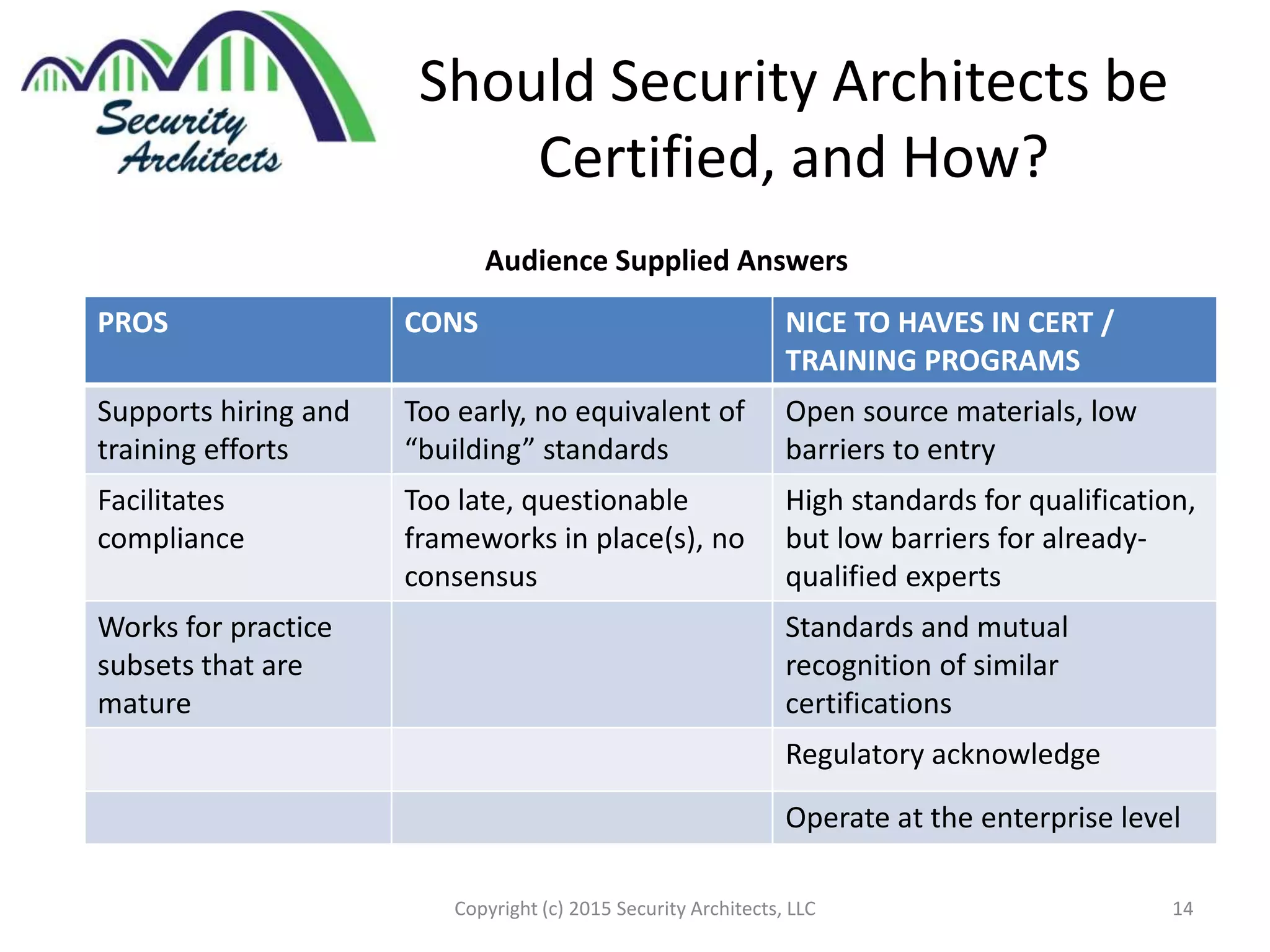
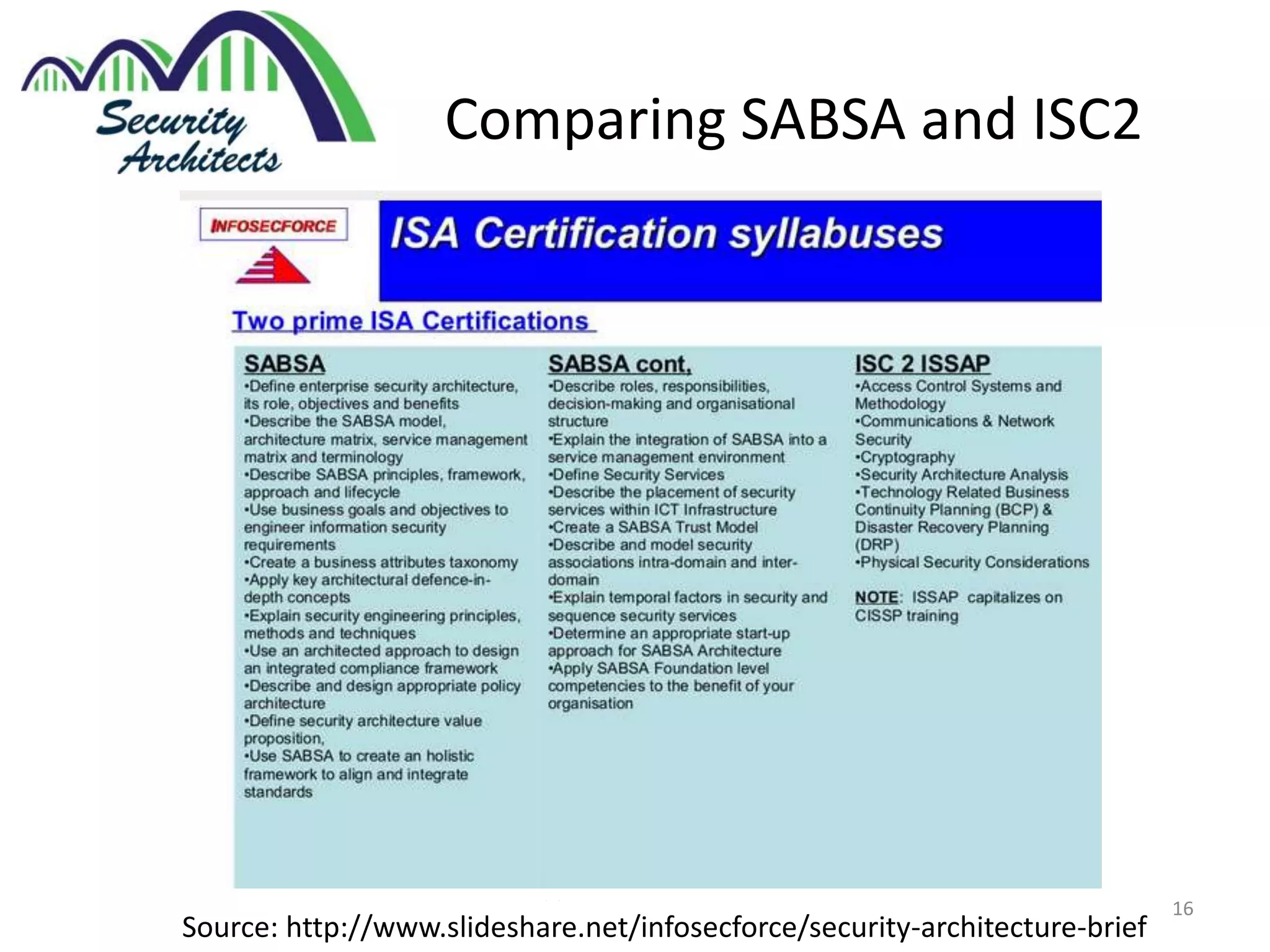
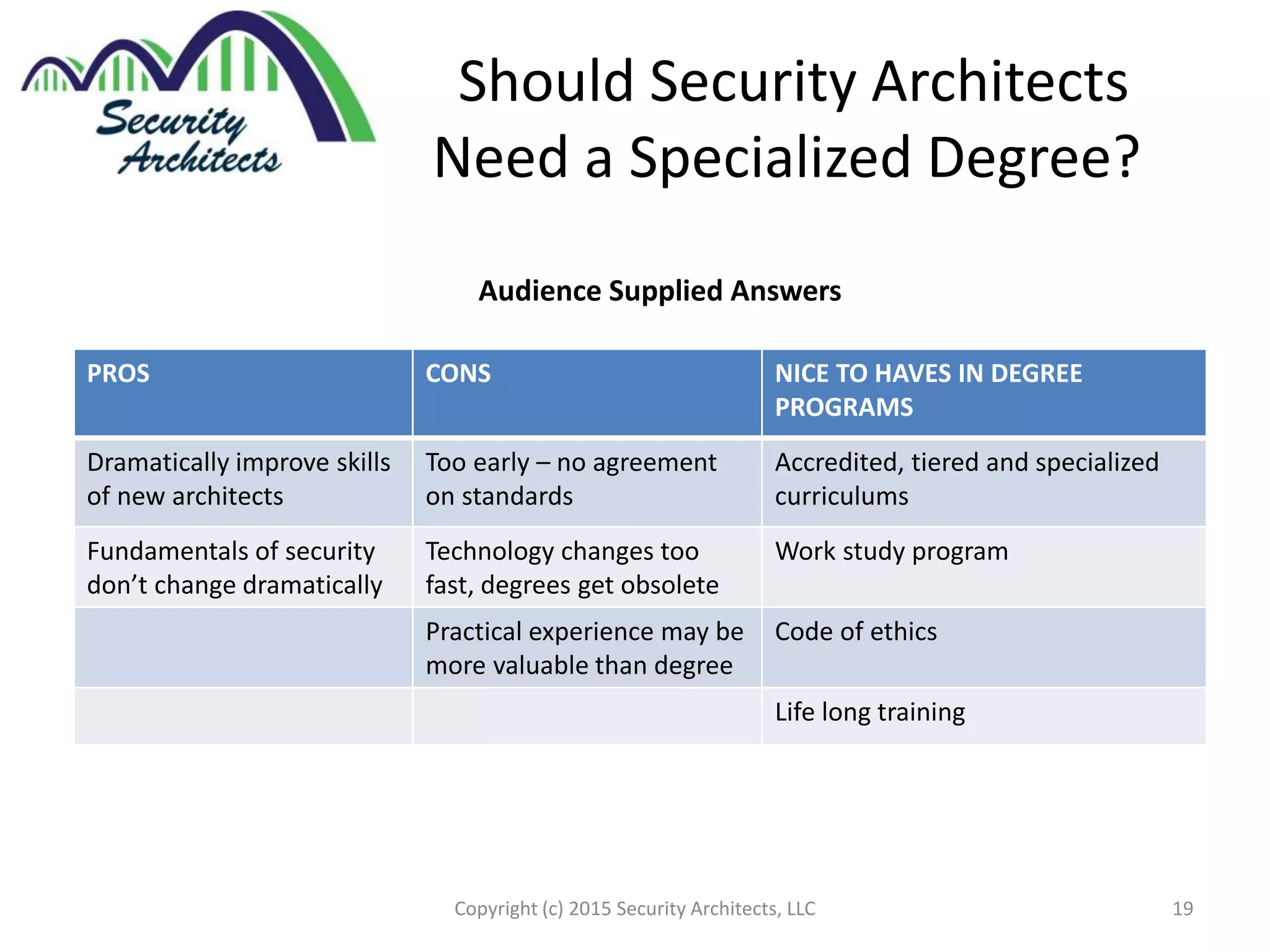
The document discusses the need for security architecture certification, highlighting the lack of consensus on definitions and requirements for security architects in a rapidly evolving tech landscape. It raises critical questions about the qualifications, frameworks, and training necessary for security architects and suggests that certification could support hiring and training efforts, despite potential challenges regarding standardization. The findings are based on contributions from various industry experts and organizations, including frameworks like SABSA and TOGAF.