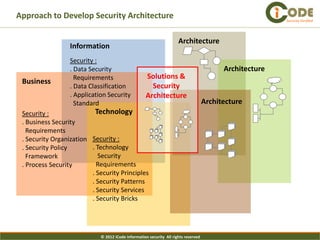
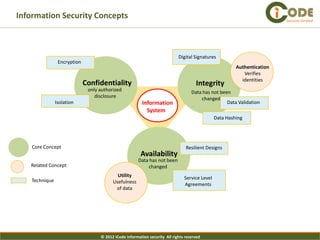
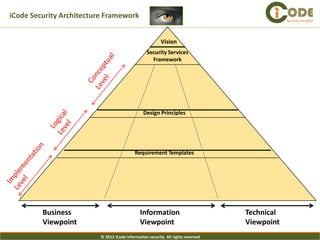
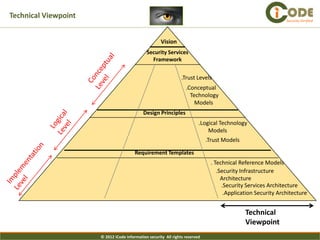
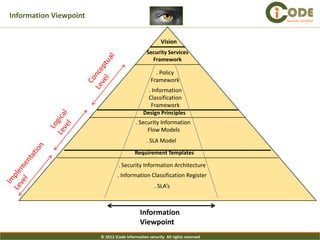
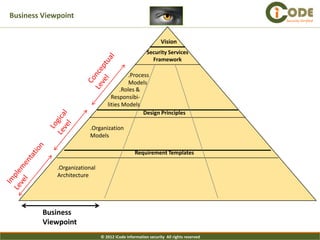
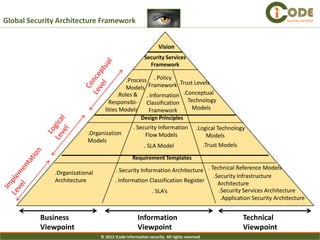
The document presents iCode's security architecture framework. The framework has three viewpoints: business, information, and technical. It uses a top-down approach with a global security vision and framework that defines security services, design principles, and requirement templates. These are then applied to each of the three viewpoints to develop models addressing things like processes, policies, information flows, and technical security components. The framework is designed to develop comprehensive and aligned security architectures.