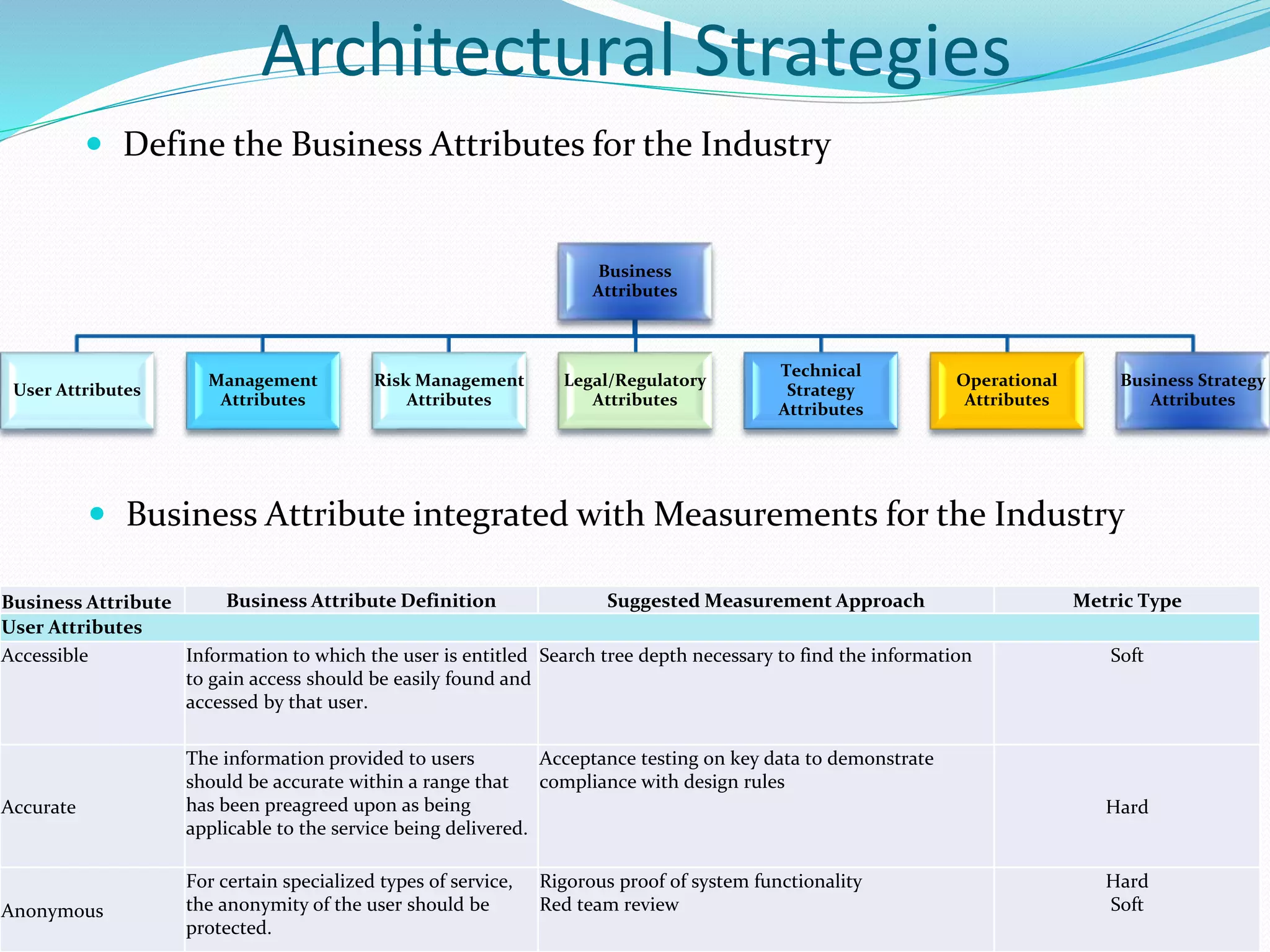
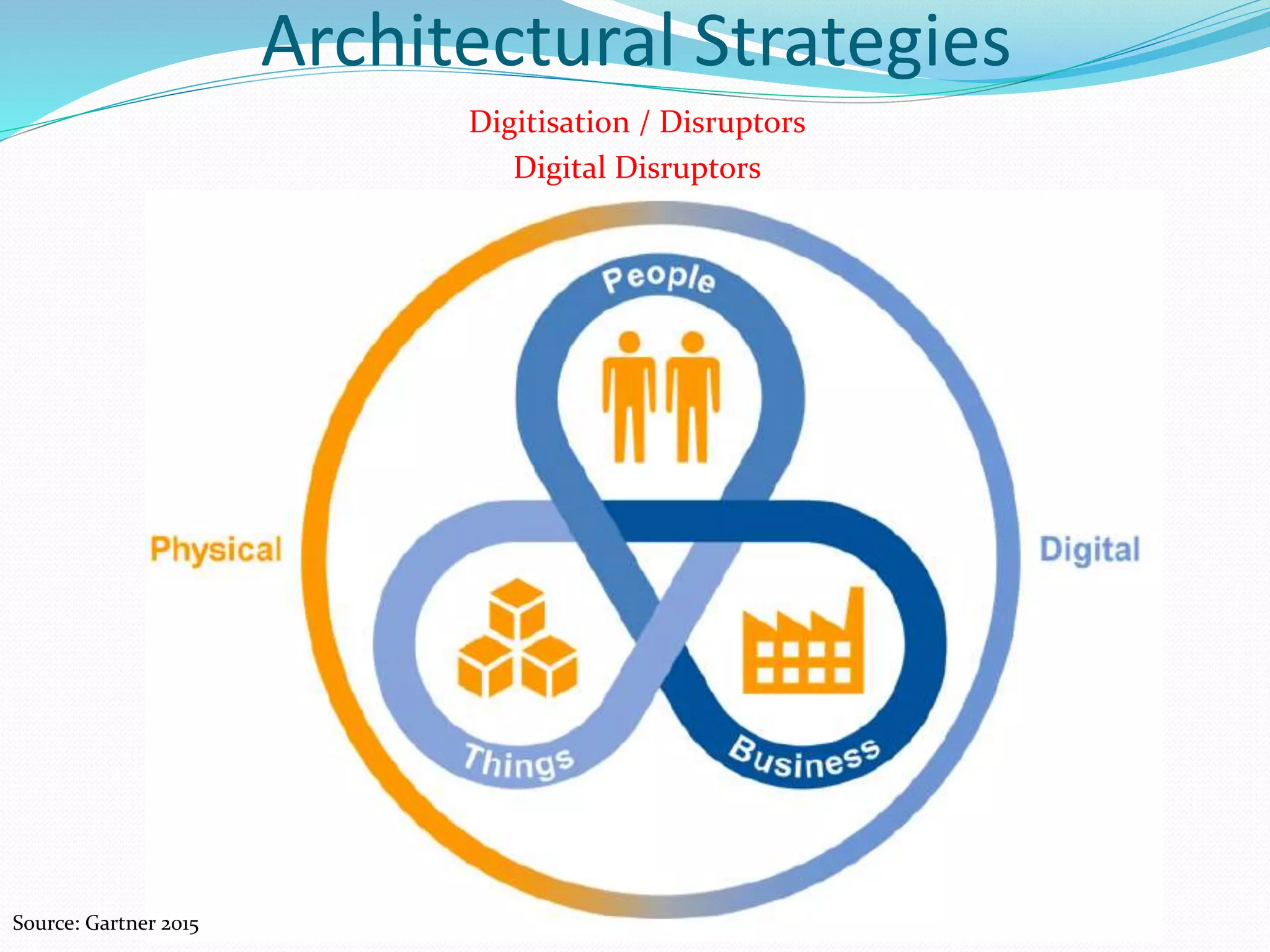
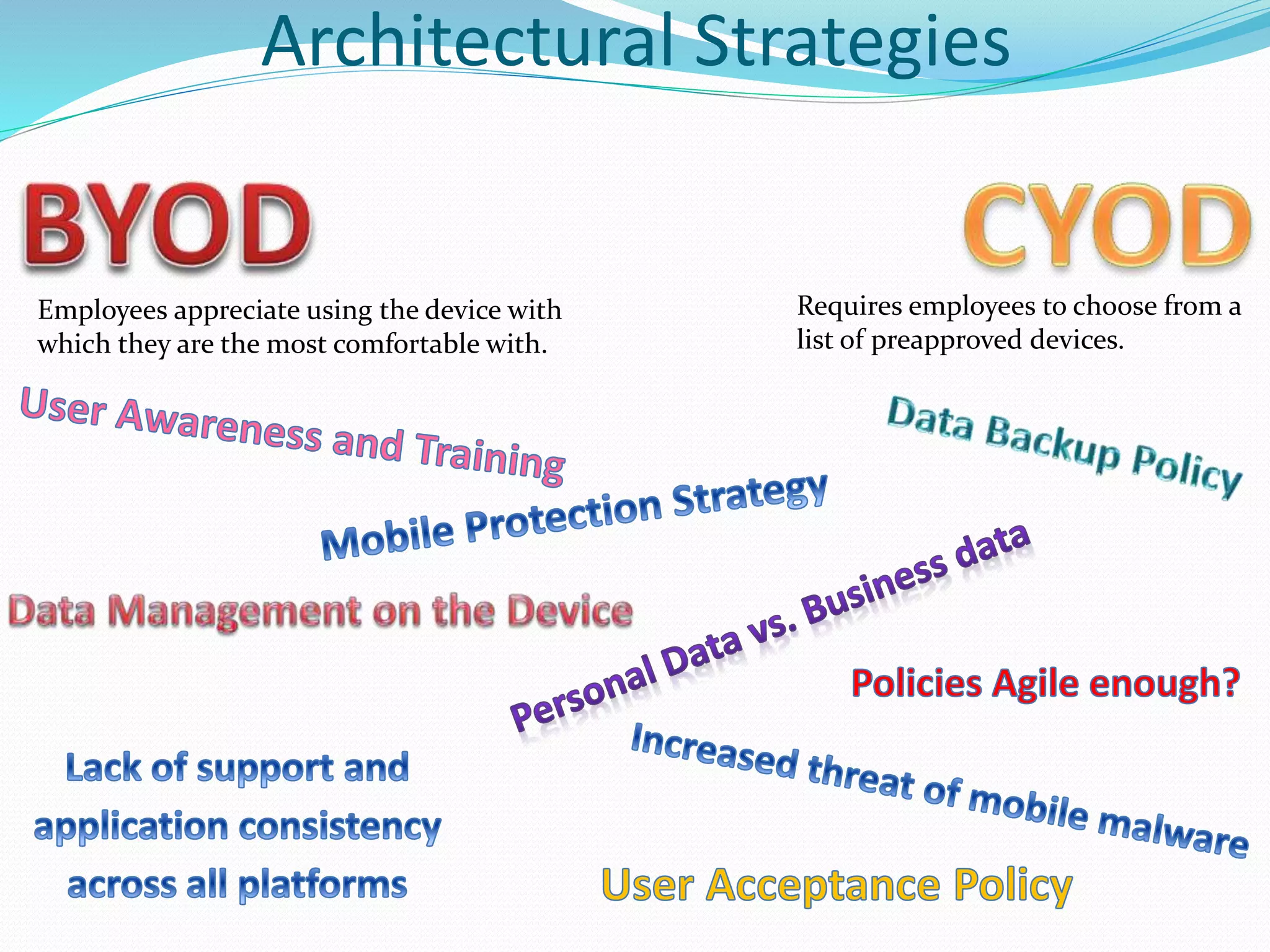
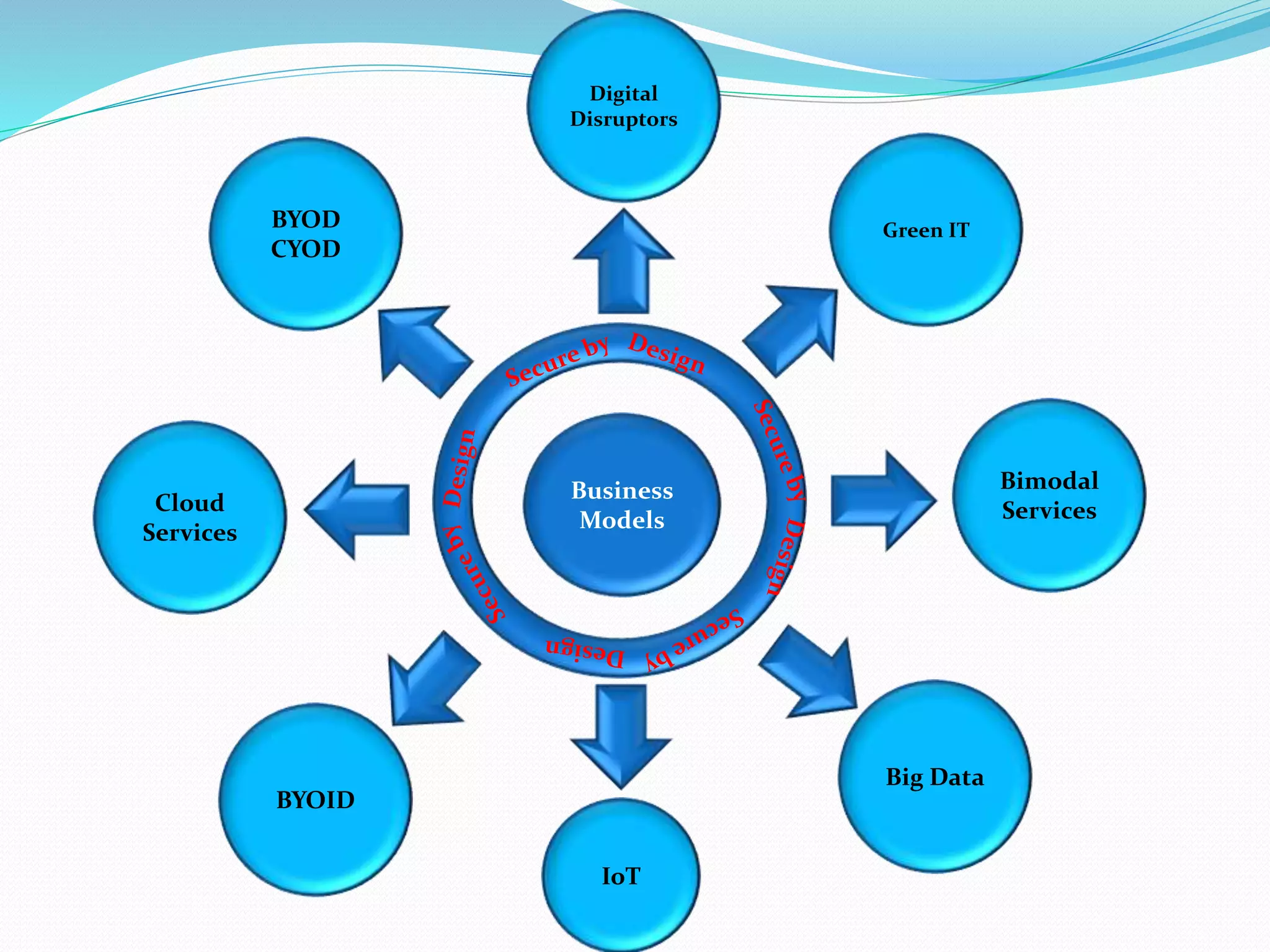
The document discusses various topics related to enterprise architecture including:
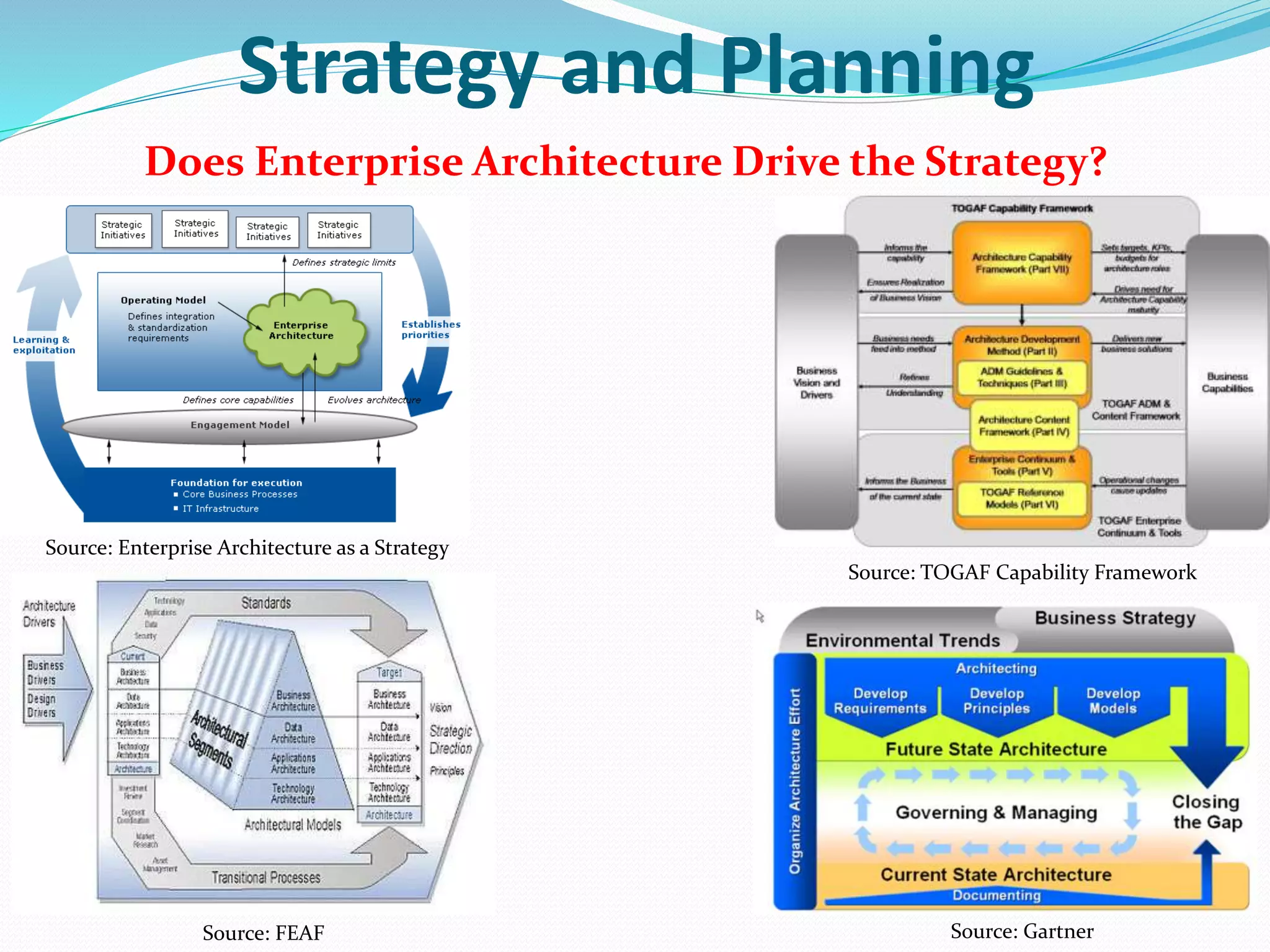
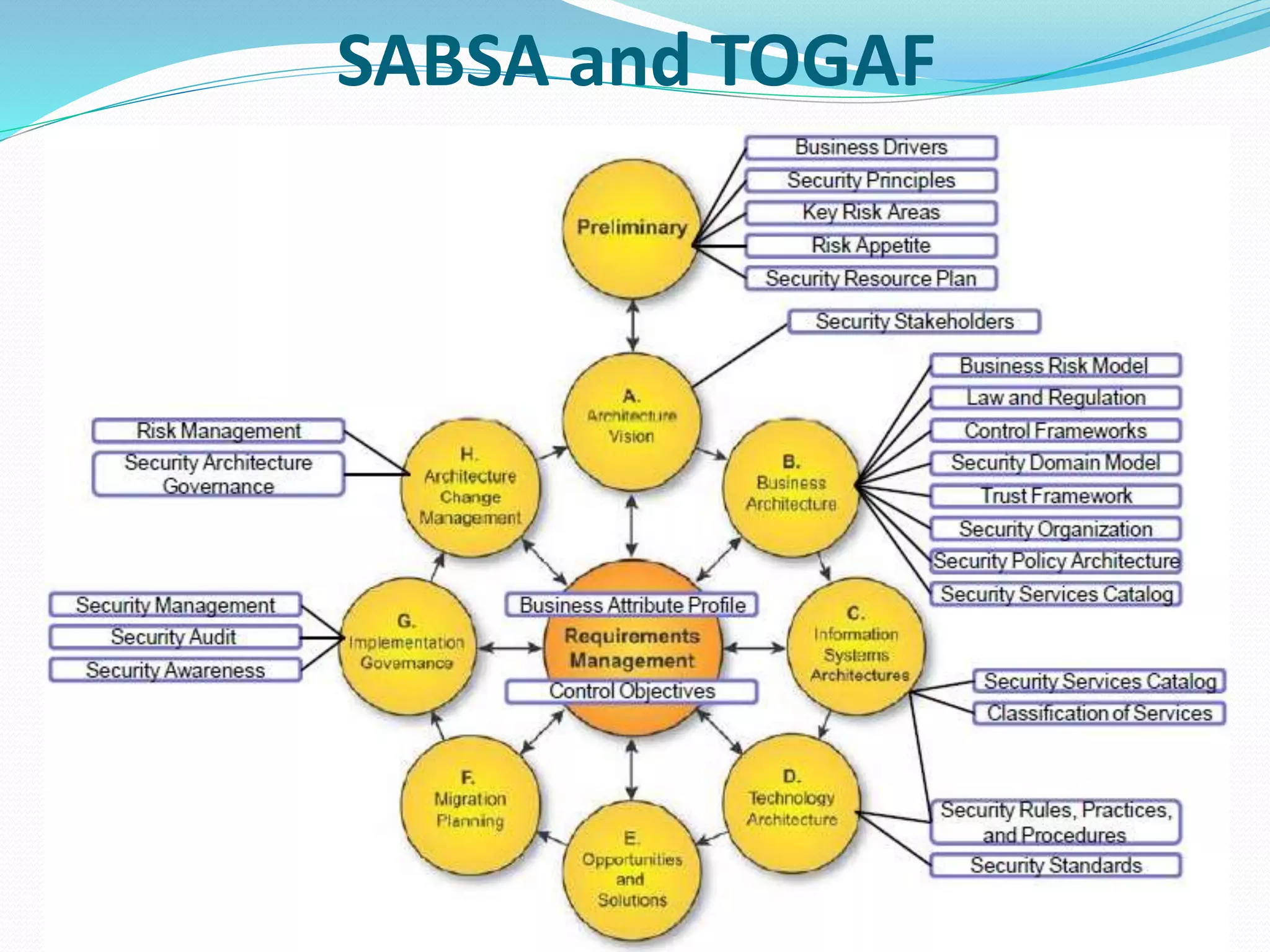
- Strategy and planning, with discussions of how architecture supports strategy.
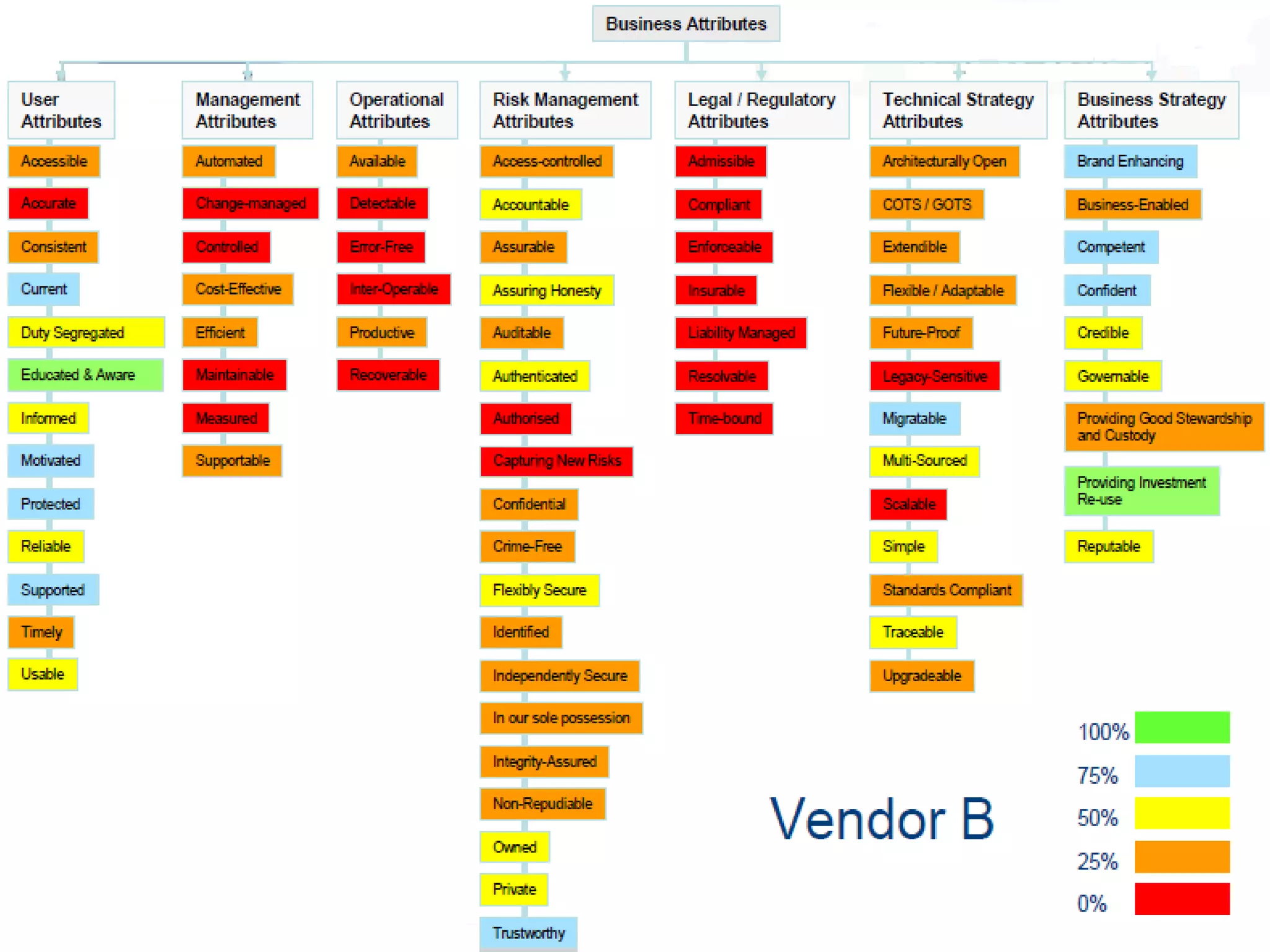
- Risk and opportunity, including regulatory drivers and using a risk-focused approach.
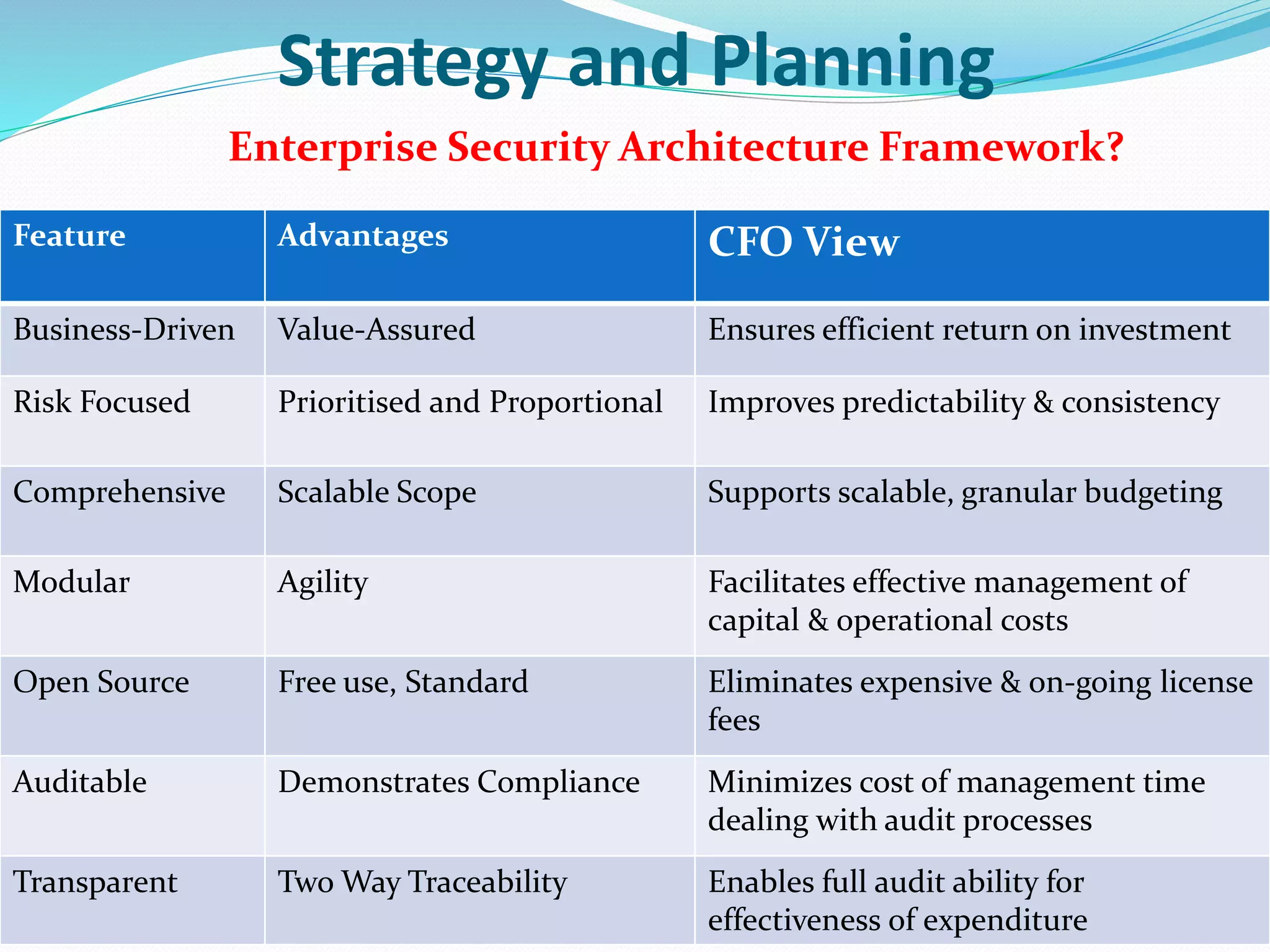
- Business context and requirements, emphasizing the need for a business-driven architecture.
- Architectural strategies such as Internet of Things, cloud computing, bimodal IT, and approaches to digitization and disruptors.