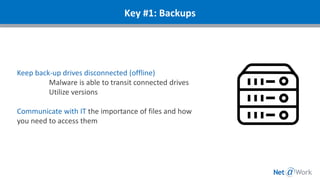
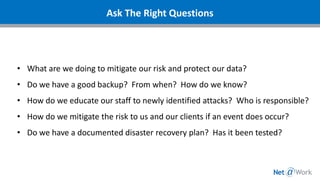
This webinar discussed cybersecurity best practices for small businesses. It covered current types of attacks like malware, denial of service, and ransomware. The presenters recommended best practices including regular backups, managing technical vulnerabilities, security awareness training, having an incident response plan, effective communication and testing of the plan, and security monitoring. They argued that managed IT services can help businesses implement these practices and mitigate security risks in a cost-effective way. The webinar provided resources for attendees and took questions at the end.