Embed presentation
Downloaded 69 times




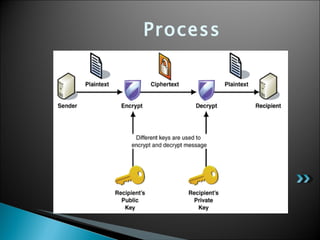
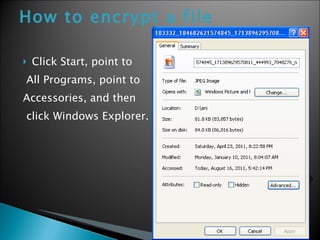
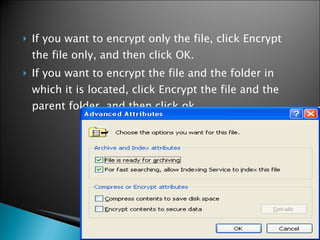


The document discusses encryption and provides instructions on how to encrypt files in Windows XP. It defines encryption as converting data into a secret code that can only be read by those with access to the decryption key. It notes that encryption protects documents by scrambling the text like a locked locker system. The document outlines the benefits of encryption like flexibility and transparency. It then provides step-by-step instructions for encrypting a file in Windows XP by using the Windows Explorer and selecting whether to encrypt just the file or the file and its parent folder. Finally, it briefly introduces common encryption types and terms like symmetric encryption using one key, asymmetric using public and private keys, and defines encrypting and decrypting data.










