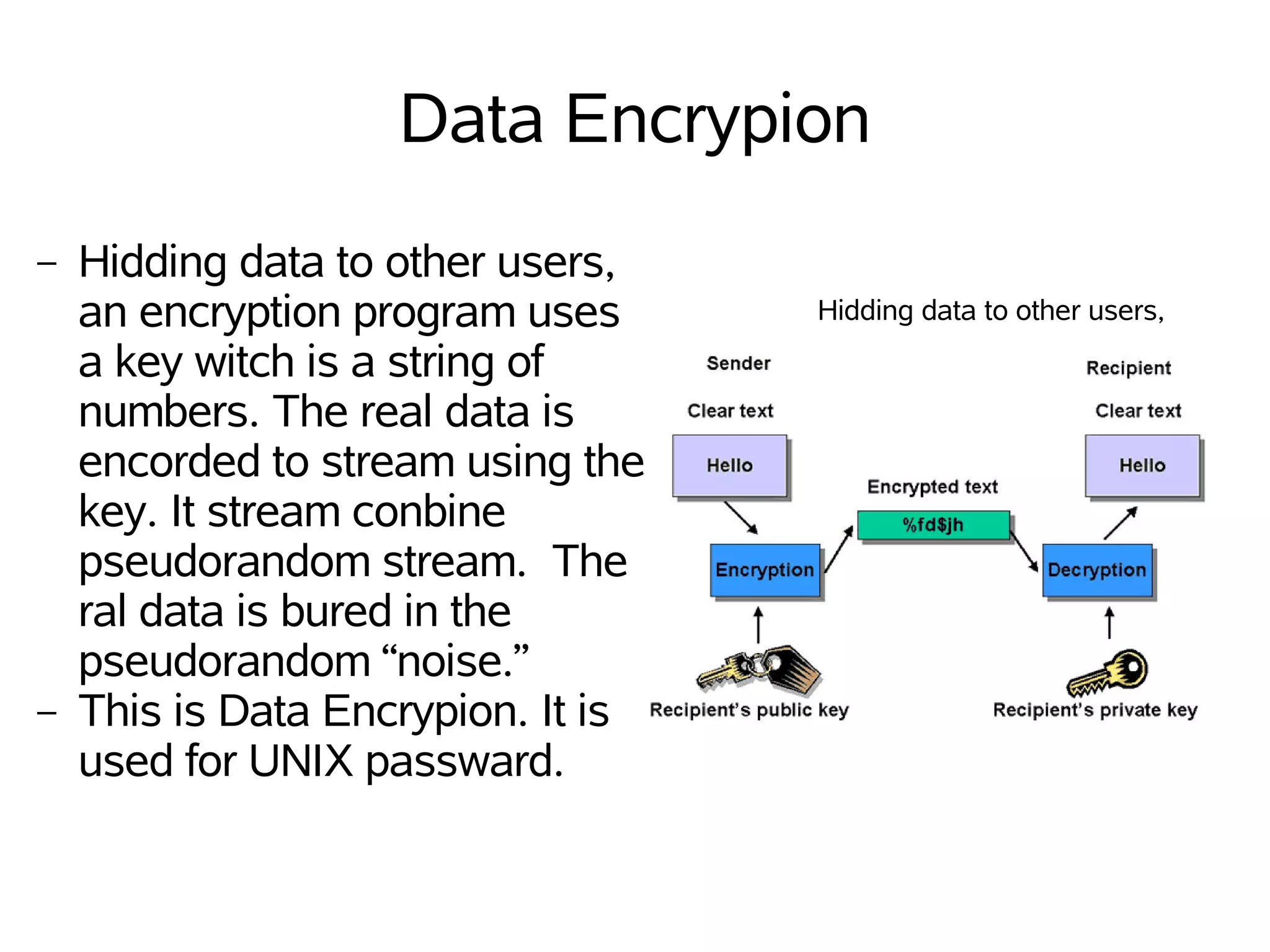
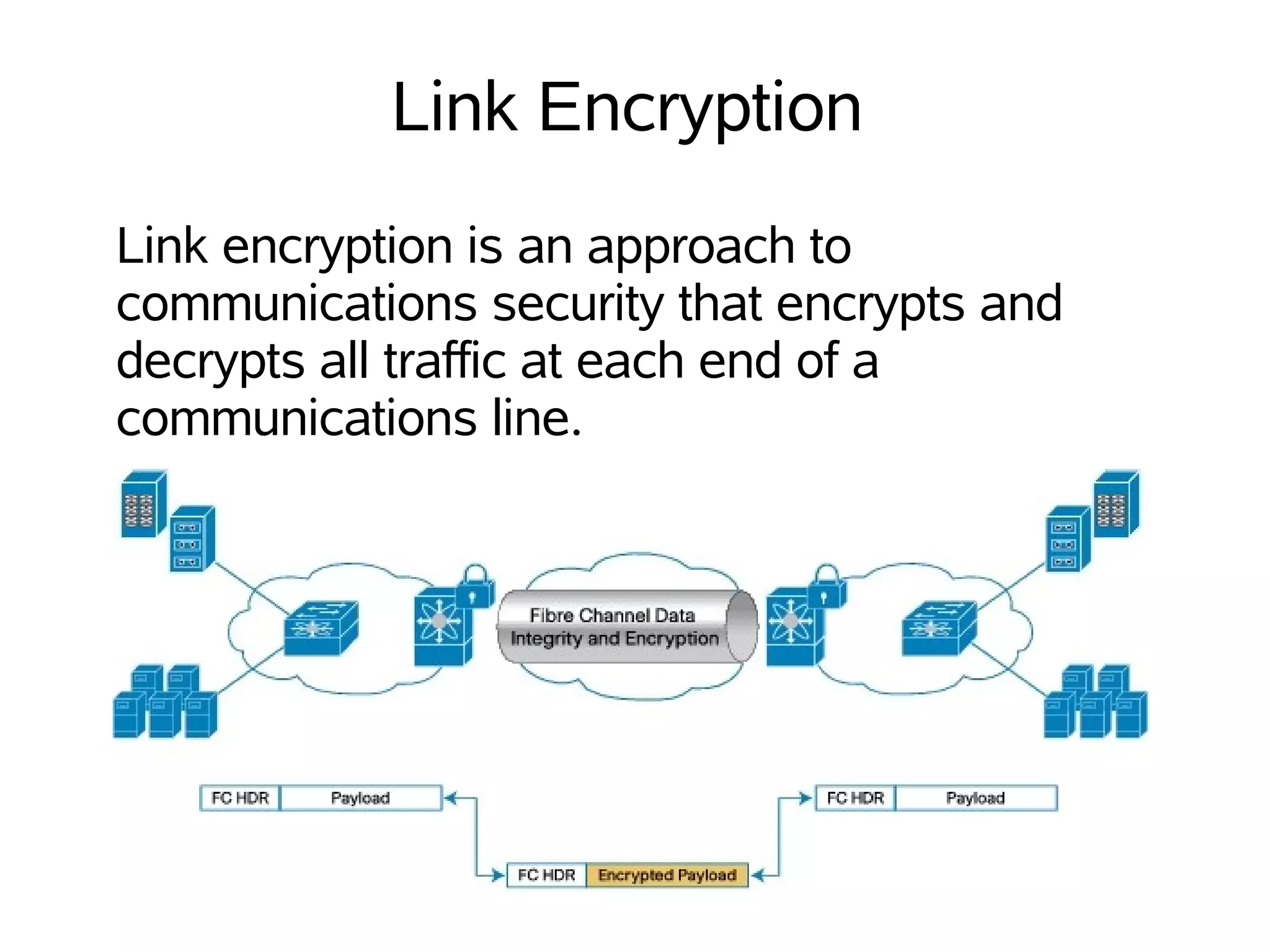
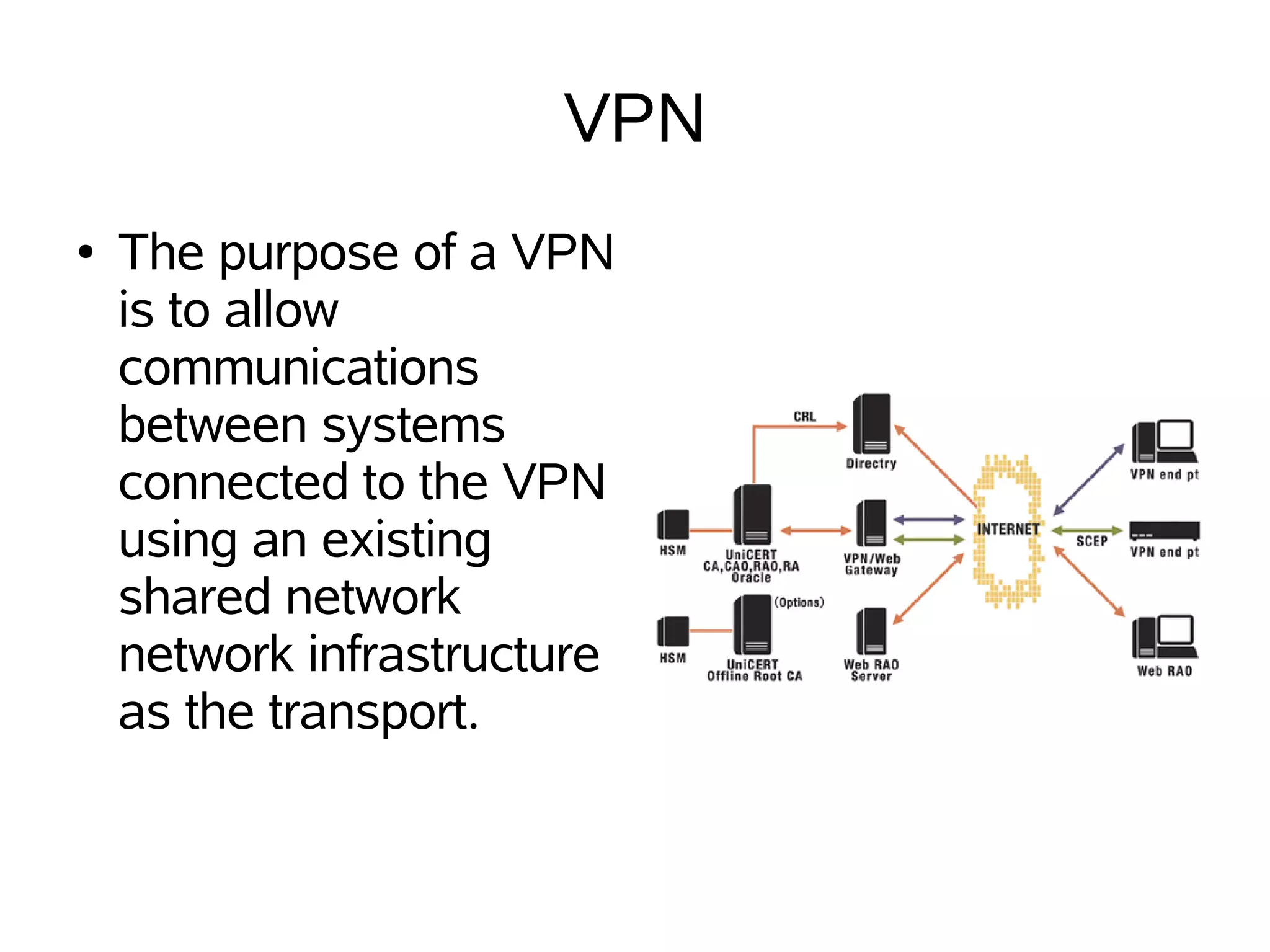
File, data, and link encryption as well as VPNs are described. File encryption encrypts files to protect them from being read or altered without a key. Data encryption hides data from other users by encoding it using a key into a pseudorandom stream. Link encryption encrypts all traffic at each end of a communications line. A VPN allows communication between systems using an existing shared network infrastructure.