Embed presentation
Download to read offline





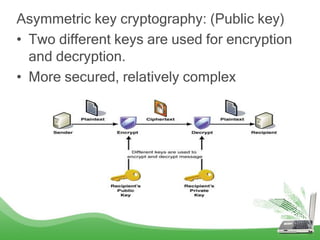



Cryptography is the process of securing communication and information by converting plain text into cipher text using cryptographic algorithms and keys. There are two main types: symmetric key cryptography which uses a single private key for encryption and decryption and is faster but less secure, and asymmetric key cryptography which uses two different keys (public and private) and is more complex but more secure. The purpose of cryptography is to defend against hackers and securely transmit sensitive information such as financial transactions, intellectual property, and other private communications.








