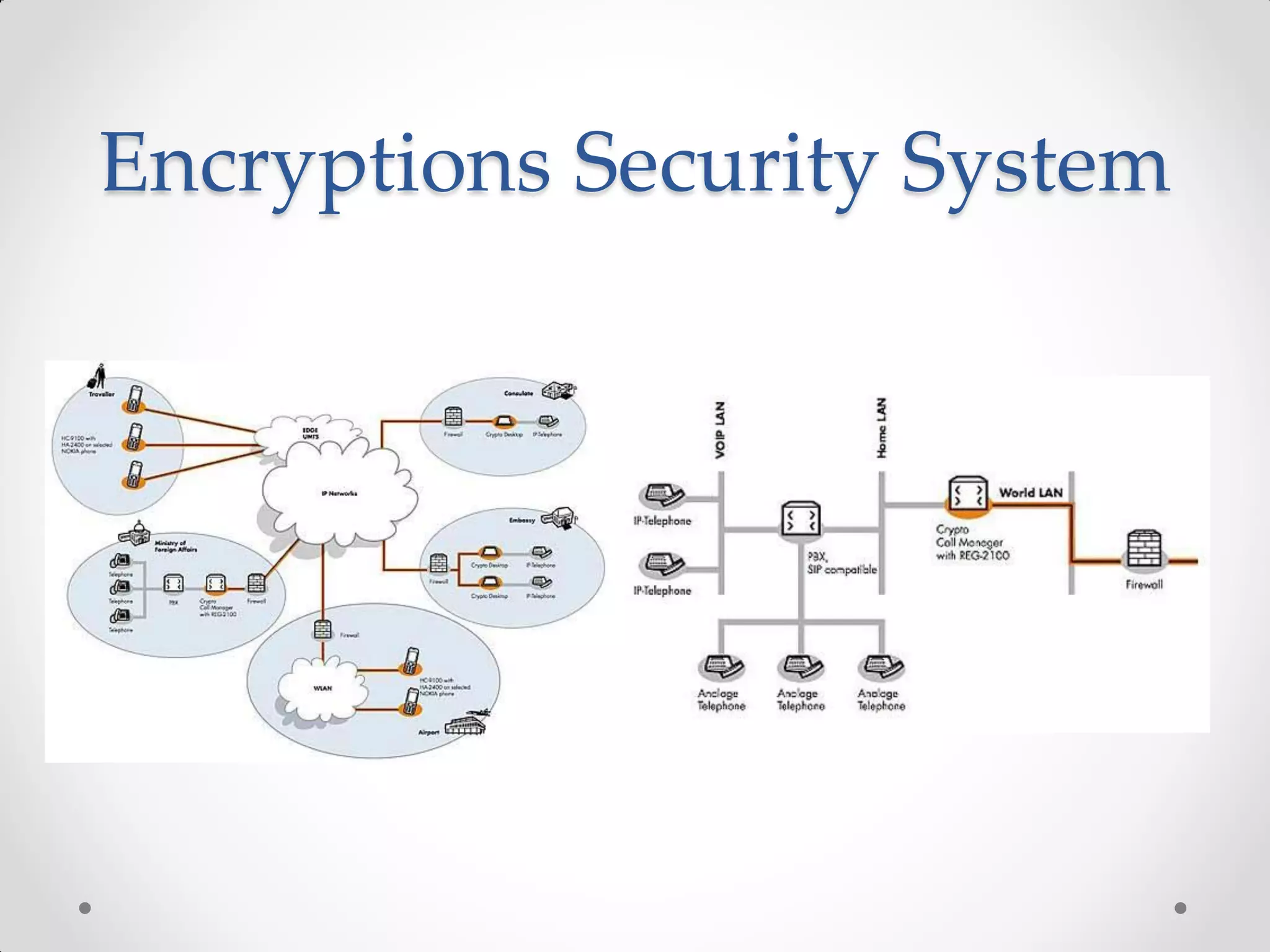
Encryption uses keys to scramble files and make them hidden. There are two main encryption systems: symmetric key encryption which uses the same key shared between sender and receiver, and public key encryption which uses a secret key known only to the user and a public key to encrypt files. Common encryption protocols are SSL/TLS which encrypt web browser data during transmission between clients and servers. Encryption systems also use hashing algorithms to change data into hashed values.