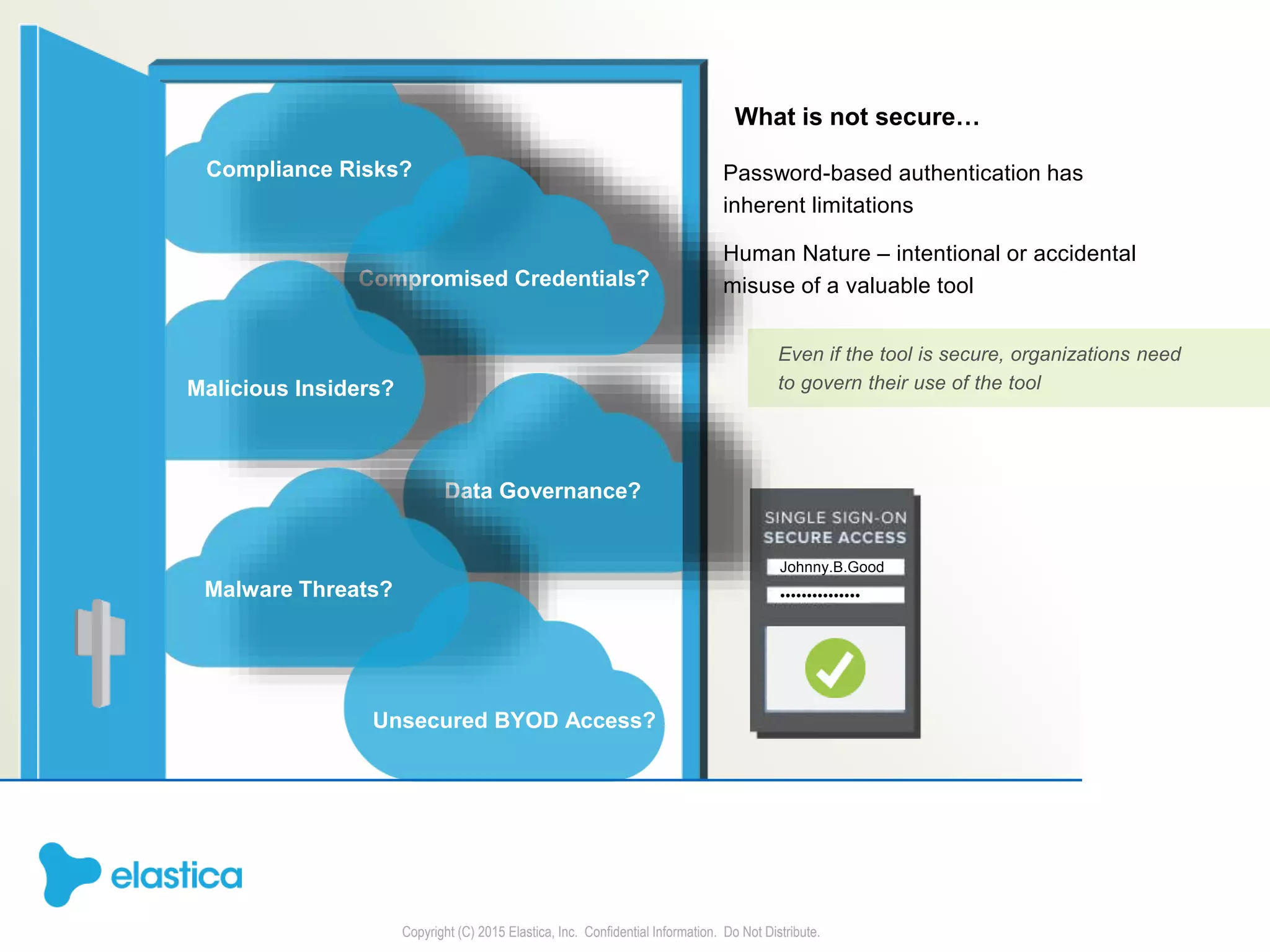
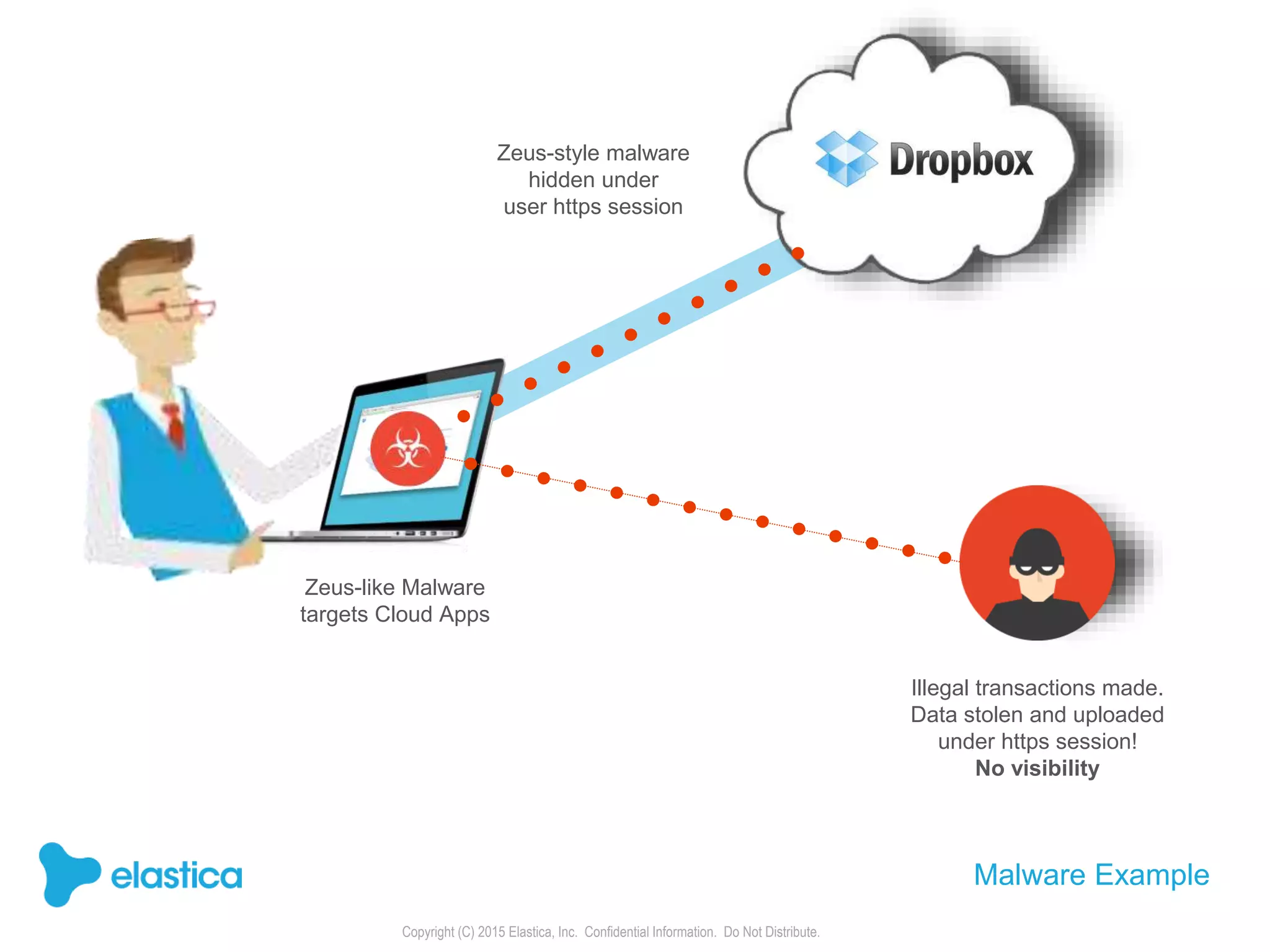
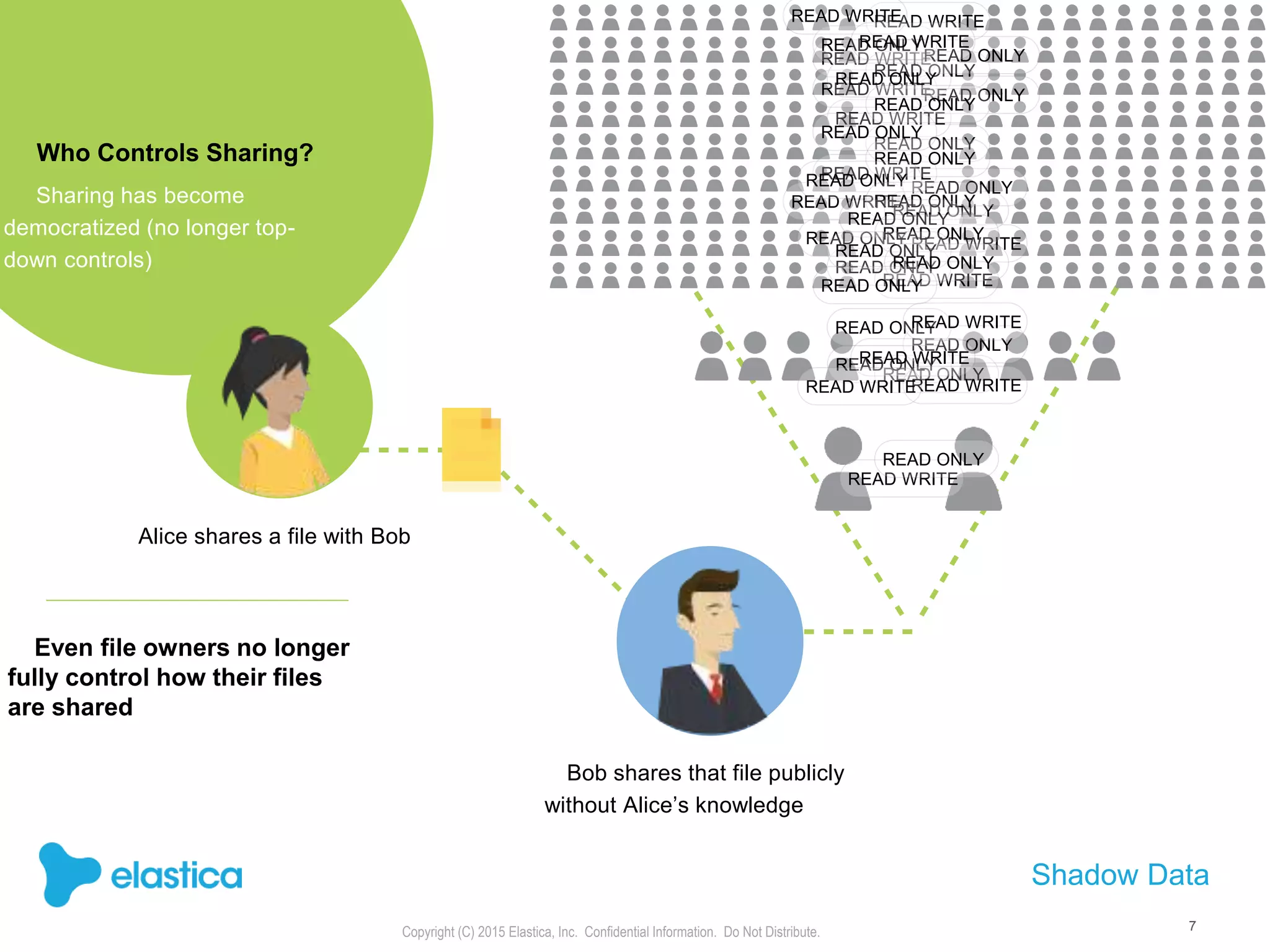
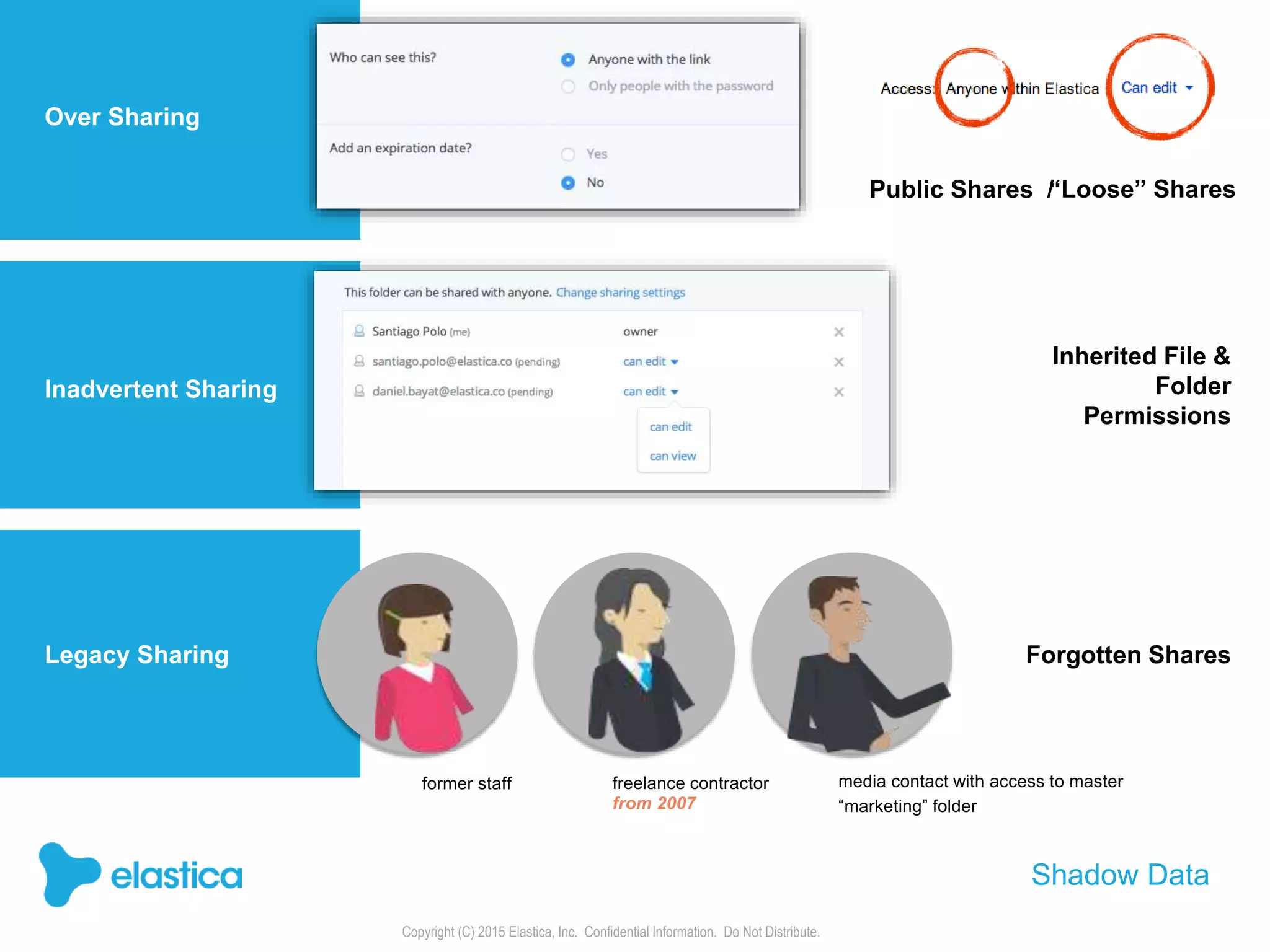
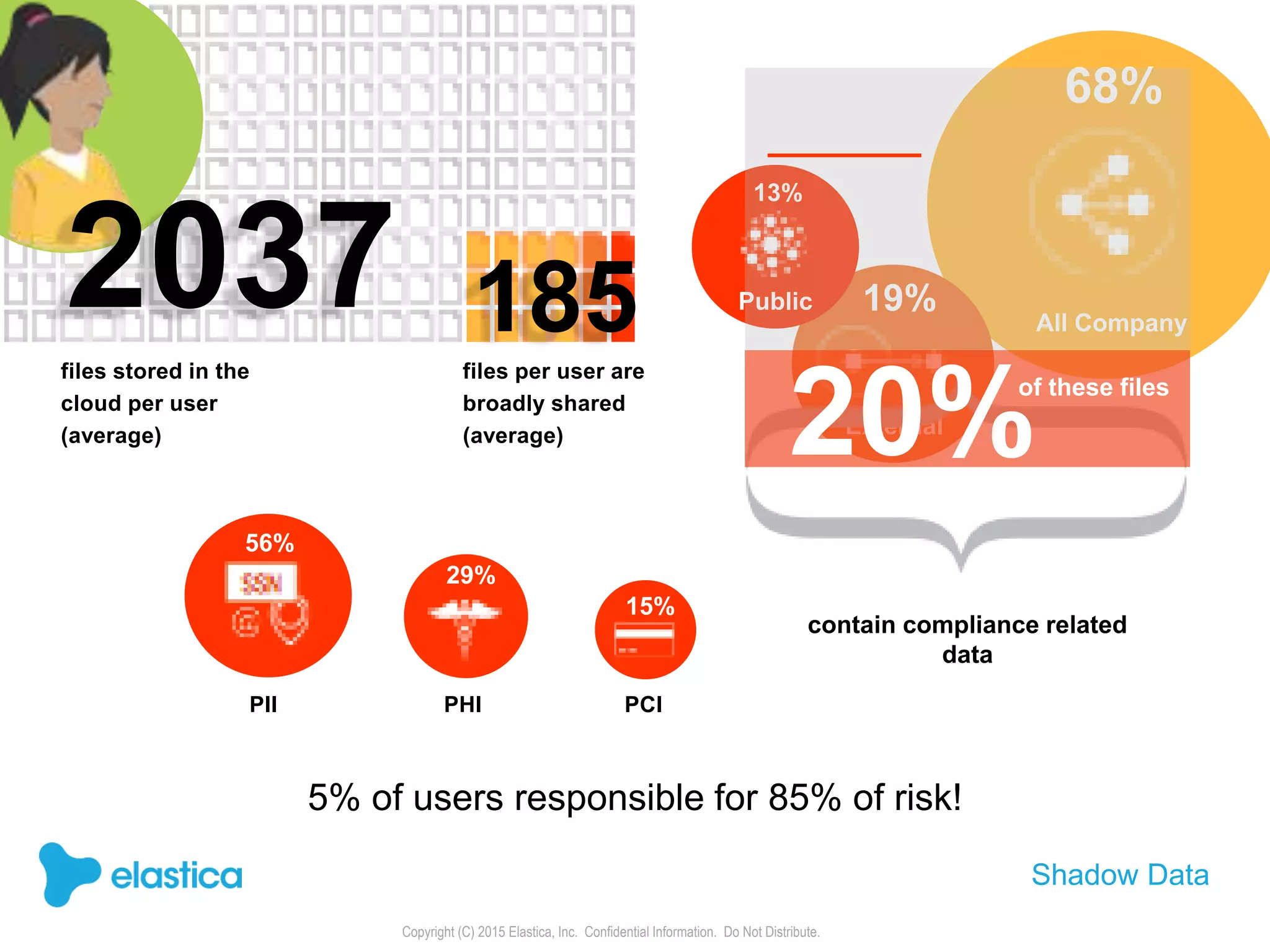
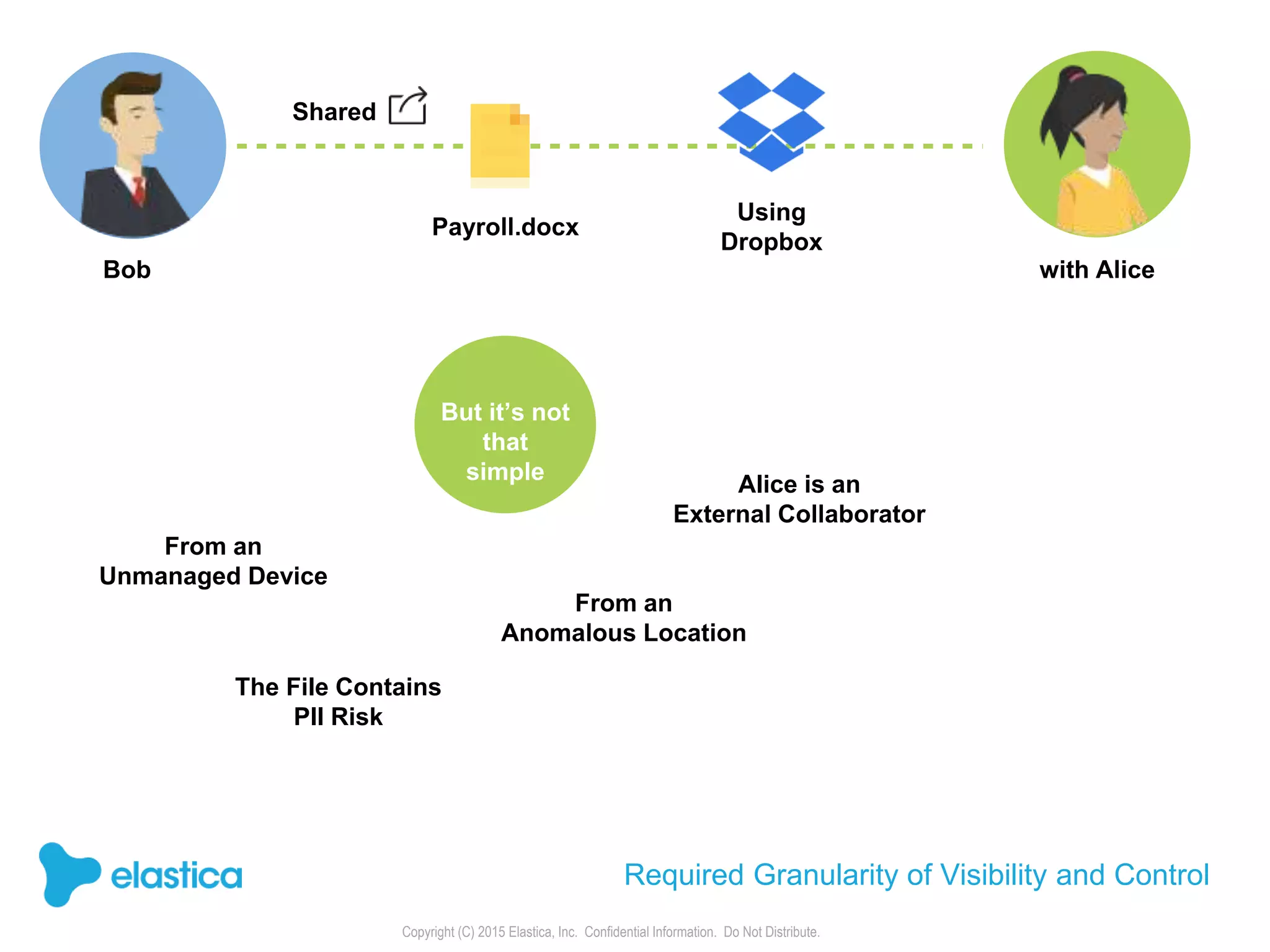
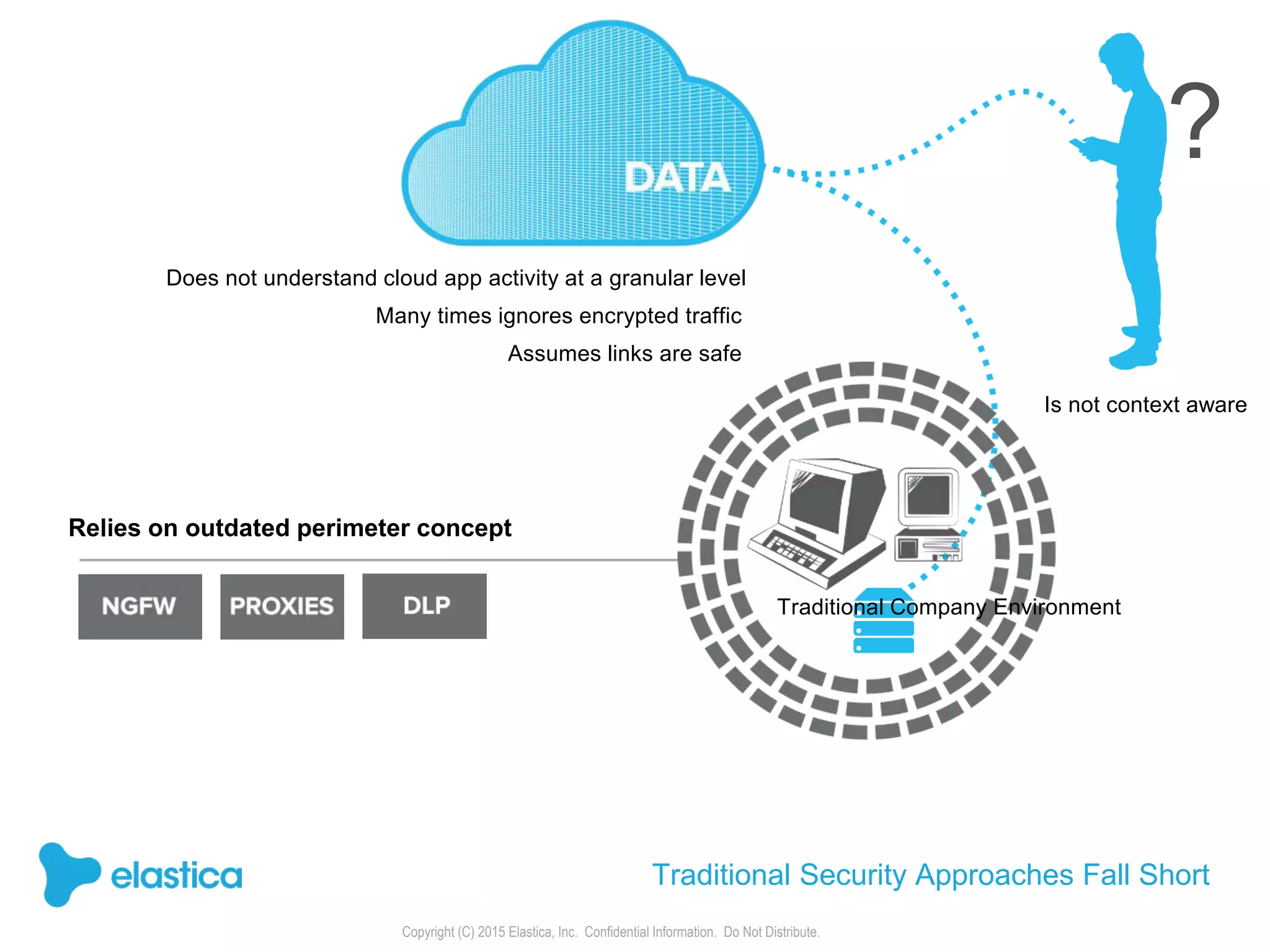
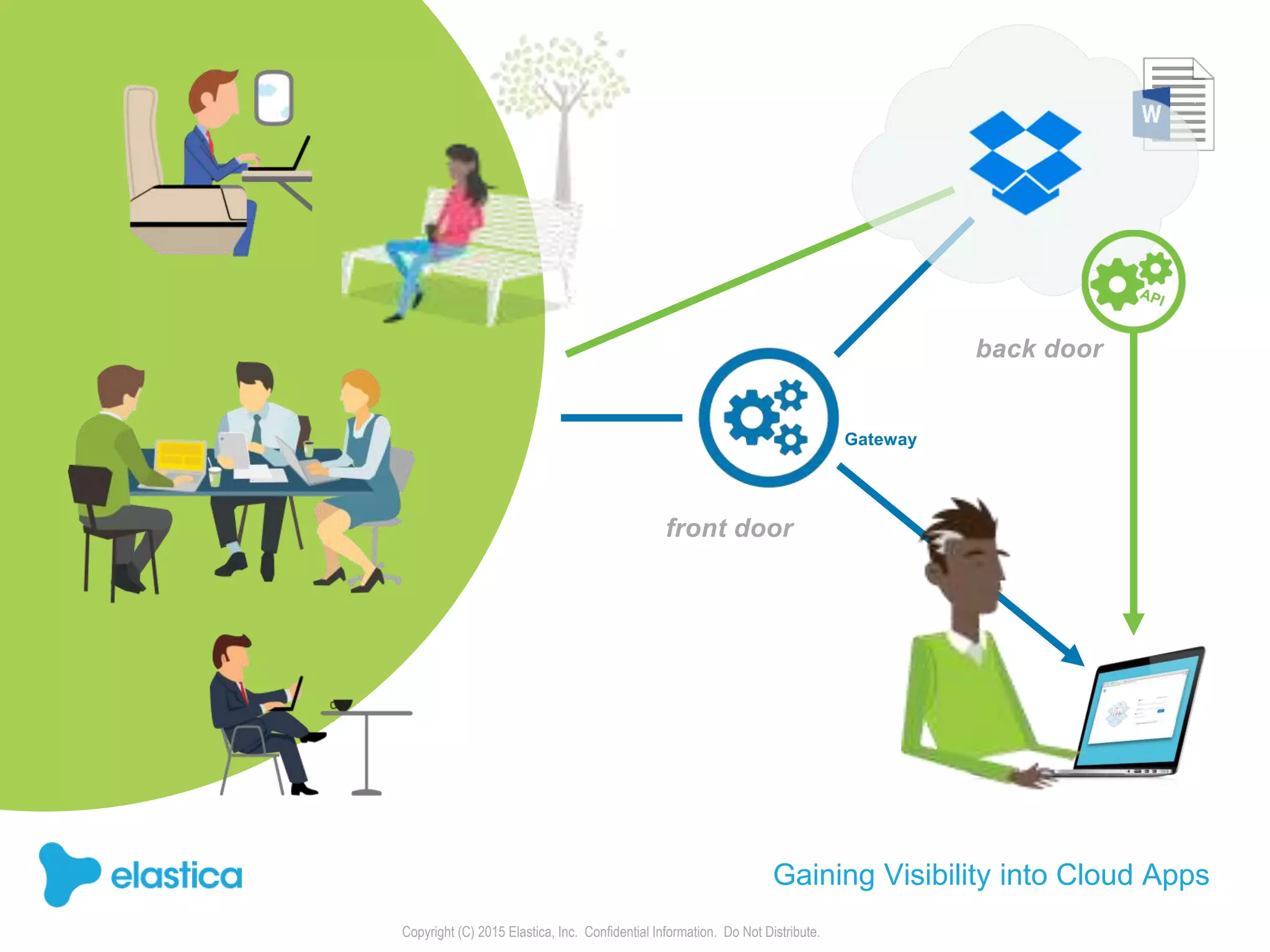
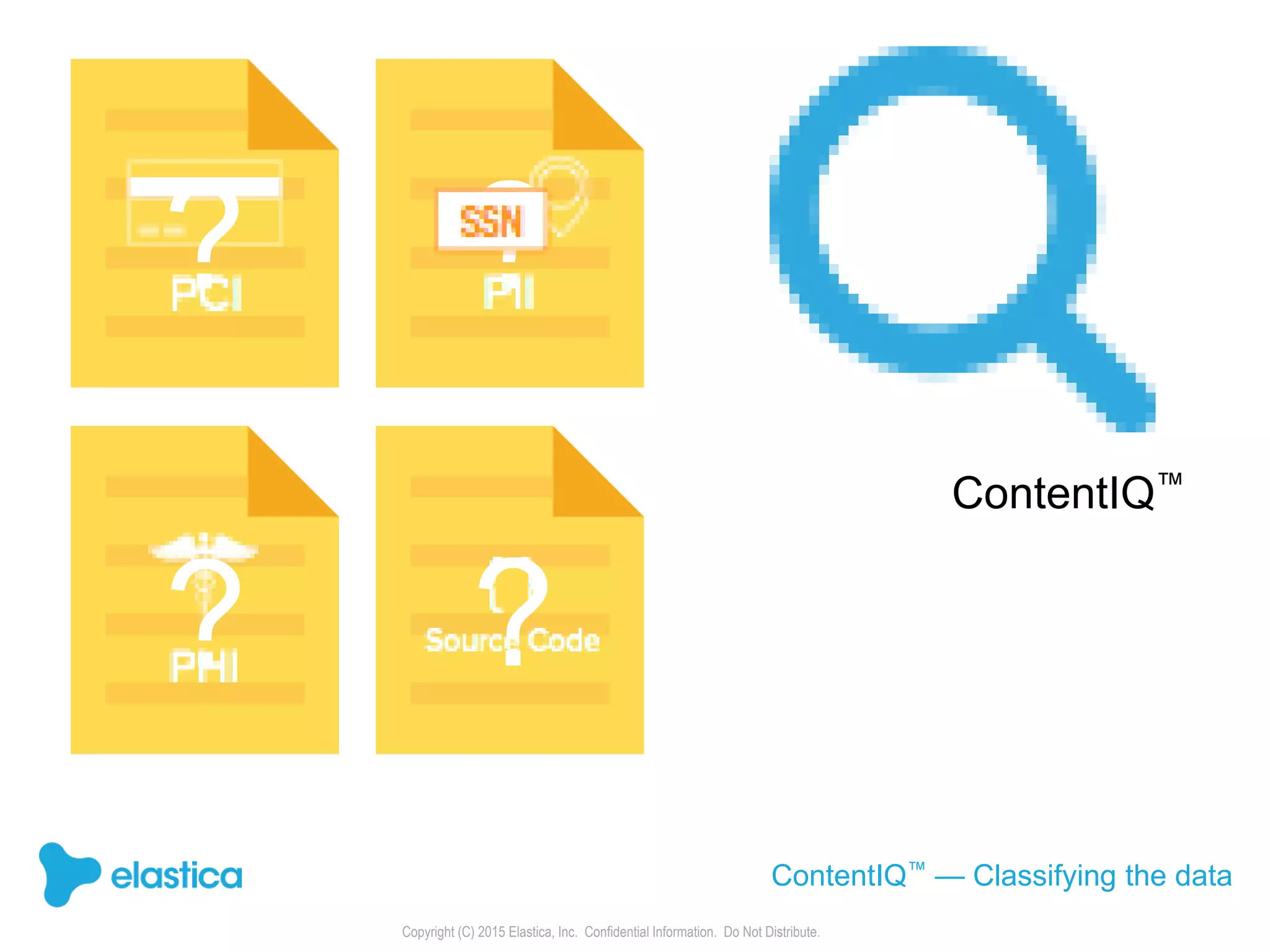
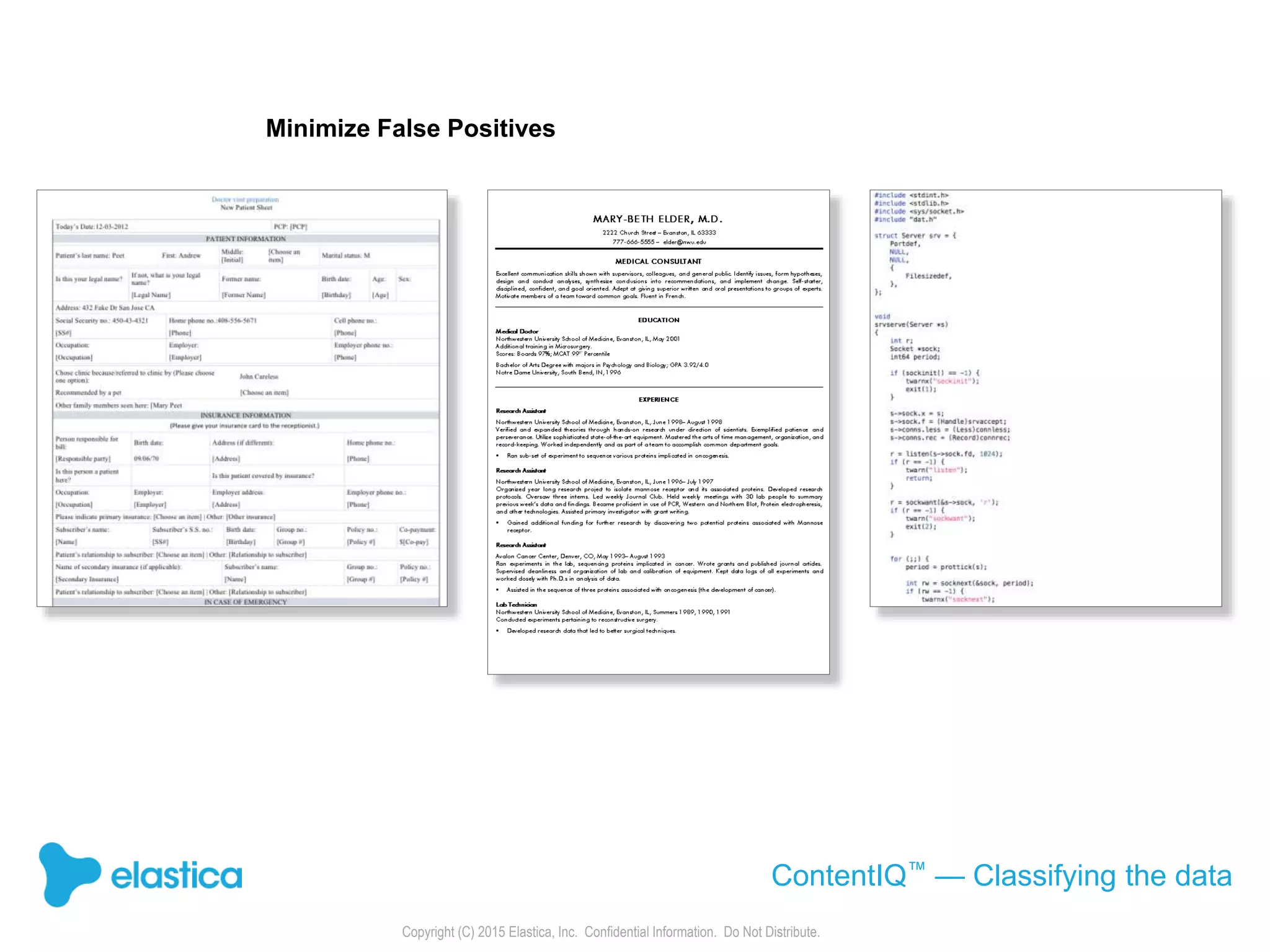
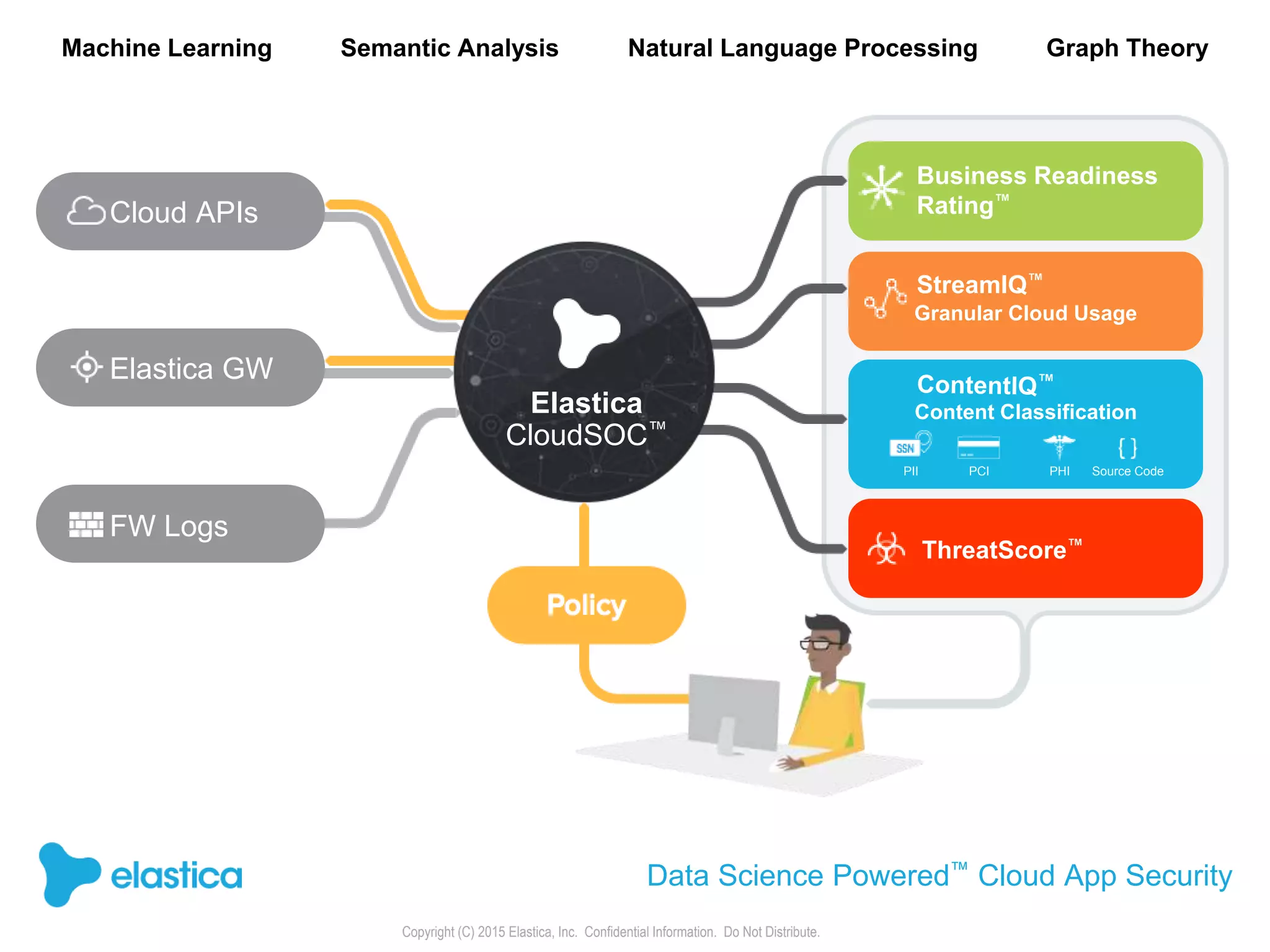
The document provides an overview of the security challenges and risks associated with using Dropbox for business, emphasizing issues like password-based authentication weaknesses, malware threats, and the democratization of file sharing. It outlines the importance of data governance and introduces Elastica's data science-powered solutions, which include tools for understanding cloud app activity, ensuring compliance, and protecting sensitive data. The presentation encourages organizations to assess their shadow data risks and offers actionable insights on how to enhance security when using cloud file sharing services.