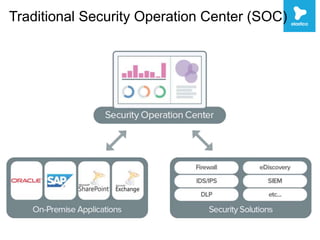
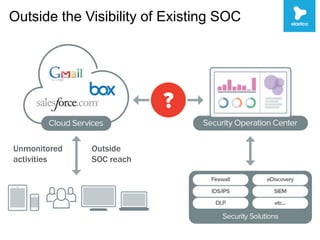
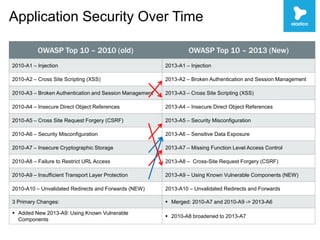
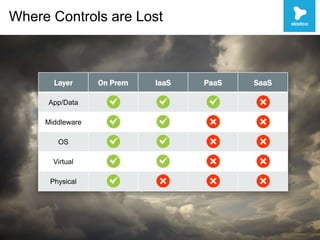
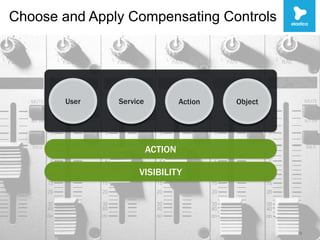
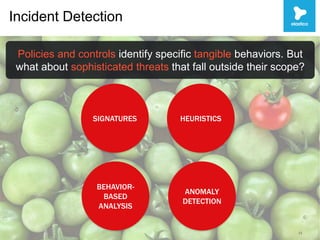
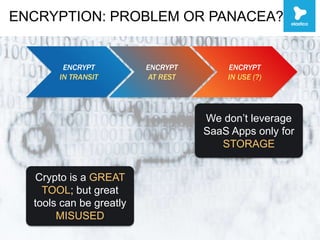
This document discusses security challenges with enterprise applications in cloud environments. It notes that traditional security controls are lost with different cloud layers and that visibility and understanding risks are important. The document outlines the threat lifecycle and how the landscape is changing. It argues that establishing baselines, choosing compensating controls, and incident detection and response are needed. Specific challenges with encryption, single sign-on, and application monitoring in cloud are discussed. The key takeaways are that cloud security problems are multifaceted and that visibility and action are important pillars across the threat lifecycle.