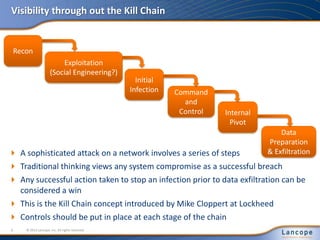
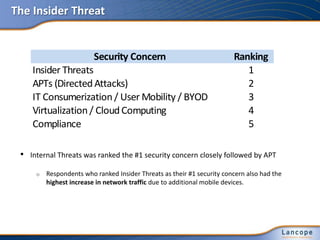
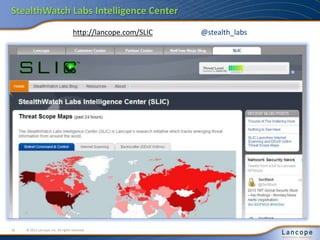
The document outlines five major cybersecurity challenges for 2013, including state-sponsored cyber intrusions, increasing DDoS attacks, issues related to IT consumerization and cloud services, problems surrounding password security, and the insider threat. It emphasizes the need for improved visibility and control measures, highlighting the importance of addressing these threats proactively through comprehensive strategies and collaboration among IT, HR, and legal departments. Additionally, recommendations for managing insider threats and adapting security policies are discussed.