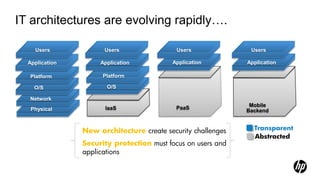
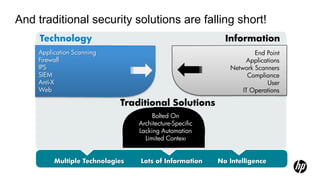
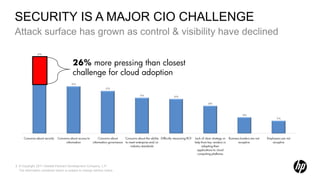
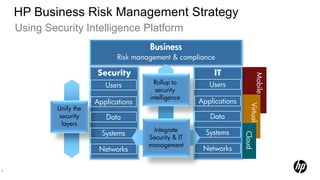
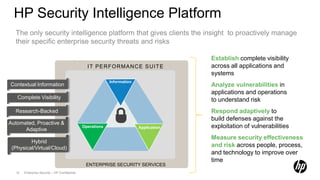
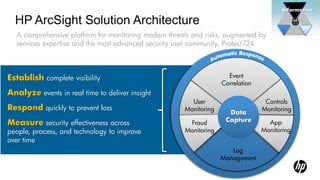
1) HP Enterprise Security provides a security intelligence platform to help organizations proactively manage threats and risks across their IT infrastructure.
2) The platform offers universal log management, regulatory compliance, network security, and other solutions to establish complete visibility and analyze security events.
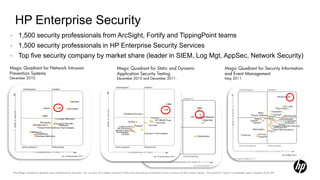
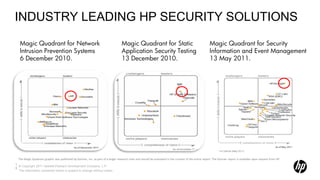
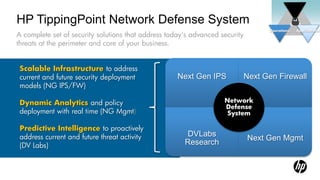
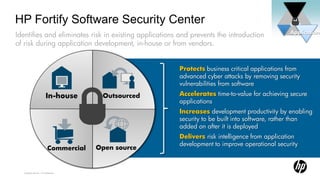
3) Key HP security products like ArcSight, Fortify, and TippingPoint provide advanced threat detection, application testing, and network defenses respectively.