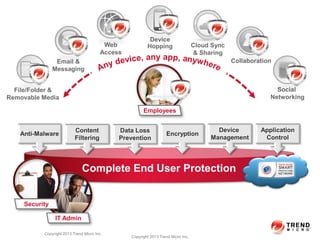
The document provides an overview of Trend Micro's smart protection strategy, which aims to empower businesses while efficiently mitigating risks. It discusses how information has become a strategic asset for organizations and the new threats they face from cybercriminals. Trend Micro's approach focuses on providing smart protection for information, security that is simple yet flexible to manage across evolving IT ecosystems, and defenses that fit organizations' needs. Key elements of the smart protection strategy include layered security, interconnected threat intelligence, real-time updates, and transparency with no user impact.