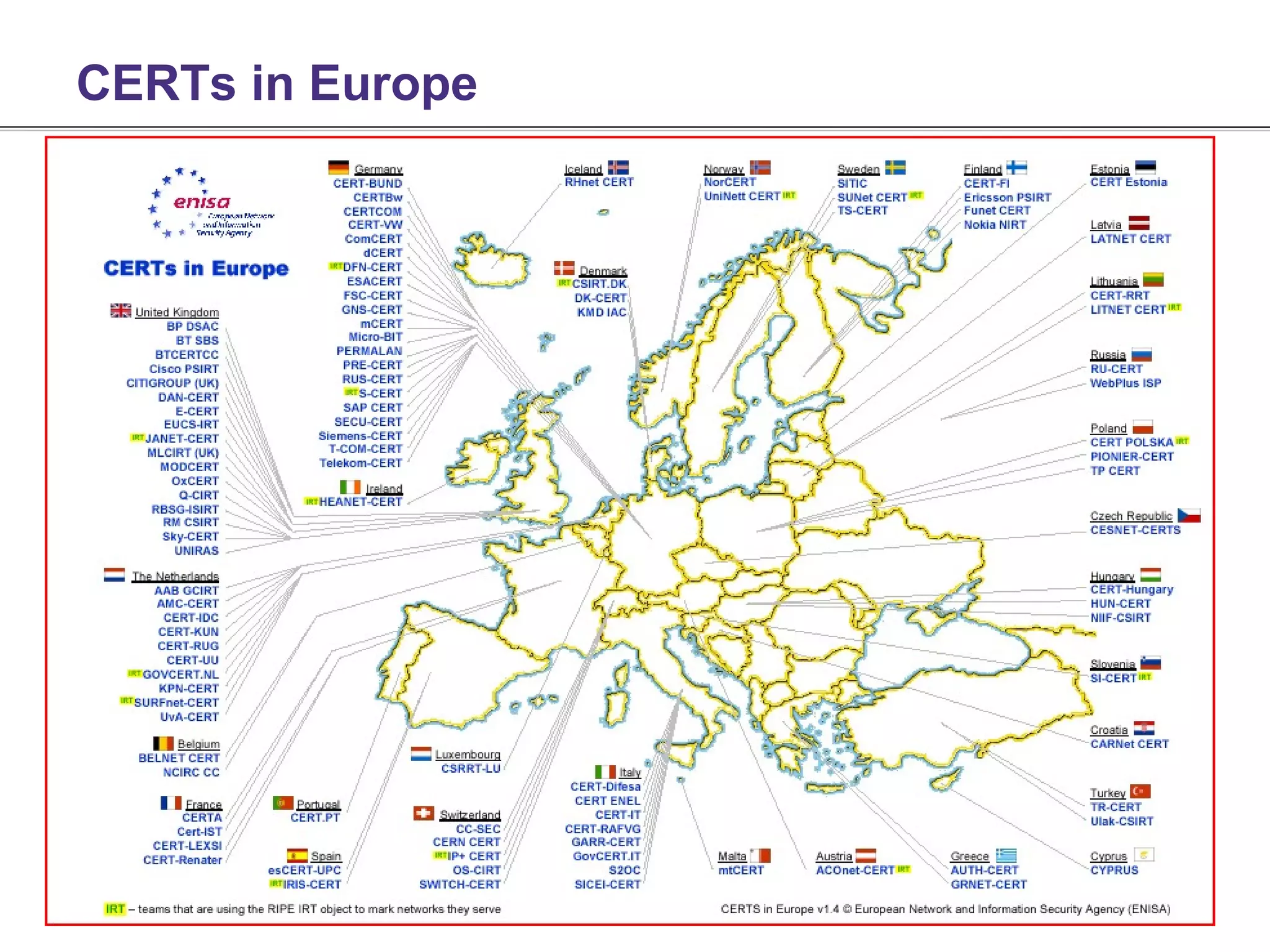
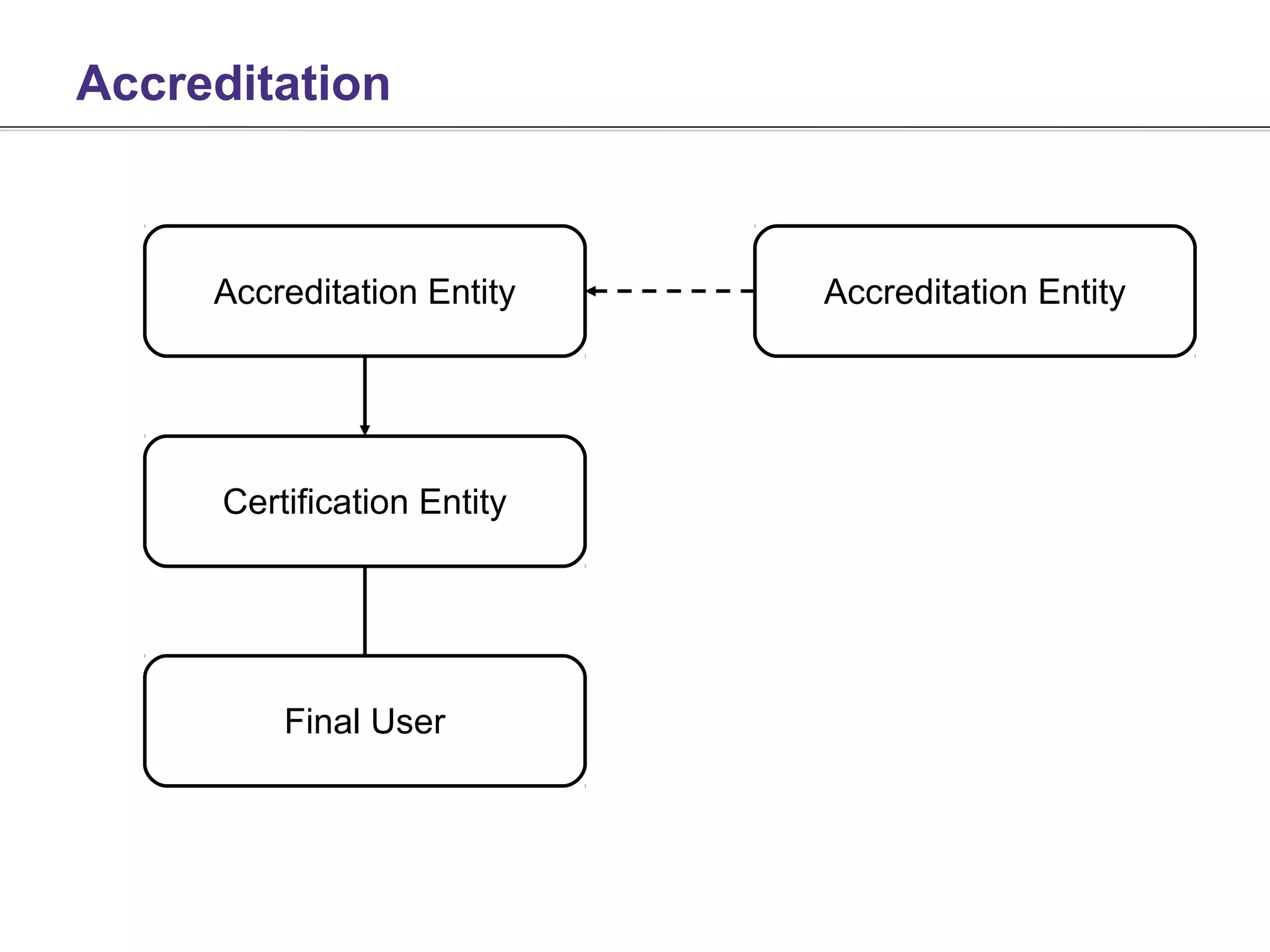
This document discusses Computer Emergency Response Teams (CERTs) and the process of CERT certification. It describes what a CERT is and the types of services they provide, including reactive services like incident handling, and proactive services like security audits. The document outlines some of the challenges with certification, noting that certification alone does not guarantee performance and that poor performers can damage the reputation of certificate holders. It emphasizes that accreditation is also necessary to verify factors like a team's competence and procedures. The document provides information on the Trusted Introducer program which facilitates accreditation and information sharing between European CERTs.