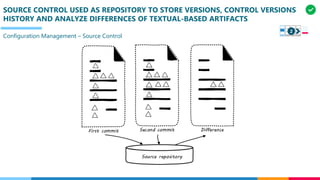
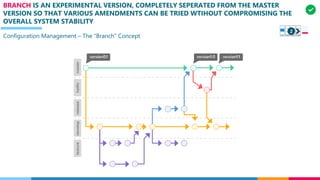
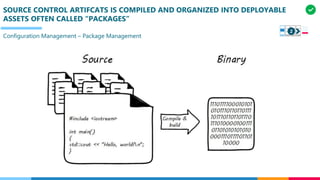
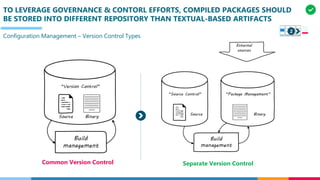
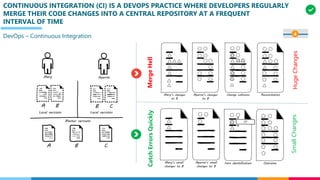
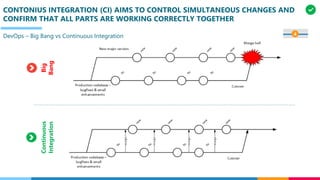
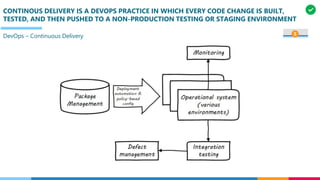
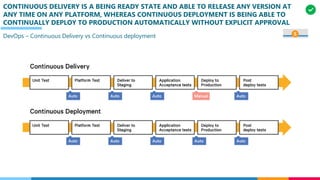
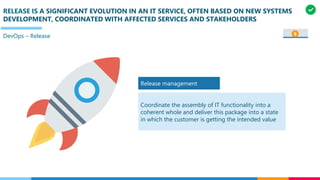
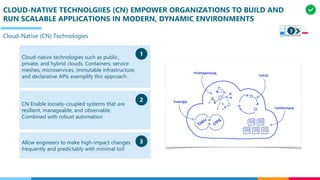
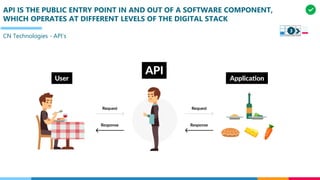
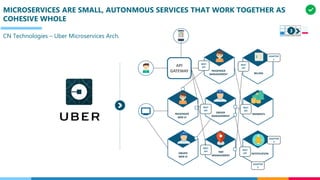
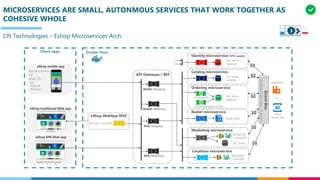
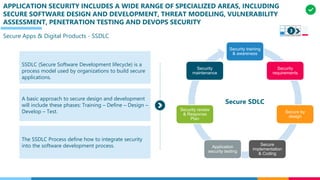
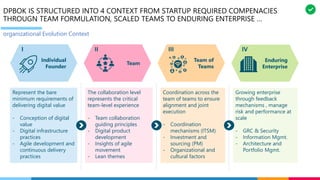
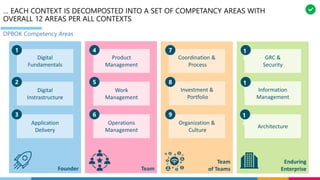
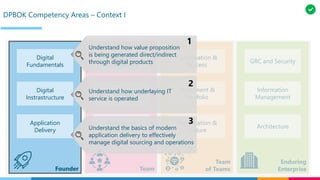
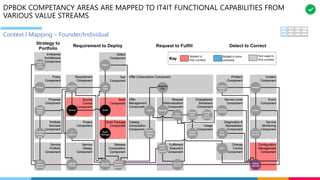
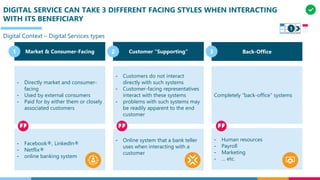
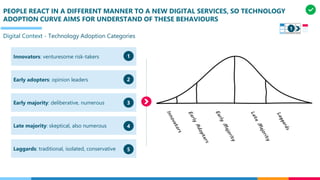
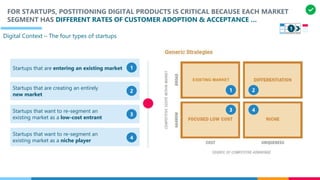
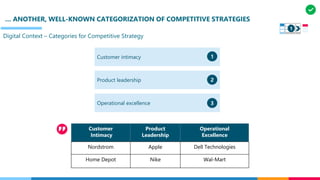
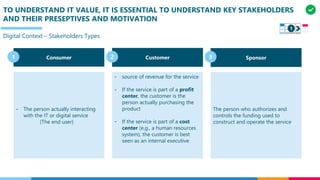
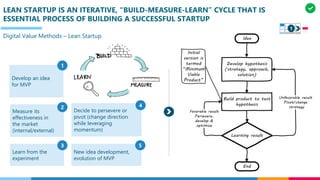
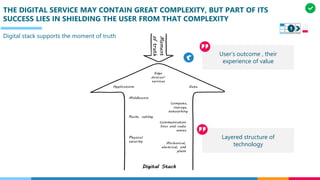
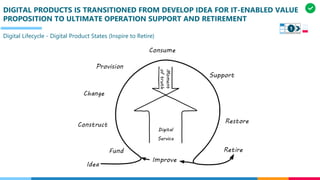
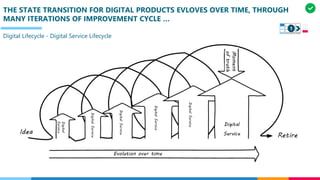
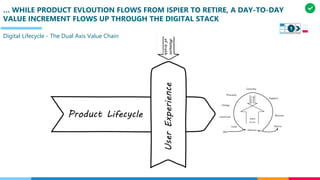
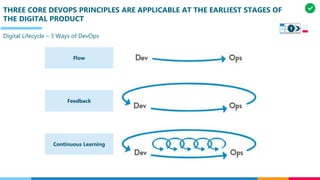
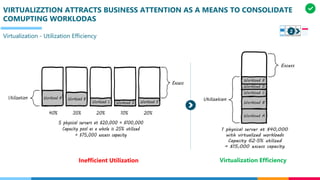
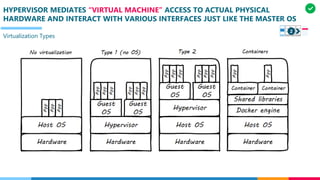
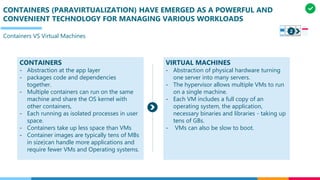
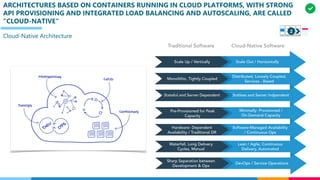
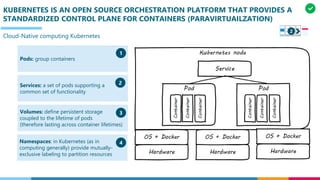
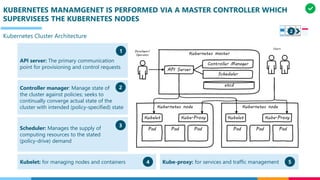
The document discusses the structure and competency areas of the Digital and Business Operations Body of Knowledge (DPBOK). It describes how DPBOK is structured into four contexts representing different stages of organizational evolution: individual/founder, team, team of teams, and enduring enterprise. Each context contains competency areas that decompose the skills needed. Context I focuses on competencies for an individual/founder and includes digital fundamentals, digital infrastructure, and application delivery. Digital fundamentals covers understanding digital value methods, contexts and lifecycles. Digital infrastructure discusses IT components, virtualization, containers, cloud-native architectures and configuration management. Application delivery outlines agile development practices and application architectures like microservices and APIs.








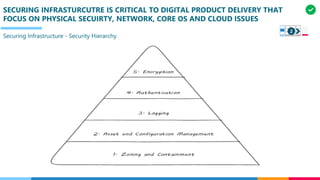
![THERE ARE 3 MAJOR PHSICAL ASPECTS OF IT INFRASTURCUTER RELEVANT TO THE
DIGITAL PRACTITIONER
Definition: “The resource that
performs the rapid, clock-driven
digital logic that transforms data
inputs to outputs”
Data processing or state change:
Move data somewhere, operate it,
return to original location required
energy and bound up to physical
reality and laws of thermodynamics
[Compute processing is not free]
We must pay for computing , even
running the simplest calculation has
physical and economic cost
Definition: “The act of computation
that is bound up with the concept of
state”
No Need to concerned with physical
infra. used for storing data:
Storage increasingly is experienced as
a virtual resource, accessed through
executing programmed logic on cloud
platforms
Storage has different levels
of speed and accessibility:
- On-chip registers and cache
- RAM,
- Online mass storage [disk]
- Offline mass storage [tape]
Definition: “The basic concern of
Networking is to transmit data (or
information) from one location to
another
Developer uses programmatic tools to
define expected information
transmission not concerned with the
network technologies serving their
needs
Hierarchy of networking:
- Intra-chip pathways
- Motherboard and backplane
circuits
- Local area networks
- Wide area networks
- Backbone networks
Compute NetworkStorage
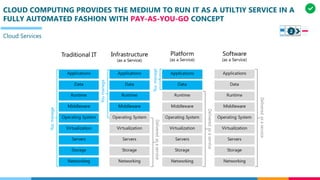
Digital infrastructure – IT Infrastructure components
2](https://image.slidesharecdn.com/dpbok-contexti-201128123317/85/Dpbok-context-i-28-320.jpg)

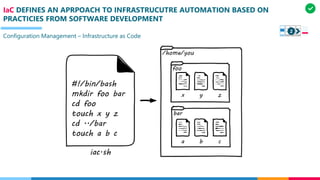
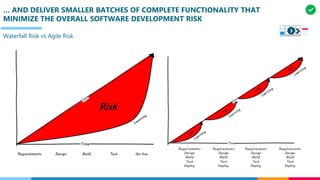
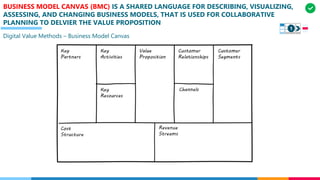
![CM CONSISTS OF VC WHICH MANAGE THE STATE OF ARTIFACTS AND D&O WHICH MANAGE
ARTIFACTS COMBINATION WITH REQUIRED RESORUCES TO ENSURE VALUE DELIVERY
Configuration Management
[CM]
[VC]
[D&O]
2](https://image.slidesharecdn.com/dpbok-contexti-201128123317/85/Dpbok-context-i-38-320.jpg)