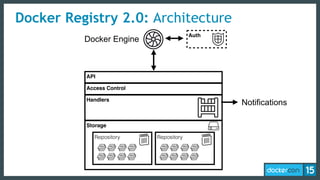
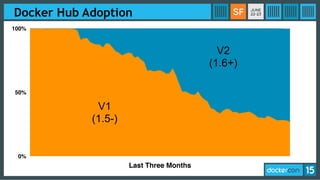
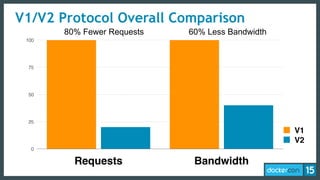
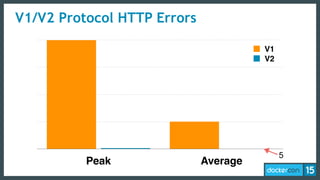
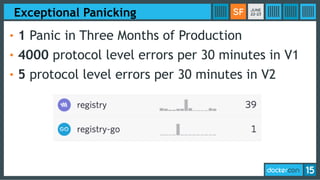
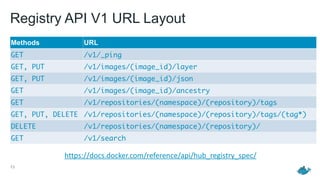
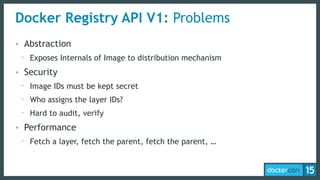
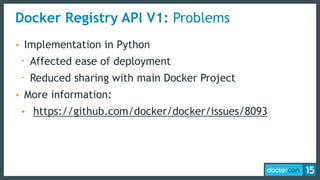
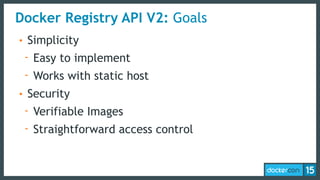
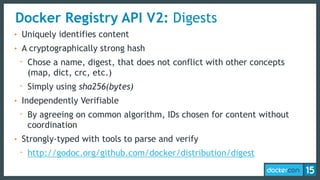
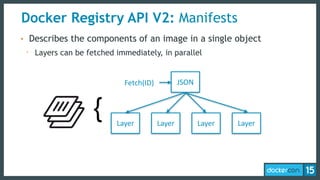
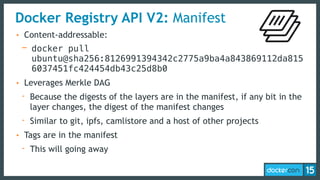
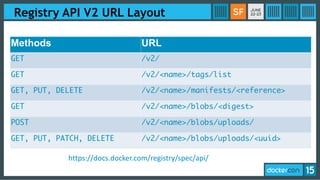
This document discusses Docker Registry API V2, a new model for image distribution that addresses limitations in the previous V1 API. Key changes include making layers content-addressable using cryptographic digests for identification and verification. Images are now described by manifests containing layer digests. The registry stores content in repositories and no longer exposes internal image details. Early adoption shows V2 providing significantly better performance than V1 with 80% fewer requests and 60% less bandwidth used. Future goals include improving documentation, adding features like pull-through caching, and developing the Docker distribution components to provide a foundation for more advanced distribution models.












![Docker Registry API V2: Manifests
{
"name": <name>,
"tag": <tag>,
"fsLayers": [
{
"blobSum": <digest>
},
...
]
],
"history": [<v1 image json>, ... ]
}](https://image.slidesharecdn.com/distributiondockercon2015final-150629160534-lva1-app6891/85/Docker-Registry-V2-22-320.jpg)




![–Earl Milford
“[A registry] should be
neither seen nor heard. ”](https://image.slidesharecdn.com/distributiondockercon2015final-150629160534-lva1-app6891/85/Docker-Registry-V2-29-320.jpg)