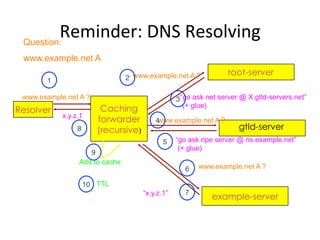
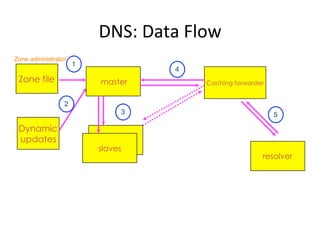
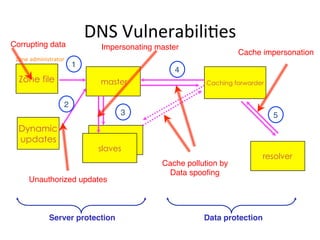
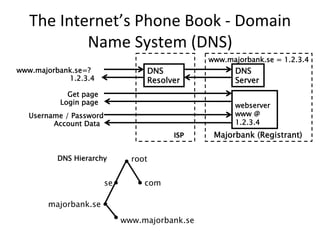
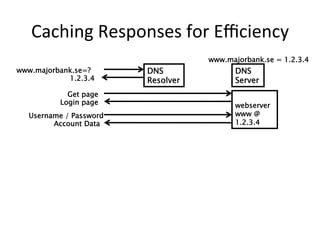
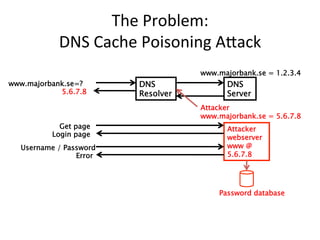
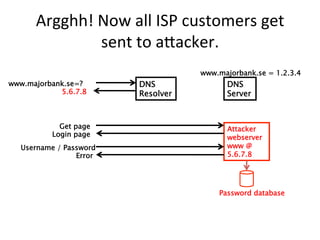
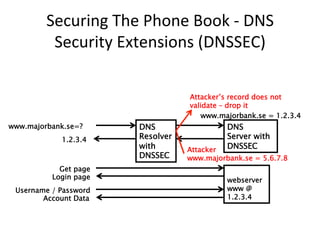
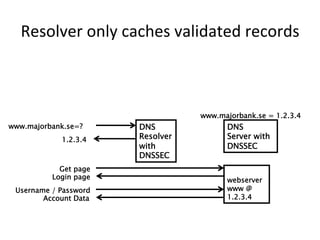
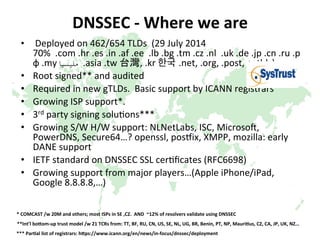
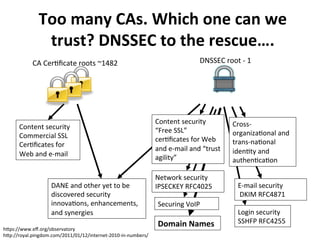
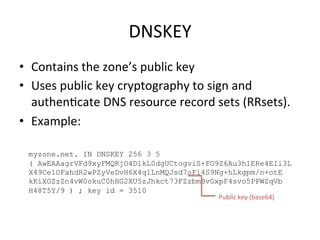
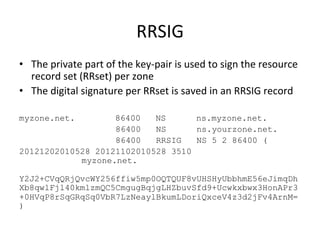
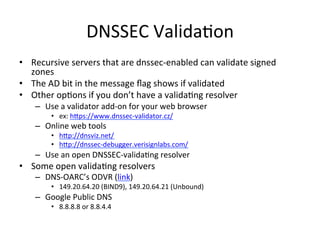
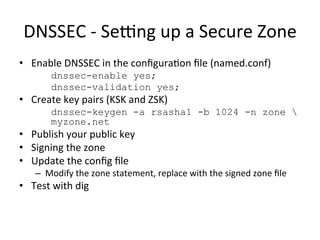
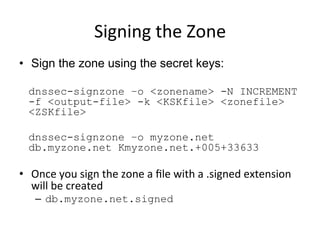
This document provides an overview of DNSSEC (Domain Name System Security Extensions). It discusses how DNSSEC introduces digital signatures to cryptographically protect DNS data and prevent man-in-the-middle attacks. It also describes some common DNS record types used in DNSSEC like DNSKEY, RRSIG, and DS. The document notes that while DNSSEC deployment has increased in top-level domains and root servers, adoption remains low at the second-level domain level, and more work is still needed for full deployment.