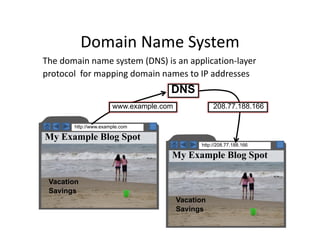
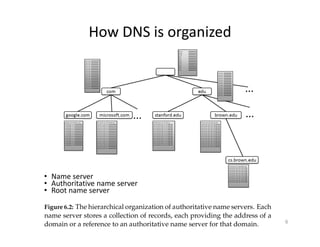
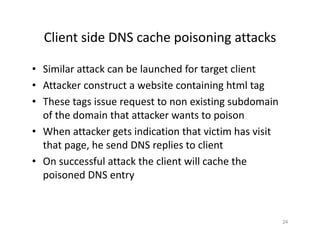
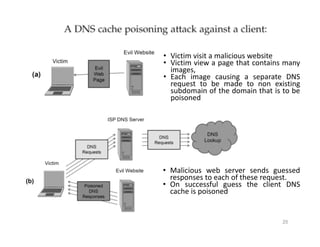
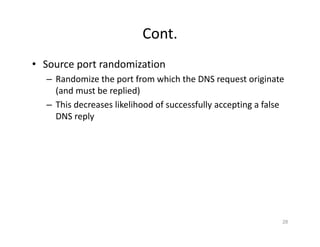
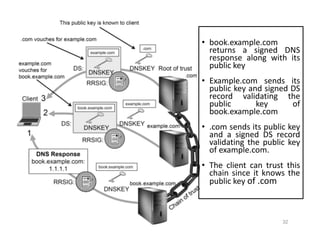
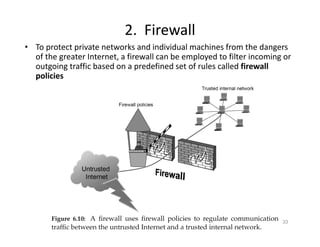
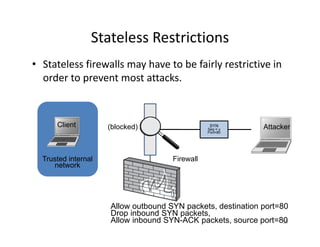
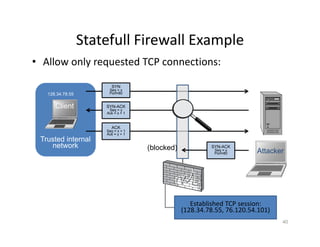
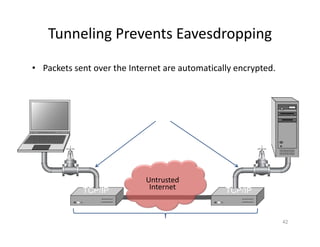
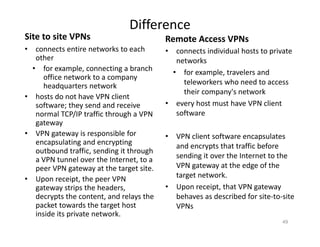
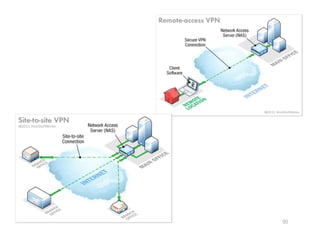
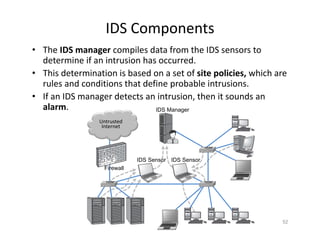
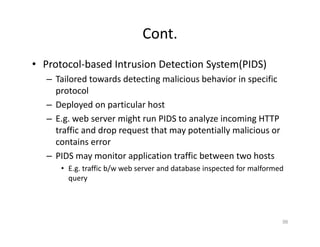
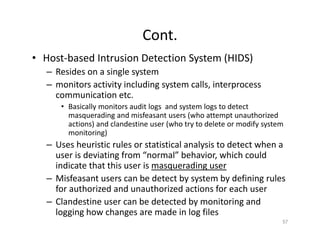
The document outlines various aspects of the Domain Name System (DNS) and its security challenges, including DNS cache poisoning and attacks like pharming and phishing. It discusses how DNS queries work, the organization of DNS, and methods for securing DNS through the use of DNSSEC and firewalls. The document also explains different firewall types, tunneling protocols, and virtual private networking (VPN) technologies to enhance network security.









































![IDS Data ‐ Examples
• If Alice write 104 Kilobyte of data to file dog.exe
[Alice, dog.exe, write, “no error”, 104KB,
20100304113451]
• If a client 128.72.201.120 attempts to initiate an
HTTP session with a server 201.33.42.108
[128.72.201.120, 201.33.42.108, HTTP, 0.02 CPU
sec, 20100304114022]
• However exact format would be determine by IDS
designer
67](https://image.slidesharecdn.com/networksecurityii-complete-240526083247-54ee0ba3/85/Information-Security-Network-Security-Cache-Poisoning-67-320.jpg)