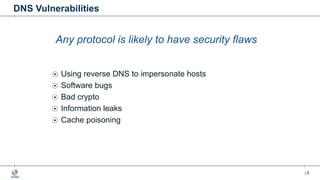
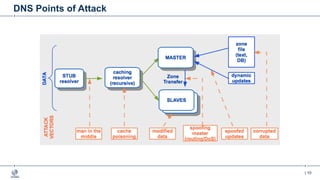
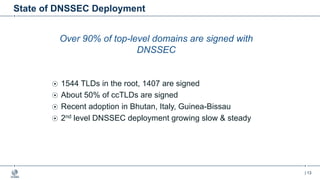
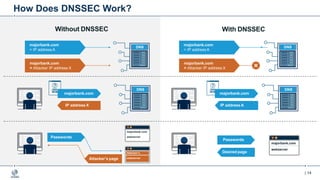
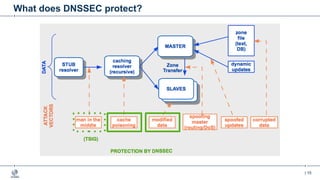
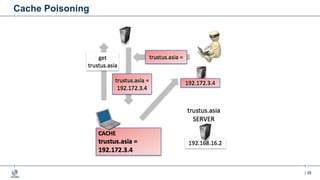
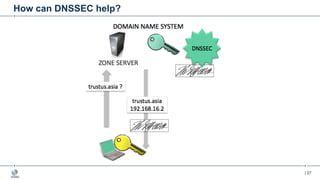
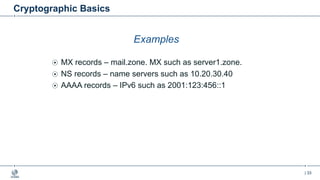
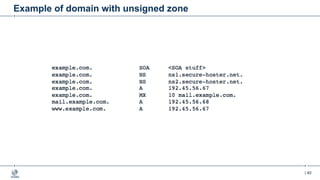
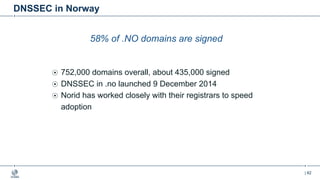
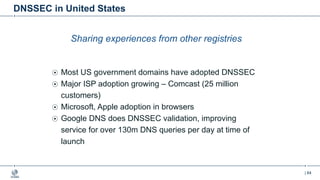
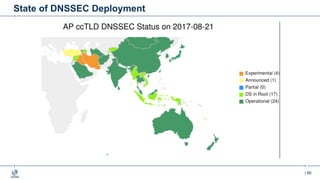
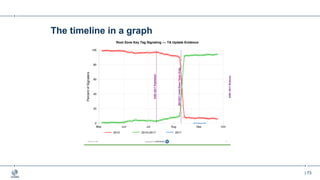
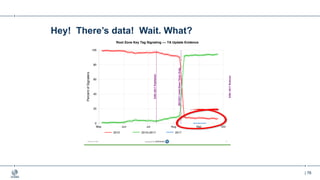
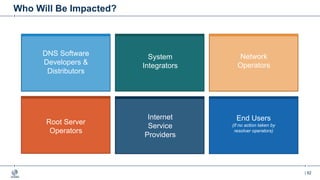
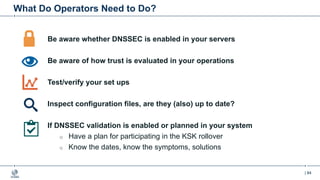
This document provides an overview of DNSSEC (Domain Name System Security Extensions). It begins with some background on the history and vulnerabilities of DNS that led to the development of DNSSEC. It then explains how DNSSEC works by digitally signing DNS data to authenticate its source and ensure its integrity. The document discusses the state of DNSSEC deployment globally and in various top-level domains and country code top-level domains. It also provides examples of DNSSEC implementation strategies used by early adopter registries such as Sweden, the Netherlands, Czechia, and Norway.